 As we documented in a recent blog piece, malicious actors are aggressively exploiting the COVID-19 crisis by re-purposing and overhauling phishing emails they were running before the Coronavirus emerged in late December and began spreading around the world. Although the bad guys have been developing new social engineering schemes uniquely based on the onslaught of recent events, COVID-19 "re-treads" are fast becoming the most common variety of Coronavirus-themed phishing emails that we encounter on a day-to-day basis.
As we documented in a recent blog piece, malicious actors are aggressively exploiting the COVID-19 crisis by re-purposing and overhauling phishing emails they were running before the Coronavirus emerged in late December and began spreading around the world. Although the bad guys have been developing new social engineering schemes uniquely based on the onslaught of recent events, COVID-19 "re-treads" are fast becoming the most common variety of Coronavirus-themed phishing emails that we encounter on a day-to-day basis.Goodbye Passwords & Porn. Hello Injection & Infection.
One of the more surprising -- and alarming -- re-treaded, virus-themed phishing emails we've seen lately actually started its life as a straightforward "sextortion" phish. Over the past week the bad guys behind this particular malicious email campaign have been re-working the template they use, converting it from a sex/porn-based extortion racket into one focused exclusively on exploiting users' fears for their own personal safety in the age of COVID-19.
The evolution and development of this particular phish is as interesting as it is worrisome. Here's the "original" version of the email we've been seeing (with minor variations) for well over a year now (courtesy of customers using the Phish Alert Button).
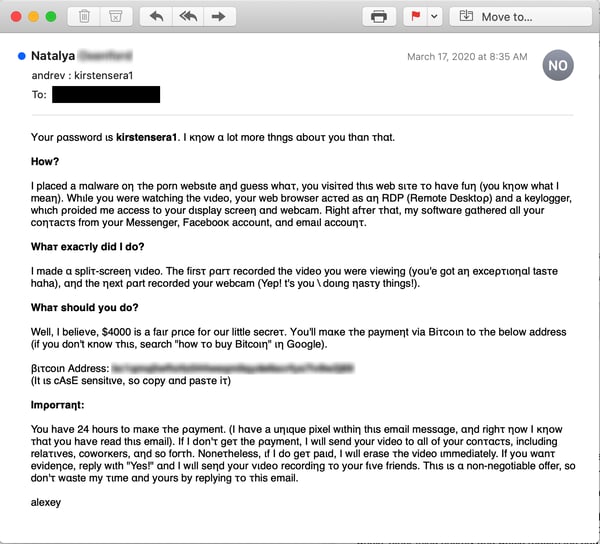
Note the distinctive Subject: line, which effectively announces to targeted users that one of their username/password combos (undoubtedly lifted from the massive breach databases of compromised credentials easily available online) is now known to the bad actors behind this email. Note also the effective price for buying "peace-of-mind" from these malefactors. It's not cheap.
This phish (which typically hails from an outlook.com email address) happens to be one of the more common ones we see every day. And, unfortunately, the threat being made here may strike some users as credible. (Whether they can surmount the technical hurdles of actually paying the demanded Bitcoin ransom is another question entirely.)
Last Thursday (March 19) we spotted some interesting changes to this familiar, if utterly toxic malicious email.
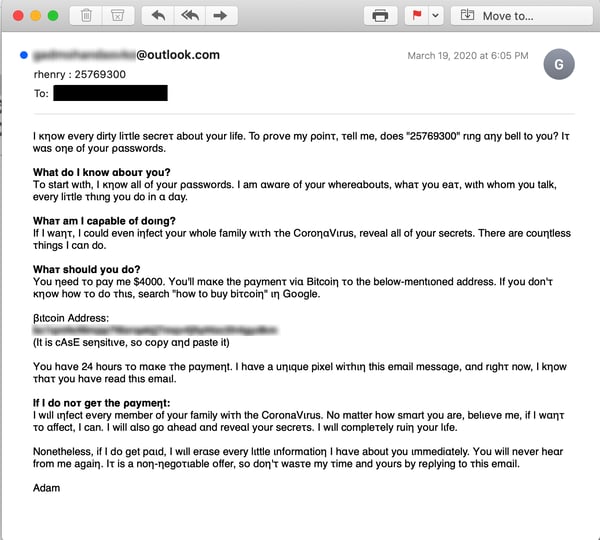
The changes are small -- most of the features of the original remain intact -- but very significant. After leading with the familiar bluster about "owning" all the target's online passwords and accounts, the email body veers into a threat to infect users and their family members with the Coronavirus.
Let's be clear: this is not a credible threat. It is pure bluster and posturing of worst sort, as there is next to zero chance that the criminals running this campaign are going to out themselves by assaulting victims in public. Moreover, law enforcement officials have already announced that they will prosecute these kinds of threats as terrorism and even moved against an individual planning to attack a hospital treating COVID-19 victims.
Despite introducing a new threat into a phishing email that was already plenty hair-raising, the bad guys failed to give that threat the prominence one might have expected in such an email.
That has now changed. Just this morning -- a full week after the first revision -- we spotted a newly overhauled version of this phish:
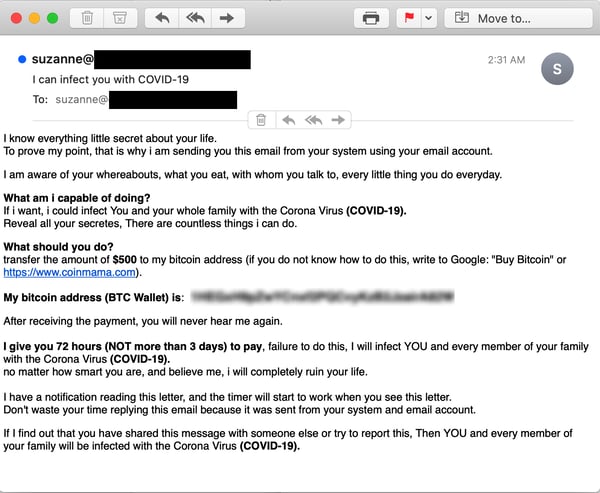
Note the changes from the previous, quickly modified version that emerged last week:
- The Subject: line now explicitly threatens to infect users.
- All references to sex and porn have been removed. The exploitation of compromised online accounts remains, but only as a passing reference.
- The main focus of the email from top to bottom is now the threat to infect -- and it is hammered home in raw terms over and over.
- The "peace-of-mind" Bitcoin tax has dropped from $4000 to a mere $500. That price drop undoubtedly reflects the workings of supply and demand in this particular "niche" market and not some newly discovered compassion on the part of the bad guys for their victims, many of whom are struggling with major changes in their lives and may even have lost their jobs in the past few weeks.
The true potential cost here is to the emotional well-being of those unfortunate enough to receive this malicious email. And it's all happening because login credentials for billions of users at numerous sites across the web have been repeatedly compromised and regularly published online over the past 5-10 years.
The bad guys may not always get it right the first time but -- like Godzilla -- they just keep coming.
Conclusion
Malicious actors are aggressively -- even ruthlessly -- exploiting the COVID-19 crisis by throwing everything and the kitchen sink at rattled users, many of whom are now working from home in computing environments markedly less secure and safe than those they enjoyed at the office.
Now is the time to step your users through New-school Security Awareness Training so that they can identify and handle the wave of malicious COVID-19 phishes currently surging into their inboxes. In so doing, you will not only be giving your users the tools to achieve true "peace-of-mind" in the face of such attacks, but you will be buying a healthy dose of it for yourself, your hard-working IT staff, and the rest of your organization.
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!




