 In what may be either a moment of brilliance or desperation, scammers are attempting to use coronavirus infection threats as a means of further convincing victims to pay up.
In what may be either a moment of brilliance or desperation, scammers are attempting to use coronavirus infection threats as a means of further convincing victims to pay up.
Since they began in July of 2018, sextortion scams have evolved. They originally started because of exposed credentials as part of earlier data breaches. These credentials were enough to establish credibility that the sender knew something about the recipient. The general scam is to state that the scammer knows the victim has been going on adult sites and will “out” them if they don’t pay up.
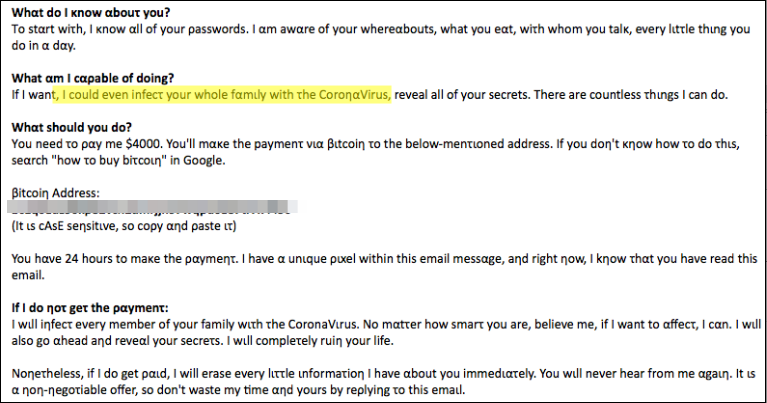
In a modern twist, security researchers at Sophos have spotted a variant of this scam where the scammer makes the laughable claim that they can infect the recipient and their whole family!
Source: ExecuteMalware
As with every sextortion scam, they all can safely be deleted and forgotten. What is interesting is the use of homographic characters in the message. These “lookalike” characters allow messages like this to pass inspections by email scanning engines looking for specific phrases and words.
We’ve seen an uptick in corporate users being the target of these kinds of scams – presumably, receiving this at a work email address is intended on creating additional anxiety, as the recipient doesn’t want to lose their job. Organizations need to keep employees educated using Security Awareness Training to prepare them for the day a phishing email may will reach their Inbox and attempt to evoke a response that could put the recipient and the organization at risk.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




