 In Short:
In Short:
The Necurs botnet is one of the world's largest botnets with more than 6 million zombie machines tied into it. It's run by Russian organized cybercrime and responsible for millions of dollars in losses tied to the Dridex banking Trojan and more recently the Locky ransomware strain.
Background
The internet criminal ecosystem is complex and interrelated, with the players often engaged in "co-opetition". Botnets generally spread malware via email blasts while Exploit Kits are the tools behind a variety of malvertising and so-called "drive-by downloads."
A large underground infrastructure -- read botnets-- has been built to drive traffic to websites compromised with Exploit Kits. Internet criminals can rent time on botnets or rent access to compromised sites. Botnets are being improved constantly and have sophisticated command & control (C&C) architectures.
Simultaneously, ransomware strains have their own developers. Some strains have their own C&C infrastructure and are rented "as a service". Many ransomware campaigns make use of botnets and exploit kits as their primary distribution methods.
Technical Details
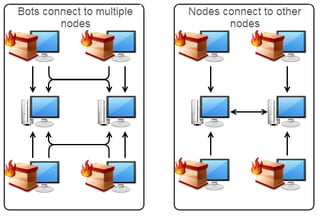 Necurs creates its "zombies " by infecting them with the Necurs rootkit. It is being used by bad guys for a variety of criminal purposes. Botnets are mostly used to evade spam filters and send phishing attacks or launching distributed denial of service (DDoS) attacks. Necurs is a sophisticated peer-to-peer (P2P) botnet.
Necurs creates its "zombies " by infecting them with the Necurs rootkit. It is being used by bad guys for a variety of criminal purposes. Botnets are mostly used to evade spam filters and send phishing attacks or launching distributed denial of service (DDoS) attacks. Necurs is a sophisticated peer-to-peer (P2P) botnet.
To prevent detection, P2P botnets do not need a lot of traffic between infected computers and C&C servers. Necurs employs a domain generation algorithm (DGA) that allows infected computers to find a new C&C when the active one goes down, using an architecture of "nodes" and "workers" where nodes function as C&C servers.
How much is this criminal business model making?
The Locky ransomware strain came into the limelight for its $17,000 payday when it encrypted and held for ransom data on more than 250 computers of the Hollywood Presbyterian Medical Center in February 2016. Dridex, for its part, has netted tens of millions of dollars from victims via banking Trojans infecting PCs.
The Necurs botnet, spewing Dridex and Locky has an incredibly successful business formula netting between $100,000 and $200,000 a day in criminal activity. The developers behind this botnet are the best in the world. They are furiously innovating their code, and regularly come up with new features and evasion techniques.
Ransomware Hostage Rescue Manual
Get the most complete Ransomware Manual packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware.
If you do not like to click on buttons with redirects, cut/paste this link in your browser:
https://info.knowbe4.com/ransomware-hostage-rescue-manual-0





