Security Researchers at Forcepoint discovered that a Russian hacking forum on the dark web is selling the Cerber ransomware as a RaaS (Ransom-as-a-service). This is a new form since Cerber has been distributed via exploit kits or email using macro-enabled Word document files, however, this is the first time WSFs (Windows Script Files) have been used for this purpose.
WSFs are executable with the Windows wscript.exe utility and can contain scripts from any Windows Script compatible scripting engine in a single file. After successful execution of the file, the Cerber crypto-ransomware will be downloaded on the victim’s system. They are likely using the uncommon WSF to trick AV solutions that rely on machine learning and/or heuristics.
The hackers are making the victims download Cerber in two methods; first is a double-zipped file with a WSF inside attached to a phishing email and the other is an unsubscribe link located at the bottom of the message, which is also linking to the same ZIP file.
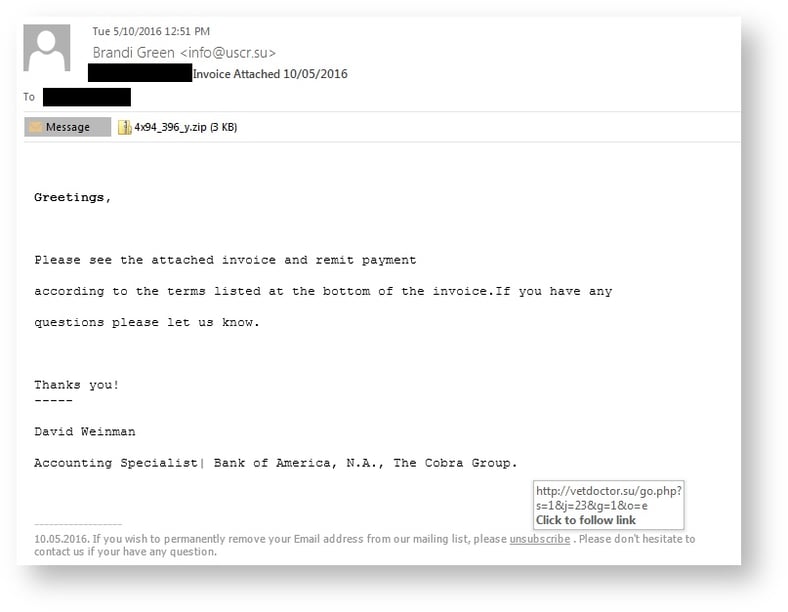
Since the nature (invoice -related subject line, genuine-looking content, and an unsubscribe link) of the double-zipped file with the WSF, heuristics-reliant security solutions might be bypassed due to the uncommon use of the WSF.
Cerber has the encryption capability without communicating with associated command and control (C&C) servers, however, security researcher at Forcepoint Nicholas Griffin wrote that Forcepoint had discovered weaknesses in the encryption implementation, which could be used to partially decrypt the files. He also made this statement:
“Although the number of observed victims is low, the majority currently appear to be within the UK. However, this is likely to change over time.”
Time and time again we've seen cybercriminals pilot new campaigns in the UK, work out all the bugs then launch a full attack here in the US.
Get the most informative and complete ransomware hostage rescue manual. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.

This was cross-posted from DeepDotWeb.




