If you checked the news this morning, you probably noticed a story getting plenty of play on mainstream news sites: threatening election-themed emails sent to recipients in three states, including the perennial swing state of Florida. Several customers in Florida using the Phish Alert Button (PAB) did indeed report these emails to us yesterday. What follows are some notes and observations about the emails reported to us.
1. The emails are fairly uniform, though some include street addresses (more on which in a bit). All emails demand recipients change their party registration to Republican and vote for Donald Trump in next month's Presidential election.
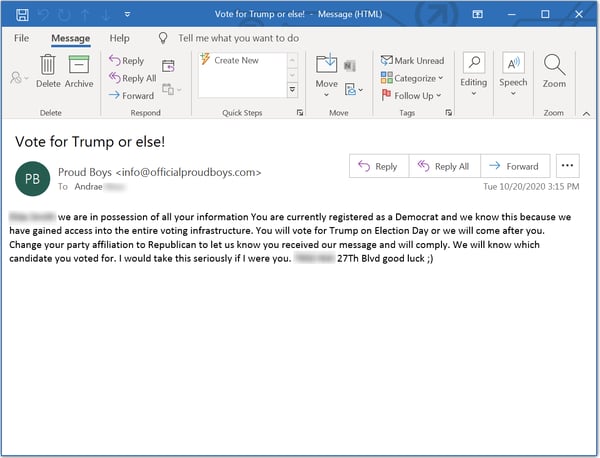
2. The emails were reported to us by individuals at a Florida institution of higher education as well as a retirement community in Gainesville. This is somewhat puzzling. While students, staff, and faculty at institutions of higher education are generally assumed to lean left politically, retirees in Florida are known to lean Republican and are expected to vote in large numbers for Trump.
3. This email very much resembles many of the Bitcoin ransom (aka "Sextortion") emails that have become prevalent over the past few years ("We know you've been watching porn..."). This email form has been adapted to other situations, including COVID-19. In this email, though, the demand is not for Bitcoin, but for votes.
4. The emails reported to us appear to have been sent by or through servers in Estonia and Saudi Arabia. The domain used in the FROM: line of the email was initially registered back in 2017, but was updated on 10/18/2020 -- two or three days ago. We're guessing it was recently bought/sold. Predictably, the domain is anonymously registered. The domain appears to have no presence on the web. And though the headers link the emails reported to us to servers in Estonia and Saudi Arabia, the actual culprits could be just about anywhere.
5. The emails include personal information to lend credibility to the threat. All of the emails reported to us lead off the email body with the name of an individual, though in some cases that name does not match the recipient listed in the FROM: line of the email. More ominously, the email copies sent to individuals in the retirement community include street addresses that appear to be connected with that retirement community. The inclusion of those addresses was clearly a ploy to suggest to recipients that the perpetrators of this email campaign have very specific data on them and their whereabouts. And the fact that the systems of two Florida counties were hacked by Russians in recent years could undoubtedly lend additional credibility to these threats.
6. The Proud Boys themselves deny any involvement. That’s actually believable to some extent as the Proud Boys are an organization more known to lead with fists, baseball bats, and the occasional firearm, not low rent phishing campaigns.
All told, this is a rather ham-handed email campaign, and the ultimate purpose of it remains somewhat of a mystery. Although it is certainly designed to sow fear, confusion, and doubt surrounding the election -- someone is clearly stirring the pot -- the ultimate end game may not be entirely clear unless and until the perpetrators behind it are identified (if indeed they ever are).
It's worth stressing that the actual danger to individuals is likely very low, although law enforcement authorities at the state and national level have been alerted. Like those Bitcoin blackmail emails we saw back in March/April that threatened to infect email recipients with COVID-19, there is little danger to users or the general public.
As always, we strongly encourage organizations to step their users through New-school Security Awareness Training so that they can anticipate and correctly handle these kinds of emails. And it's worth reminding readers that KnowBe4 does offer a free course for home users (who were targeted in this election-themed email campaign).
In the face of threats designed to sow fear, confusion, and doubt, knowledge and sunlight are the appropriate responses.
