.jpg?width=400&name=iStock-1299483011%20(1).jpg) Disguised as an invoice, cybercriminals use a Windows-supported disk image to obfuscate malware from email gateways and security scanners. The question is how viable will it be?
Disguised as an invoice, cybercriminals use a Windows-supported disk image to obfuscate malware from email gateways and security scanners. The question is how viable will it be?
The bad guys are in constant need to find ways to evolve their art as the good guys improve their security solutions to respond to current attack methods. Historically, we’ve seen a number of image files used including virtual hard disks and ZIP files, as well as .ISO, .IMG, and .DAA files. But, as security solutions get wise and use AI to simply determine “has this user EVER received an image file???” to flag an email, the bad guys need to look for a new format.
According to a recent article from security vendor Trustwave, they’ve spotted a WIM (Windows Imaging Format) file disguised as an invoice or consignment note in the wild.
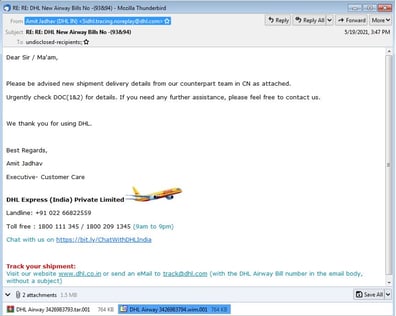
Source: Trustwave
The WIM format is one developed by Microsoft. The WIM file contains a single executable – the Agent Tesla malware. Because Windows 10 and above support this filetype, it’s possible that it can be directly opened by the recipient.
This one seems a little out there, as the user experience to detonate this malware involves first extracting the WIM file’s contents (and “extracting” is a very foreign concept to most users). So, it seems the bad guys are relying on the recipients unwitting-ness to simply click the affirmative buttons blindly to install the malware.
Users can easily be educated about such tactics using continual Security Awareness Training that keeps them updated on the latest types of scams, phishing methods, and more.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




