 Cybercriminals are taking to more advanced functionality than traditional VBA scripting to both execute complex malicious actions via Excel and to obfuscate their true intention - phishing attacks.
Cybercriminals are taking to more advanced functionality than traditional VBA scripting to both execute complex malicious actions via Excel and to obfuscate their true intention - phishing attacks.
If I had a nickel for every time I heard about a malware attack that used macros embedded in an Office document, I’d have quite a few nickels by now. It’s an age-old tactic that, to this day, remains an effective means to execute malicious code.
But new data from HP Wolf Security’s Threat Insights Report Q4 2021, just released this month, shows a newer tactic very quickly growing in popularity in the form of an Excel Add-In. These add-ins allow individuals to create custom functions using the Excel JavaScript API that can be used – in most cases – across Excel on Windows, Mac, and within a web browser, making this potentially very dangerous.
According to Wolf Security, they’ve seen this technique used in malware we’ve covered here in our blog, including Dridex, IcedID, BazaLoader, Agent Tesla, Raccoon Stealer, Formbook and Bitrat. And in Q4 of last year (the timeframe covered by their latest report), the presence of XLL files increased 588% over Q3.
Emails sent to potential victims include a malicious XLL file as the attachment. Clicking it launches Excel and prompts the user to install and activate the add-in.
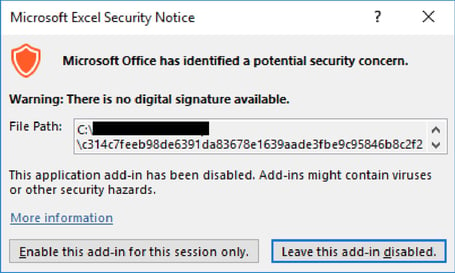
Source: Wolf Security
Wolf Security include the following three recommendations to help address the threat potential of XLL files:
- Configure your email gateway to block inbound emails containing XLL attachments
- Configure Microsoft Excel only to permit add-ins signed by trusted publishers
- Configure Microsoft Excel to disable proprietary add-ins entirely
Additionally, Security Awareness Training can play a valuable role in stopping these kinds of attacks by elevating your user’s vigilance around not engaging with suspicious and (in the case of XLL files) unusual email content. If it’s not expected, assume it’s malicious until proven innocent.
 Here's how it works:
Here's how it works:




