 Uncovered by the research team at cloud protection vendor Intezer, this new phishing campaign seeks to steal information and position each victim as the foothold to spear phish additional companies.
Uncovered by the research team at cloud protection vendor Intezer, this new phishing campaign seeks to steal information and position each victim as the foothold to spear phish additional companies.
I love seeing the big picture; it let’s me know my educated guesses about who, why, and what’s next based on attack after attack I’ve seen are all pretty well-founded. In the case of this latest attack documented by security researchers at Intezer, we get to see the entire picture from start to finish. And it appears the Energy sector (and a few related industries) have been the target of a phishing campaign spanning over one year.
The campaign uses some traditional tactics we’ve all seen before to phish the user into taking the bait. Emails appear to be legitimate correspondence, usually related to requests for quotations (RFQ), contracts, and references to real projects related to the business of the victim company. An example from Intezer is below:
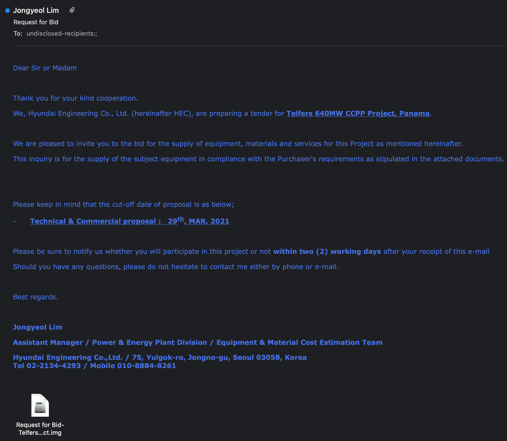
Source: Intezer
Sender addresses use lookalike domains, forged email headers, and spoofed email addresses of real individuals to convince potential victims into engaging with malicious attachments – usually IMG, ISO, or CAB files containing .NET-based malware including Formbook and Agent Tesla, which can steal banking info, credentials, and more, as well as provide remote access to threat actors.
And, because much of the malware this campaign uses is fileless – meaning, it installs directly to memory, many AV solutions miss this. So, it’s necessary to ensure the human element of your security strategy is fully engaged via Security Awareness Training so they can see through the spoofing tactics and immediately know something is off before they even begin to think about clicking on that link or attachment.
 Here's how it works:
Here's how it works:




