 Much of the world, or at least the United States, is coalescing around the NIST Cybersecurity Framework. It’s a pretty good one to follow out of the many dozens that have been proposed over the decades. My only major problem is that it doesn’t tell you which controls matter more than others. For example, since social engineering and phishing account for 70% to 90% of all malicious breaches and unpatched software accounts for 20% to 40% of attacks, I wish the framework’s recommendations spent far more time on those two issues and related controls.
Much of the world, or at least the United States, is coalescing around the NIST Cybersecurity Framework. It’s a pretty good one to follow out of the many dozens that have been proposed over the decades. My only major problem is that it doesn’t tell you which controls matter more than others. For example, since social engineering and phishing account for 70% to 90% of all malicious breaches and unpatched software accounts for 20% to 40% of attacks, I wish the framework’s recommendations spent far more time on those two issues and related controls.
At the very least, every cybersecurity plan should first model the most likely risks and then map the proposed and implemented controls against the most likely threats first and best. It’s insane that the majority of cybersecurity defenses essentially put the cart before the horse and just start mapping out controls without any real consideration of what the actual risks are. But I digress…and I wrote a whole book on the subject, A Data-Driven Computer Defense.
Even if the NIST Cybersecurity Framework isn’t perfect, it’s nice to get some general agreement about which framework to model our own security policies around. But in order to think about what I need to do and propose, I like to consolidate as much as possible. The NIST Cybersecurity Framework has five pillars – Identify, Protect, Detect, Respond, and Recover. That’s too many for me to remember and map to.
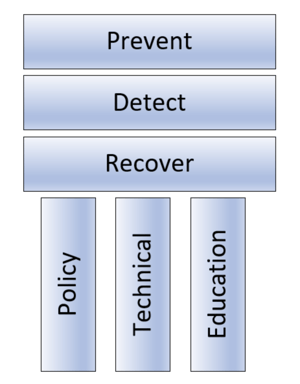
Three Security Defense Pillars
When I think about computer security defenses, I have three control objectives in my head:
- Prevent
- Detect
- Recover
I want to prevent bad things from happening to an environment I manage. If bad things get past my preventative controls, I want early warning and detection of those things to mitigate damage. And I have to recover from the attack and figure out how to prevent it next time. Everything in my planning looks at computer security using these three pillars of security defenses.
When I learn of a risk or threat, I first ask myself, what is the true severity of the risk? One-quarter to one-third of all risks are ranked by someone as High/Critical. Considering that we have well over ten thousand different risks each year, that equates to thousands of supposedly high-risk threats we need to respond to. And it’s just not true. The average organization gets threats that try to exploit one to two dozen different types of risks each year. The most likely ones are the ones you need to mitigate first and best.
I’ll give you an example, the Meltdown and Spectre chip vulnerabilities are likely the most threatening vulnerabilities to be announced in decades. Without patching those vulnerabilities, any involved computer (and most computers were impacted) could not only not stop the attacks, but not even get an event log record that a successful attack occurred. After the announcement of Meltdown and Spectre in 2017, over a hundred demonstration malware programs were created and released to show how easy it would be to worm and militarize those vulnerabilities. There isn’t a vulnerability report that won’t list them as among the highest risk threats you need to mitigate. You’ve got to patch, patch, patch! Stop what you’re doing and patch!
Except for the fact that there hasn’t been a single real-world exploit conducted against a single target, that I know of. That means that supposed high-risk threats are really a near-zero risk. That’s what I mean by focusing on preventing and detecting what your real threats are. Figure out what your real and true most likely to happen in the near future threats are and focus on preventing and detecting those things.
Prevention of the most likely threats is the most important defense you can have. It may sound funny that I have to write that sentence, but many of today’s conventional computer defenses are based on an “assume breach” mentality, where you either assume your environment is already currently breached or easily could be if someone concentrated on breaking into it. Assume breach essentially concentrates on preventing internal spread and detection. That’s great. All defenses definitely need a strong set of assume breach defenses. But the primary focus always has been and still needs to be on stopping the badness from being successful in breaking in in the first place. Accordingly, I’m more of a STOP BREACH mentality.
Detecting correctly is a matter of figuring out your true most likely threats and determining if you’ve got the detection capability if they successfully occur against your environment. Take all your potential security logging and alert tools and services and figure out which ones map or don’t map to your most likely threats. You’ll see a lot of overlap and some weaknesses. Plug the gaps.
Recovery is damage control and figuring out what you did wrong in the first two pillars, prevention and detection, so it won’t happen again.
Three Control Pillars
For each of the three security control pillars (i.e., prevent, detect, recover) you have to do everything in your power to mitigate the most likely, true threats. You need to combine the best defenses you can split out among the three types of controls:
- Policy
- Technical
- Training
Every security control needs policy behind it. Each control needs policy, procedure, and guidelines. You must empirically document control expectations so there is no ambiguity. Everyone needs to understand what the biggest, most likely threats are and how you are mitigating them. You need to provide expectations, which helps with accountability if someone doesn’t do something right. Or perhaps everyone does everything right and when something bad still happens, it means you missed something, and you have to update the controls. Either way, documented and communicated controls help everyone to understand expectations and row in the same direction.
Technical controls are all the mitigations you can implement using software or hardware to enforce a particular input, action, or output. Whenever possible, implement a technical control to mitigate your biggest threats. They help put down the majority of your risks and do so automatically.
Lastly, some amount of badness will always get past your technical controls. I don’t care what you implement; technical controls are not perfect, and hackers find ways around them. So you need to educate your staff and workers as to how to spot badness when it gets past existing technical controls and what they should do when they see it (hopefully report and mitigate).
Example – Fighting Social Engineering and Phishing
Social engineering and phishing accounts for 70% to 90% of all malicious breaches. It’s important that defenders mount their best defense-in-depth plan to fight it. You start by looking at prevention. How do you stop social engineering and phishing from being successful? You use policy, technical controls, and training.
Your policies and documentation should warn users about the risks from social engineering and phishing and how to prevent, detect, and recover. It should tell users how to avoid the easy social engineering pitfalls and how to report attempts. It should tell users to hover over URLs and to verbally confirm requests that could adversely impact the organization (such as money transfers, gift card purchases, unexpected invoice payments, and wiring instruction changes, etc.). The policies should require specific technical controls to fight it (including SPF, DKIM, DMARC, endpoint protection, patching, anti-spam, and anti-phishing filtering tools, etc.). The policies should include employee requirements to report phishing attempts to the appropriate people and include how to handle ransomware incidents. It should include an Acceptable User Policy, which users must review and sign at the beginning of their employment and annually thereafter. The organization needs to figure out if they should have cybersecurity insurance to limit potential costs from cybersecurity incidents like business scams and ransomware.
Technical controls should include a defense-in-depth set of software and hardware defenses to make phishing and social engineering less likely to be successful. These items, including the items listed above, plus firewalls, reputation services, multi-factor authentication, email attachment blocking, application controls, blacklisting, whitelisting, DNS checks, network traffic anomaly detection, intrusion detection, logging, alerting, and data leak prevention. Technical controls to prevent the most likely types of cyber attacks from being successful should be a huge part of any defender’s focus.
Unfortunately, no matter how great your technical controls are, badness will slip by. You need to have a robust training program for everyone in the organization. They need to be made aware of the most likely threats and what the organization is doing to prevent them. Employees should have security awareness training every year, a longer training session perhaps 15 to 45 minutes long, and monthly training, with shorter involvement, say two to five minutes. Monthly topics should include education about the most likely to occur attacks and increasing trends. Training should include how to recognize the threats, how to report them, and how to treat them. Simulated phishing tests should be sent to employees at least monthly to gauge effectiveness of training and to help give more training to those who need it.
If you are interested in learning more about what you can do to fight phishing and social engineering, see my inclusive webinar on the subject at: https://info.knowbe4.com/webinar-stay-out-of-the-net.
IT staff and other employees should be taught how to treat and respond to successful cases of phishing and social engineering so that compromise is detected quickly, damage is minimized, and recovery operations can begin. IT should figure out how the threat was able to be successful and determine if policy, technical controls, or training needs to be updated to improve prevention or detection.
Summary
So, that’s it. You need to figure out what your most likely, true, biggest threats are. Then figure out how to prevent and detect them. You need incident response and recovery for when those threats get by your existing defenses. You execute the mitigation of risks by issuing policies, implementing technical controls, and educating your people. That’s computer security in a nutshell – 3Ps of 3Ps.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




