 In several recent blog posts we've showed you the myriad ways in which malicious actors have aggressively -- even ruthlessly -- deployed social engineering tactics to leverage the COVID-19 pandemic for financial gain. Just over the past few days we spotted several new virus-themed phishing emails that underscore just how rapidly and nimbly the bad guys are moving to exploit every new twist and wrinkle in the crisis.
In several recent blog posts we've showed you the myriad ways in which malicious actors have aggressively -- even ruthlessly -- deployed social engineering tactics to leverage the COVID-19 pandemic for financial gain. Just over the past few days we spotted several new virus-themed phishing emails that underscore just how rapidly and nimbly the bad guys are moving to exploit every new twist and wrinkle in the crisis.
Below are two emails that were reported to us on Monday and Tuesday of this week by customers using the Phish Alert Button (PAB). Both attempt to use the emerging U.S. fiscal stimulus package to craft Coronavirus-themed social engineering schemes designed to trick users into clicking malicious links.
The first phish we spotted is a bit confused, at first billing the embedded link as a way to "keep up to date with official/regulatory information" before finally tossing in a little something that could well pique the curiosity of more than a few users.
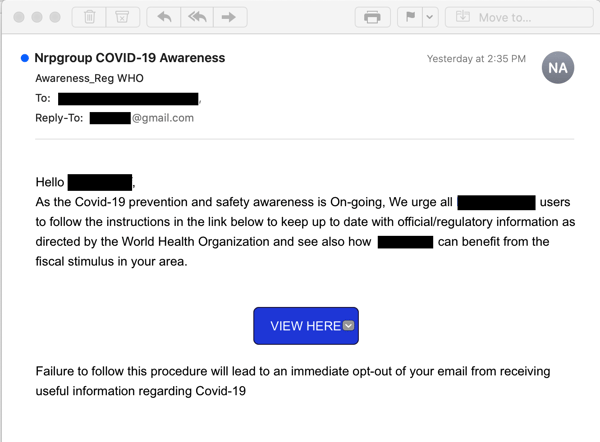
Yeah, it's a curious move to invoke the authority of the WHO just before pivoting to information about how readers "can benefit from the fiscal stimulus in your area." With confused and contradictory stories coming out of Washington D.C. about just what might be in that stimulus package, however, many readers will be happy to click the Big Blue Button to find out more.
The second email is a bit more straightforward in its approach, even if its focus on an alleged individual tax cut falls a bid wide of the truth.
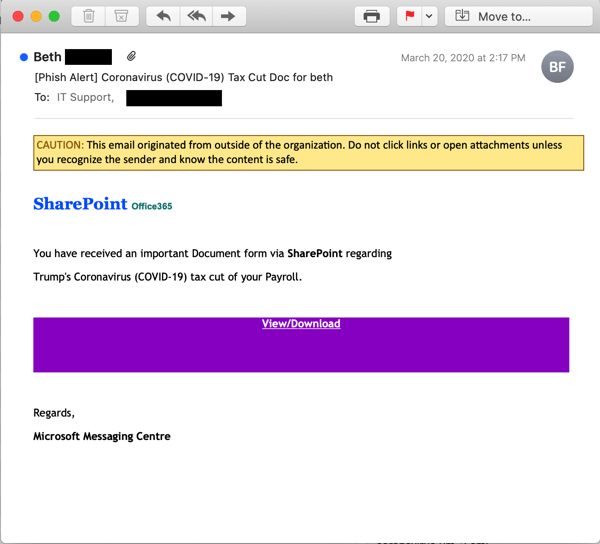
Still, it's a smart approach for the bad guys. We all like money, and we all like tax cuts that give us more of it.
Unfortunately, the links in both emails were dead by the time we checked them. Our best guess, based on experience with a myriad of virus-themed phishes so far, is that both emails likely booted users to credentials phishes of one sort or another.
What's most striking about these emails, though, is that they were crafted while the stimulus package was still being negotiated. The bad guys didn't even wait for the final bill to pass both houses of Congress and hit the President's desk for signature. One whiff of money being fed to users -- and, potentially, to their employers -- and these malicious actors were on it.
The COVID-19 crisis is unfolding rapidly, and malicious actors are proving day in and day out that they are more than capable of aggressively riding the swelling tide of new events. The real question is, are your own users capable of adapting as fast as the malicious actors trying to trick them into opening the door to your network?
New-school security awareness training can ensure your end users know how to identify and report suspicious emails, including malicious Coronavirus-themed phishing emails. In fact, we just announced the addition of two new categories of email templates directly related to Coronavirus/COVID-19. We are moving all of our existing Coronavirus-related items to these new categories.
In times of crisis, it is important to ensure your users are regularly tested against the latest threats landing in their inboxes. A free phishing security test can help you get started.
Let's stay safe out there!
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




