 By Eric Howes, KnowBe4 Principal Lab Researcher. Having already published three blog pieces on the epidemic of Coronavirus-themed phishing emails and spam/scam offerings online (see HERE, HERE, and HERE), we were wondering what else the bad guys might be ginning up for stressed-out users and IT folks working the trenches. The answer arrived this week as COVID-19-themed phishes exploded.
By Eric Howes, KnowBe4 Principal Lab Researcher. Having already published three blog pieces on the epidemic of Coronavirus-themed phishing emails and spam/scam offerings online (see HERE, HERE, and HERE), we were wondering what else the bad guys might be ginning up for stressed-out users and IT folks working the trenches. The answer arrived this week as COVID-19-themed phishes exploded.
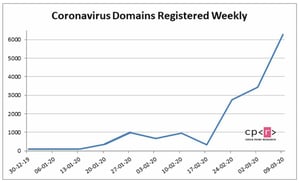
On Monday and Tuesday customers using the Phish Alert Button (PAB) reported a massive surge in virus-themed phishing emails. Although we had already seen 90 percent of those emails over the previous days and weeks (and had documented them in our first three blog pieces), we were nonetheless surprised by the sheer volume of emails reported -- a phenomenon we suspect may have been driven by the dramatic escalation of the COVID-19 health crisis in the United States at the end of the previous week.
On Wednesday and Thursday, though, customers began reporting an entirely new set of phishing emails. Curiously, most of these apparently "new" phishing emails were somehow also strangely familiar (more on that in a bit).
In this fourth installment of our COVID-19 phishing reports, we will review the new crop of Coronavirus phishing emails that landed this week. And, as before, we will be offering a generous helping of screenshots so that you and your users and employees know what to look for.
The Three Waves
Before tackling the very latest phishing emails reported to us by customers using the Phish Alert Button (PAB), we thought it might be useful to do a quick review of the development of COVID-19-themed phishing emails that we've been tracking since early February.
Looking back, we can now discern three distinct waves of phishing emails reported by customers.
1. The first wave, which began growing slowing over the course of February and early March, mainly involved straightforward spoofs of the CDC (Centers for Disease Control), WHO (World Health Organization), and a few other reputable authorities including HR departments within targeted organizations. These spoofs generally purported to offer information and updates on the unfolding crisis, leveraging the trust vested in those spoofed authorities to trick users into clicking through links and attachments to malicious content (mostly credentials phishes, but occasionally malware, including Emotet).
During that time period we also observed a rather predictable rise in spam/scam emails trading on fear and confusion to push the usual variety of dodgy products and services -- fake vaccines, price-gouged health care products (masks, sanitizers), as well as books, videos, and bogus "miracle cures."
2. In the second wave, malicious actors began experimenting with new and novel social engineering schemes -- some more successful and convincing than others. If nothing else, though, this second wave demonstrated that the bad guys were seriously committed to exploiting the chaos and growing hysteria over the spread of virus by rapidly developing a larger menu of phishing templates.
We covered the first and second waves of Coronavirus phishes in our earlier blog pieces. This second wave, in particular, proved to be relatively brief and was soon overtaken by a massive wave of new virus-themed phishing emails that crashed into users' inboxes starting Wednesday and Thursday.
3. The third wave, which arrived mid-week, saw the bad guys building out their repertoire of customized social engineering schemes by re-purposing a wide variety of older phishing emails -- all those golden oldies so depressingly familiar to end users and IT departments alike, now newly re-invigorated and sent into battle once again under the banner of the mighty Coronavirus.
It's that third wave of re-purposed, "standard" phishing emails that we'll be focusing on in this blog piece, for it turns out that the Coronavirus is always the perfect complement to whatever phishing campaigns your average bad guy happens to enjoy running.
We should note that we will not be covering the kinds of more traditional spam/scam emails that we did in our earlier blog pieces. Those emails are still in circulation, but they've now been utterly eclipsed by the sheer volume of truly malicious phishing emails washing into users' inboxes.
Everything Old is New Again
Over the course of just 48 hours this week we spotted ten distinct new varieties of re-purposed, "standard" phishing emails. Although all of these malicious emails strive mightily to be relevant and topical by invoking the COVID-19 crisis in one way or another, they should still look at least vaguely familiar. That's no accident, as most of them are just "warmed over" or "re-treaded" versions of the same malicious emails that have been plaguing users and IT departments for years.
File Sharing (Branded)
The bad guys love spoofing and exploiting file sharing services, as they know many of the biggest brands (Dropbox, OneDrive, SharePoint, WeTransfer, Sharefile, et al) will be very familiar to cubicle dwellers in offices around the world. Thus, it was only natural that malicious actors should turn to spoofed file sharing emails to continue dangling purported information about the crisis to concerned users.
This first one relies on Office 365 branding to push a vaguely ominous "Coronavirus Review" on recipients.
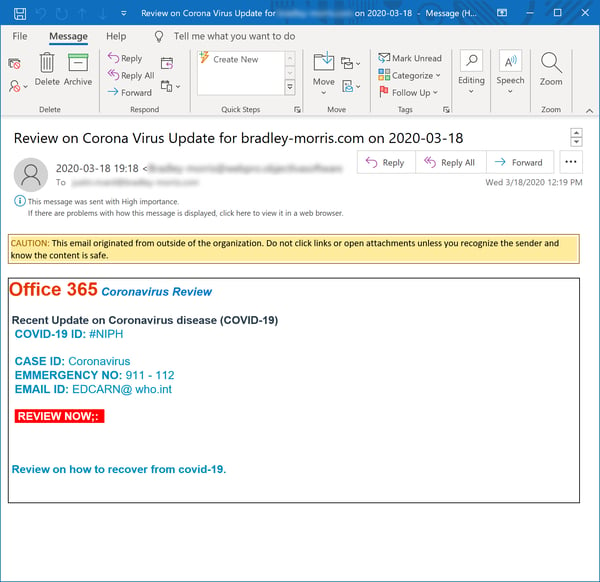
Although this email does not clearly match any known Microsoft form email that we're familiar with, the "Review Now" link predictably leads to a page that should look all too familiar familiar to all too many users.
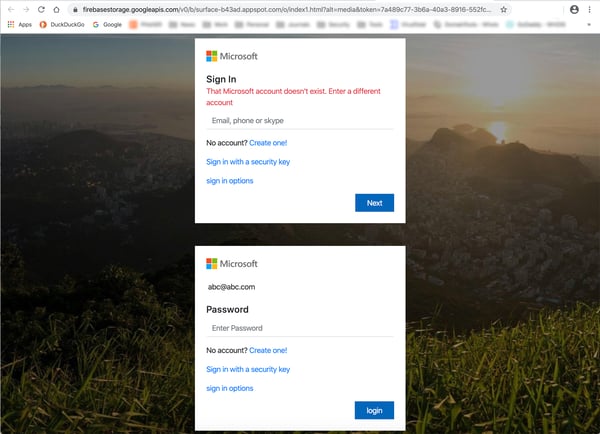
It's one of the most common credentials phishes in the world -- the fake Microsoft login page.
This next phish hues more closely to the real thing, clearly striving to look every bit the legitimate SharePoint email...
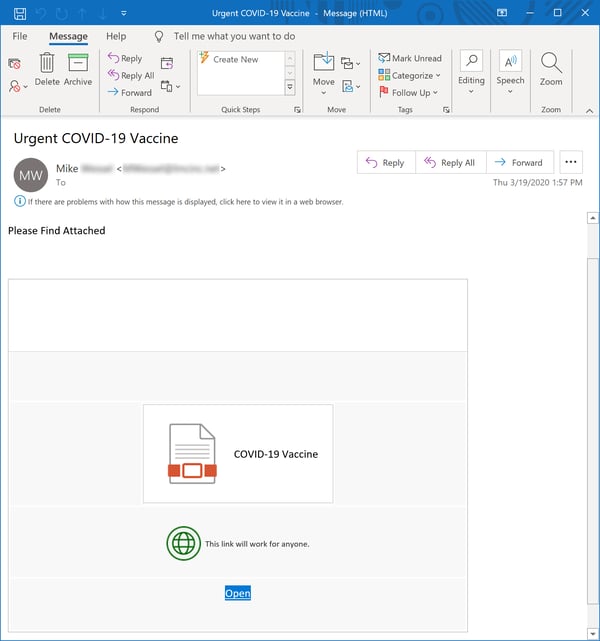
...which sends users on to a fake OneDrive document hosted on what is probably a compromised SharePoint account.
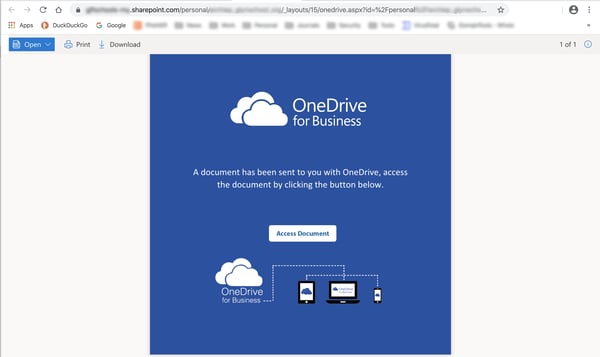
The document itself serves only to shuttle click-happy users along to a spoofed Microsoft login page almost identical to the one used with our first example above.
How many users will even question why they're being asked to login for a second time to access a document purportedly hosted on Sharepoint or OneDrive -- especially when that document is offering information on a COVID-19 vaccine?
Secure Docs
The bad guys have also been keen to spoof and exploit secure document delivery services, many of which (again) should be familiar to users working in many companies and organizations.
Though a bit amateurish, this next phish happens to be one of the more common virus-themed phishes reported to us by customers this week. When users open the attached Word document and input the provided "secure code"...
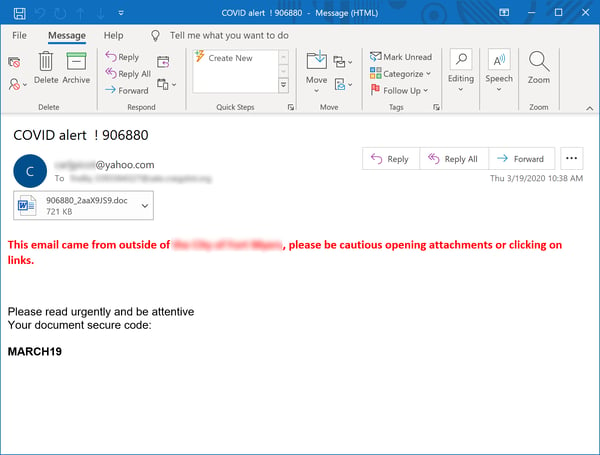
...they will find themselves staring at a malicious, macro-laden document complete with instructions to view its "full content," which was allegedly created in an older version of Word -- an old and familiar ruse.
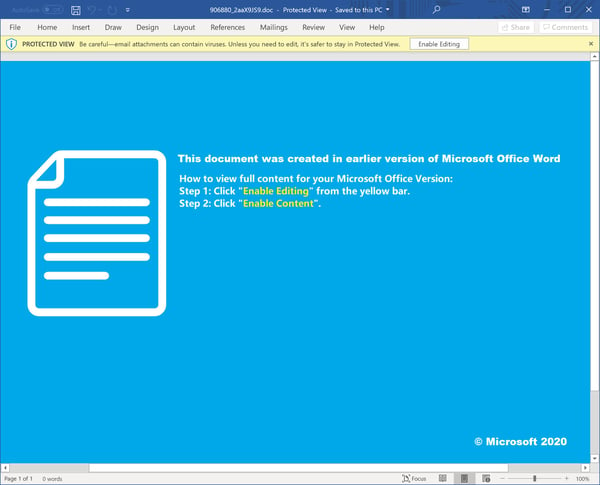
The bad guys are certainly capable of spoofing the more common secure doc delivery services in rather convincing fashion. See for example...
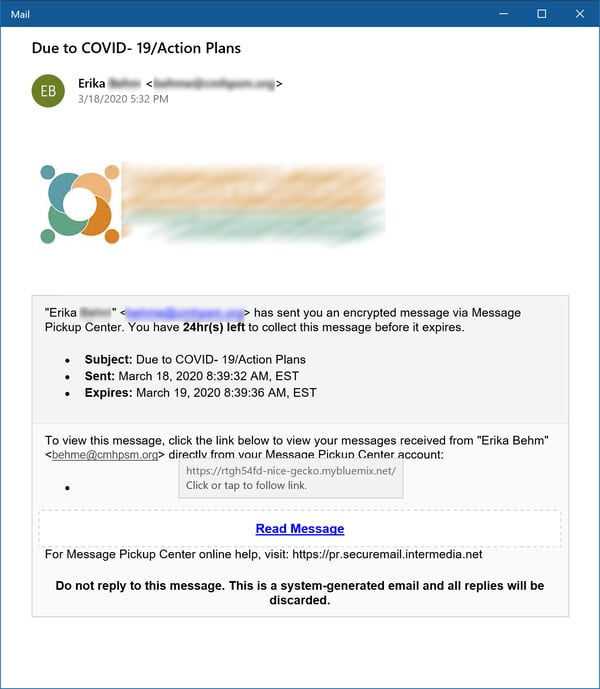
...which not only matches the look and format of common secure messaging emails but even sports the targeted organization's logo at the top of the email body.
File Sharing (Casual/Individual)
Some of the more strikingly effective and wily phishing emails we've seen over the past few years involve malicious attempts to imitate the kinds of routine, everyday exchanges of files and information between employees that are common to office life, whether those users happen to be working in the same office or for different organizations in distant parts of the country.
This phish rather crudely attempts to bulldoze recipients with the sheer shock of a reported infection within the organization, counting on alarmed users to open that attachment for more information.
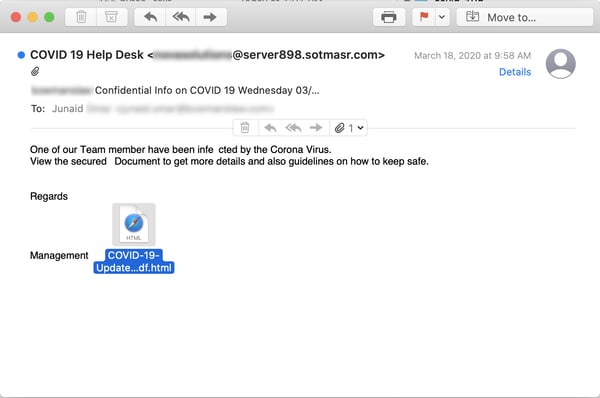
The HTML attachment is, of course, yet another credentials phish, though decidedly low-rent when compared with those we encountered earlier.

Our next example takes a more casual approach, citing the author's purported quarantine status as an excuse to push a malicious attachment (caught by the organization's anti-malware protection in this case) on sympathetic users.
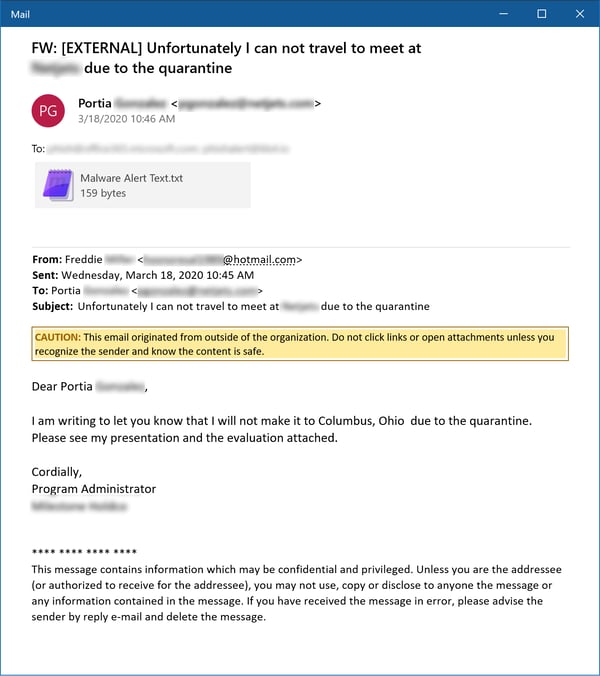
Quarantines, it turns out, are incredibly handy excuses for all kinds of malicious activity.
Purchases & Orders (Invoices/POs/RFQs)
Some of the more reliable old war horses for malicious actors involve spoofing parts of the order/purchase process. Thus, fake invoices, POs, and RFQs abound in the daily haul of phishing emails reported to us by customers.
This slickly designed phish not only manages to dangle potential new business in front of recipients, but convincingly spoofs LinkedIn in the process.
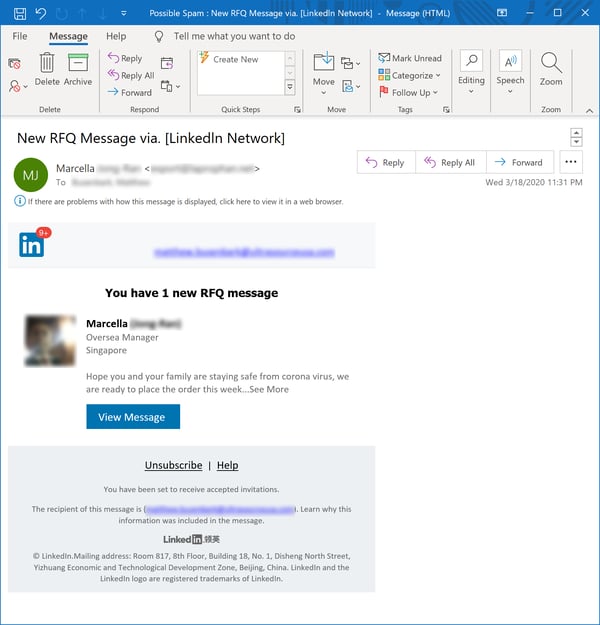
Unfortunately, the bad guys seem to have drawn blanks when trying to figure out where to send users who click the proffered link...
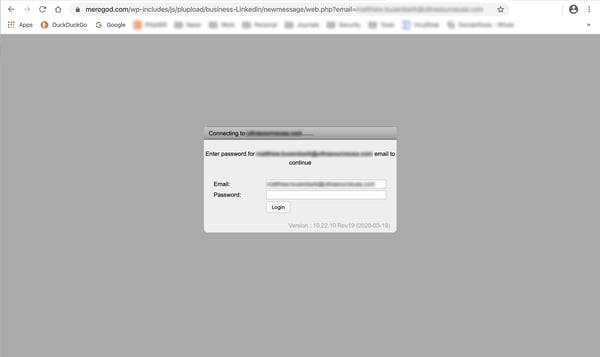
..dropping users on a login page that looks like everyone's worst nightmare of a user-indifferent, corporate IT culture straight out of the Nineties.
Meetings & Schedules
Malicious actors are not entirely indifferent to your pain. They know your usual office routines and operations have been disrupted over the past few weeks, and they're ready to jump in to help you sort it all out.
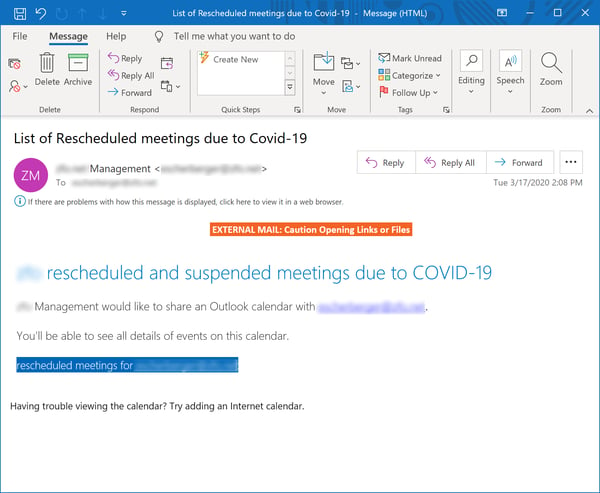
This email, which looks vaguely Microsoft-ish, doesn't promise anything unworldly like a "miracle cure" for the Coronavirus or a dark expose on the evil machinations of Deep State actors who (rumor has it!) reportedly released the virus in the first place. Nope, it's offering the kind of news that just about every veteran cubicle dweller can use to simply get through another day.
Package Delivery
Pandemic or not, business must continue. And one key part of everyday office life involves package deliveries through services like USPS, UPS, DHL, and Fedex -- all favorite targets of spoofed emails from the bad guys.
Although this next example doesn't directly spoof any of those familiar brand names, it does casually invoke the routine headaches caused by the Coronavirus to push a malicious link (disguised as a fake attachment) on unsuspecting users.
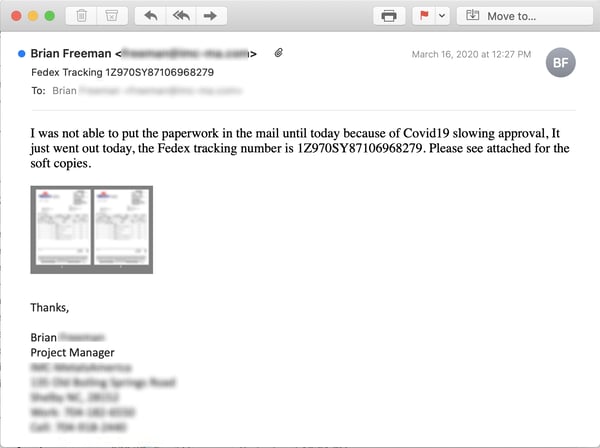
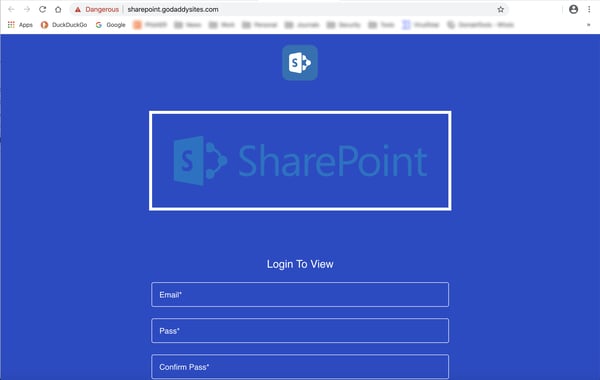
The attachment itself turns out to be yet another credentials phish, this time spoofing SharePoint.
Email Accounts
Yet another favorite ruse on the part on malicious actors is to tell users that some problem with their email accounts requires them to log in to "confirm," "validate," or "verify" those accounts.
Unsurprisingly, we see bad guys trying to shoehorn the Coronavirus into one of the more common social engineering schemes we see on a daily basis.
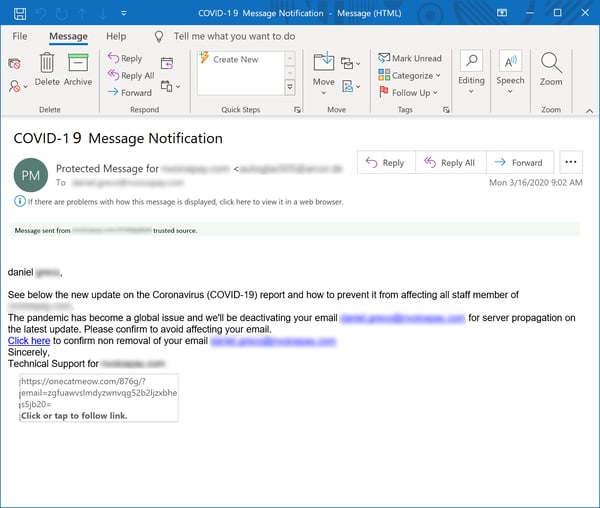
Apparently, the Coronavirus now infects both users and their email accounts as it spreads across the globe, requiring "server propagation" and clicks from employees to "confirm non removal of your email" -- a turn of phrase straight from the Official Bureaucratic Style Guide from Hell. Yes, it's all a bit confusing. But, hey, such are the strange times we live in.
HR, IT, & Corporate Policies
As we noted in one of our previous blog pieces on virus-themed phishes, the bad guys regularly spoof IT and HR departments, leveraging their inherent authority to coerce users into clicking malicious links and opening malicious attachments.
This email convincingly keeps it brief, instructing users to familiarize themselves with yet another new batch of policies handed down from on high, presumably in response to the virus.
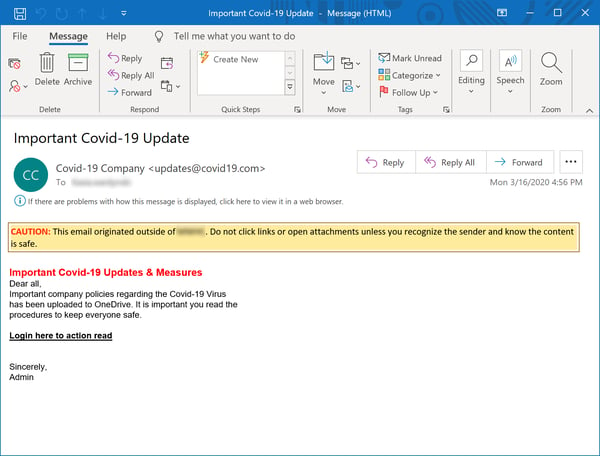
Users who actually bother to look will discover that they now work for the "Covid-19 Company." In addition to eating corporate inboxes, it would appear the Coronavirus now also does Mergers & Acquisitions. (We're still waiting to see the virus's official logo.)
Voice Mail / Voice Messages
One of the more prevalent social engineering schemes or phishing "genres" reported to us over the past year has been fake voice mail. And, before you ask, we can assure you that we have no reports of the Coronavirus leaving voice messages for alarmed employees (yet). The bad guys are happy, however, to deliver yet more (fake) news about COVID-19 straight to your VMsg (sic) mailbox.
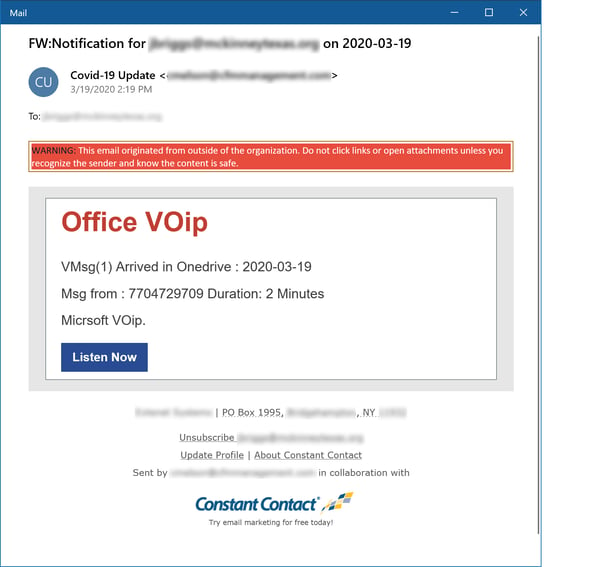
Note that this particular malicious email was delivered through Constant Contact. Like Sendgrid (which delivered a Coronavirus phish covered in one of our previous blog posts), Constant Contact is a popular, widely-used email service provider that we expect many companies and organizations will have whitelisted, enabling these kinds of phishes to sail right through firewalls and anti-malware protection straight into users' inboxes.
CEO Fraud
And then there's the Big Kahuna of phishing emails: CEO Fraud (aka Business Email Compromise). CEO Fraud is booming business for the bad guys these days, and they're not afraid to bring the Coronavirus to the party as a plus one.
Most CEO Fraud phishes that we see start off with a simple, brief email -- usually from a spoofed senior executive within the targeted organization -- seeking to draw the recipient (almost always carefully selected for their particular role within the organization) into a back-and-forth that eventually ends with a request to provide assistance in the furtherance of some kind of fraudulent scheme.
The Coronavirus is small -- completely invisible to the human eye -- and in this email the bad guys don't even bother to name it directly. A simple nod to current circumstances is all that's required. It's a light touch -- perfectly calibrated to this kind of social engineering scheme.
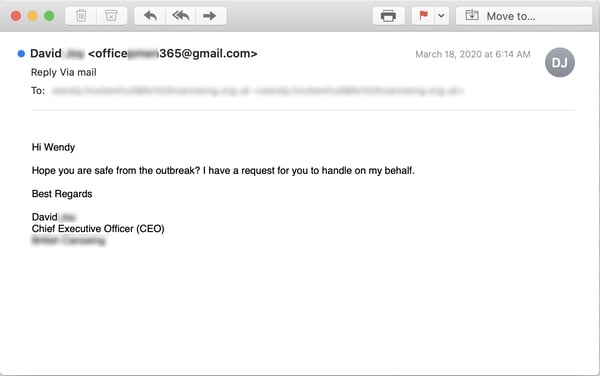
Users who take the bait will almost certainly find themselves being asked to do one of the following: 1) wire money to a bank in Hong Kong; 2) buy thousands of dollars in gift cards; 3) fork over copies of employees' W-2 forms. It's all a bit of a roll of the dice. And whichever variety of CEO Fraud phish you happen to get, it's guaranteed to cost your organization a serious amount of money and plenty of headaches.
Why play it safe, though, with the usual, boring CEO Fraud social engineering schemes when you've got the mighty Coronavirus playing on your side? If you're a bad guy with this kind of once-in-a-lifetime opportunity staring you in the face, you'd best start swinging for the fences.
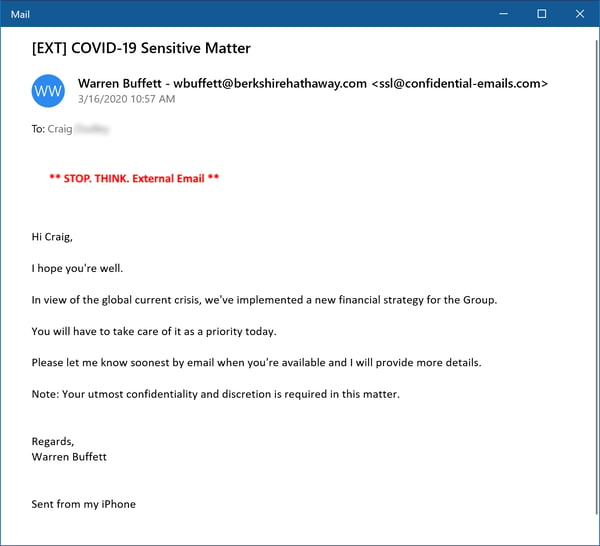
When Warren Buffett comes looking for an employee in your organization to go on a secret mission for his company, you'd wouldn't be unwise to worry that someone just might take the bait.
Money talks, but pure power often talks louder. In this cleverly designed phish, malicious actors spoof a sitting U.S. Senator (now apparently hiding out somewhere in Turkey) to deliver official word from the White House Coronavirus Task Force.
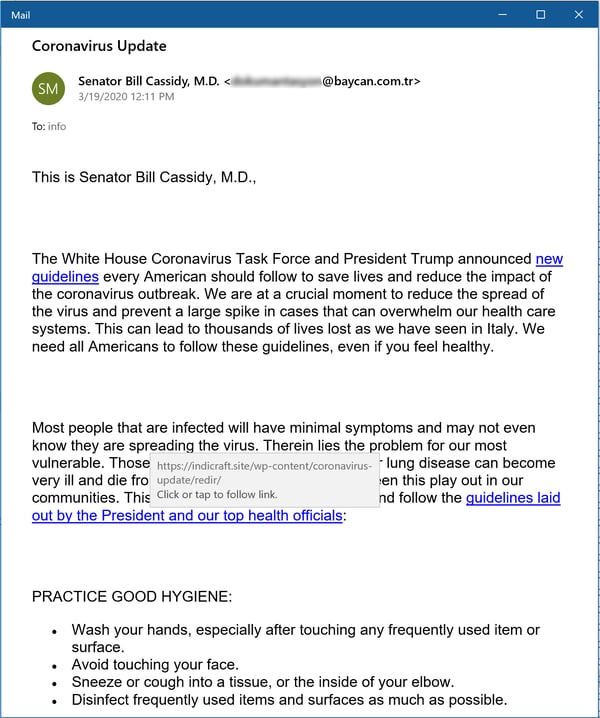
This phish works for several reasons. First, members of Congress are in fact frantically messaging their constituents about the developing crisis, keen to demonstrate that they are on top of things, most decidedly "in the loop," and working hard to protect voters back home.
Second, though, this phish smartly mimics the kind of approach typically seen in official statements from government officials and elected representatives, even to the point of providing the usual checklist of precautionary advice to "flatten the curve" of the spreading virus.
In short, there are no wild-eyed conspiracies or hyperventilating pronouncements being peddled here, just plain old good information from the seat of power itself -- along with a bomb tucked in the underbrush, waiting to be detonated when users click any of the links.
Conclusion
You don't need us to tell you that many of your users and employees are stressed out these days -- perhaps even to point of being rattled. That's not only entirely understandable but, sadly enough, strangely normal in some ways. And if the Coronavirus itself weren't already bad enough for your organization, you've now got malicious actors looking to exploit that stress and fear to compromise your organization's endpoints and network. That, too, is normal to some extent, sad to say.
If there is any good news in the batch of phishing emails we've reviewed in this latest blog piece, it's that however aggressive and malicious these virus-fueled social engineering schemes happen to be, they should also be somewhat familiar to your users -- provided you've been regularly educating them about the dangers lurking in their inboxes. If you haven't been doing that already, it's high time you started, lest the bad guys take what is already a challenging situation for your organization and turn it into an out-and-out disaster.
We have uploaded 100 examples of this massive wave, broken out in phishing attacks and spam examples:
If you are not sending simulated phishing attacks to your users, now is the time to start. We have just added a coronavirus template to the options you can use for the free phishing security test below. You can also check out our coronavirus phishing and security awareness resources to help keep your network secure while users are working from home.
 Here's how it works:
Here's how it works:
