 It’s nearly impossible to find an Internet scam or phishing email that doesn’t involve a malicious Uniform Resource Locator (URL) link of some type. The link either directs the user to a malicious web page or contains malicious instructions itself. The goal is to execute malicious code or instructions in the user’s browser. This article will cover some of the most common malicious URL tricks and defenses against them.
It’s nearly impossible to find an Internet scam or phishing email that doesn’t involve a malicious Uniform Resource Locator (URL) link of some type. The link either directs the user to a malicious web page or contains malicious instructions itself. The goal is to execute malicious code or instructions in the user’s browser. This article will cover some of the most common malicious URL tricks and defenses against them.
Common Rogue URL Tricks
I’ve come up with 12 different types of URL tricks that scammers and phishers use to trick users into clicking on malicious links. They are:
- Look-alike Domains
- Domain Mismatches
- URL Shortening
- URL Character Encoding
- Homograph Attacks
- Overly Long URLs
- Cross-Site Scripting
- Malicious Redirection
- Fake 404 Pages
- Fake File Attachment Images
- Rogue Digital Certificates
- Password Hash Theft
Look-alike Domains
One of the most common URL tricks is when a phisher uses a look-a-like domain which contains the name of some other well-known brand in order to fraudulently gain trust of possible victims. Here are some examples below:
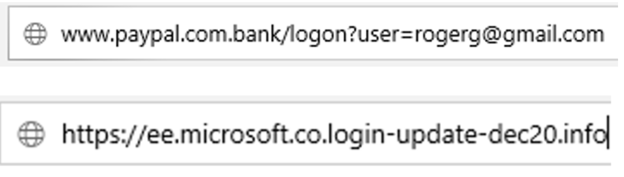
Domain Mismatches
Domain mismatches are signs of maliciousness rather than a “trick.” In this case, the phisher sends an email purportedly coming from a well-known brand, but that contains multiple domain names, none of which are related to the claimed brand’s real domain name. Here’s an example below:
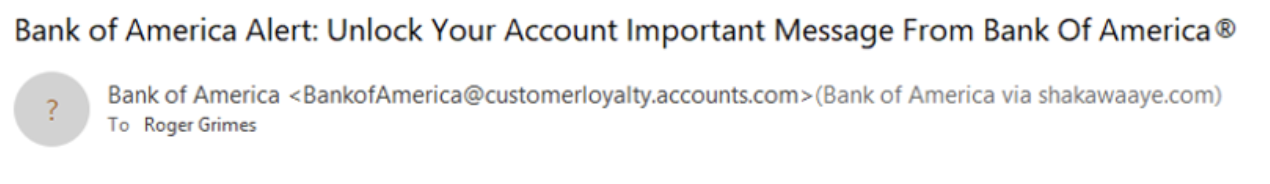
URL Shortening
Many hackers use URL shortening services, which convert their longer malicious URLs into innocuous, shorter URLs. These adjusted URLs make it harder for a potential victim to investigate. Here’s an example below:
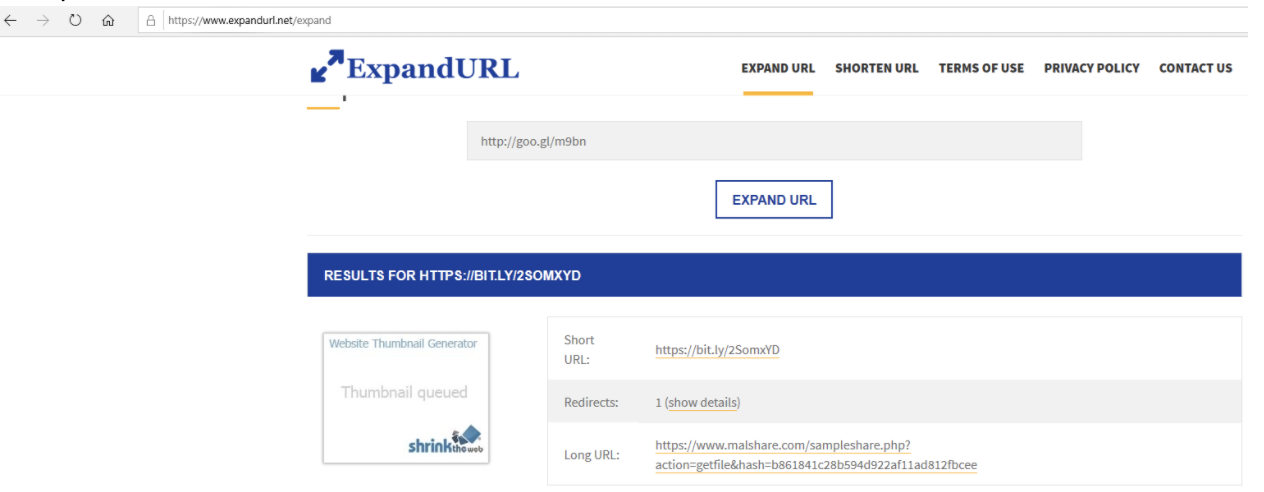
In this case, the shortened URL of “https://bit.ly/2SomxYD” expanded into a malware program stored at a malware website under the domain of “www.malshare.com.”
URL Character Encoding
Internet URLs can be encoded using several different methods. The most common method is known as percent “escaping.” This is when each ASCII character is replaced with its hexadecimal digit counterpart followed by a % sign. Here’s an example below:
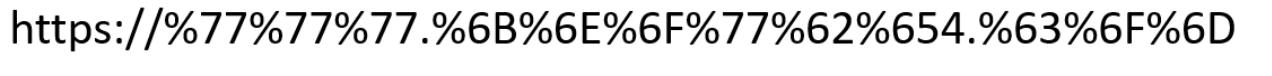
The example above is simply the URL, “https://www.knowbe4.com,” encoded.
Homograph Attacks
Homographic attacks use other languages' characters that look like another language’s characters to create new domains. The new domains look like a well-known brand, but are really entirely other domains in a completely different language. For example, the Unicode Latin "a" (U+0061 hex) and Cyrillic "а" (U+0430 hex) may look the same in a browser. Here’s a graphical example below:
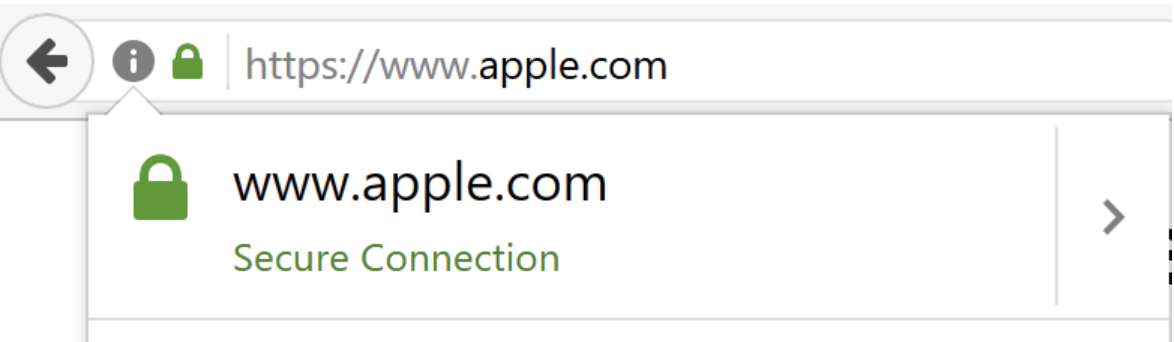
The URL above looks like English www.apple.com, but it is really another Cyrillic domain name with the same look-a-like characters. Once clicked, it redirects the user to another domain altogether (as shown below).
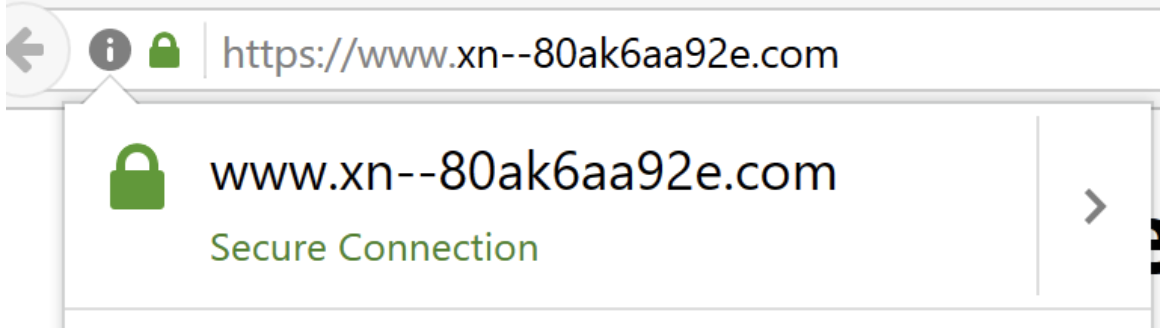
Xudong Zheng has a more detailed discussion of phishing with Unicode domains.
Overly Long URLs
Some scammers will use overly long URLs, with hundreds of random characters in order to “overflow” the screen when a user hovers over the URL link to investigate. The idea is that there will be so much information that the user might just give up on investigation and click on the link prematurely. Here’s an example below:

Cross-Site Scripting
Cross-site scripting (XSS) is an attack method where HTML code meant to be “display only” or executed on a server gets manipulated into executing code on client instead. XSS code can either be directly included in a URL or, more commonly, the URL redirects the user to a malicious web page that then tries to execute the XSS. Here is an example below:

Malicious Redirection
Some otherwise innocent websites contain coding that allows their URL to be misused by scammers who use the URL to redirect potential victims to other more malicious locations. In this case, a user investigating an involved URL would see and trust the originating domain, not knowing that it is being used to automatically redirect them somewhere else. Here is an example below.

Fake 404 Pages
On websites, when someone ask for a web page or object that does not exist, they are supposed to get a “404 Error” message that tells them they asked for something that does not exist (similar to the example below):
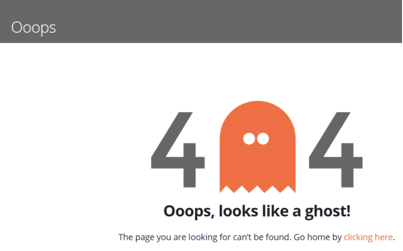
Hackers will break into an otherwise innocent website and change the default 404 error message to be a redirect to a malicious website. Then, they will send out millions of phishing emails pointing to a non-existent object or page on the website, which ends up redirecting the user to an even more malicious website (such as the fake Microsoft Office 365 login page example below):
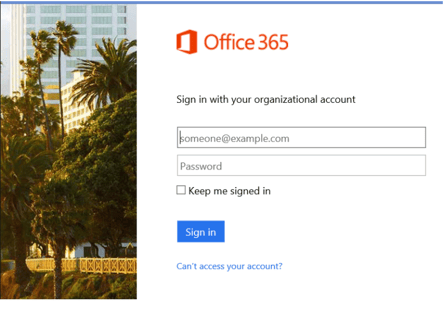
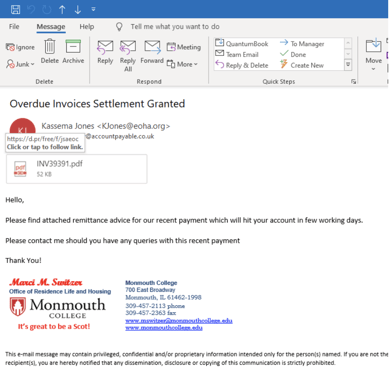
Fake File Attachment Images
Something relatively new we are seeing over the last year is the use of fake file attachments, which are really images with links to other objects hosted on malicious websites. See an example below:
Rogue Digital Certificates
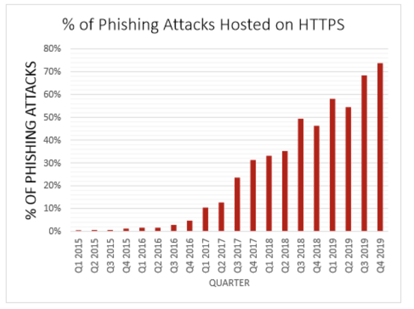
Most people think a trusted TLS digital certificate means a site is a “good” site and won’t harm them. This is far from the truth. A trusted TLS digital certificate means the website’s hostname and DNS path are valid. It does not mean a website is a legitimate website that can be trusted. The Anti-Phishing Working Group said that over 70% of malicious phishing websites had a trusted digital certificate in 2019. Many of these certificates are from free certification authorities, like Let’s Encrypt, which do not expend much effort to determine the trustworthiness of someone they issue a certificate to.
Password Hash Theft
If a user can be tricked into clicking on a link, there is a chance their browser or email client can be tricked into sending the hash of their password to a hacker. It occurs like this:
- Hacker creates/has a malicious web server on the Internet
- Hacker creates a malicious URL address that links to object on web server
- Sends link to victim (e.g., using email, etc.)
- Victim clicks on URL link
- Email program/browser attempts to retrieve object
- Server requires authenticated login
- Email program/browser attempts authenticated login
- Sends remote login attempt, from which attacker can derive password hash
How the trick is done and what the malicious URL looks like both depend on the hacker and the available, unpatched vulnerabilities the hacker is trying to take advantage of. Kevin Mitnick, KnowBe4’s Chief Hacking Officer has a demo with an example of this password hashing trick. I additionally wrote a more detailed discussion of the trick with the article, “I Can Get and Hack Your Password Hashes From Email,”.
The examples above are just 12 examples from what seems like an endless list of hacker tips involving rogue URLs.
Defenses
Defenses come down to your best defense in depth strategy, including what I call the 3 x 3 Pillars of Security Defense (see the figure below).
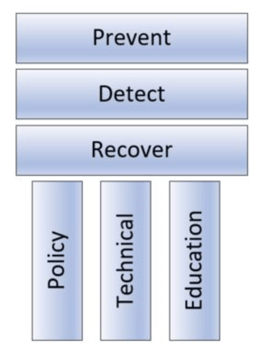
All organizations should have three security control objectives:
- Prevent
- Detect
- Recover
Organizations want to prevent bad things from happening to their environment. If bad things get past the preventative controls, they should get early warning and detection of those things to mitigate damage. Finally, they have to recover from the attack and figure out how to prevent it next time. Each security control needs to have policy, technical controls, and education around it.
Perimeter Defenses
Specifically, to mitigate threats from rogue URLs, perimeter defenses should include:
- Anti-Malware Defenses
- Content Filtering
- Reputation Services
- Make sure Defenses Decode Encoding Before Inspecting
- Make sure Defenses Expand Short URLs
- Keep Up to Date on Latest Malicious URL Trends
Personal Defenses
To mitigate threats from rogue URLs for each user:
- Provide Security Awareness Training
- Teach All Users to Always Hover Before They Click
- Stay Fully and Timely Patched
- Teach Users to Not Knowingly Allow Code to Execute
- Teach Users Not to Download Unexpected Files
- Teach Users to Investigate or Ignore Suspicious URLs
If users see a suspicious URL, they should be taught to report it to IT/advanced users who:
- Investigate Further; or
- Execute Suspicious URLs in a Safe, Isolated, Virtual Machine; or
- Submit Suspicious URLs to a Malware Inspection Service
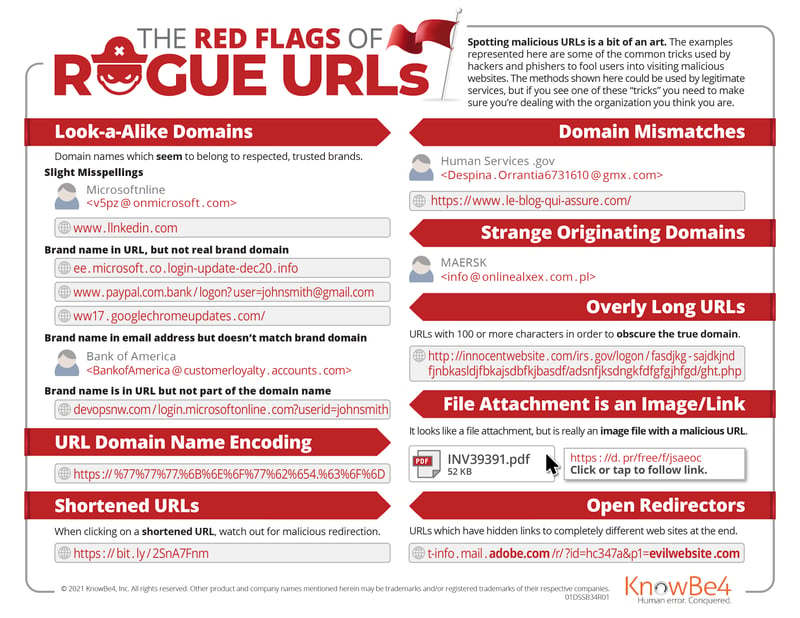
The more you and your co-workers know about malicious URLs, the easier they can avoid them. I hope this short paper has been educational and useful. If you are interested in learning and/or hearing more details about rogue URLs, see my Combatting Rogue URL Tricks webinar. You can also download KnowBe4’s Red Flags of Rogue URLs PDF document, which is a great, quick handout for teaching your co-workers about some malicious URL tricks:
 Real-life examples of advanced attacks using rogue digital certificates, homograph attacks and more
Real-life examples of advanced attacks using rogue digital certificates, homograph attacks and more




