By Eric Howes, KnowBe4 Principal Lab Researcher
Just two weeks after we reported that the bad guys had effectively converted LinkedIin into a phishing platform, Facebook once again found itself being used as an attack vector -- this time for the well-known and much feared Locky ransomware.
Two days ago security researchers Bart Blaze and Peter Kruse reported that malicious messages delivered via Facebook Messenger were being used to trick unsuspecting marks into kicking off a download and install process that, in some cases, ended with Locky ransomware being installed on victims' PCs.
Of all the social media platforms, Facebook is undoubtedly the most heavily targeted given the unsurpassed size of its user base as well as the wide range of native functionality that it offers malicious actors. While many of the elements in this particular attack have been seen before, there was at least one that was new and rather unique.
The Attack
On November 20 an undetermined number of Facebook users received messages in their Messenger accounts from other users already familiar to them. The message consisted of a single .SVG (Scaleable Vector Graphic) image file which, notably, bypassed Facebook's file extensions filter. (.SVG files are XML-based and allow the embedding of other content, including dynamic content -- exactly what the bad guys needed in this scenario.)
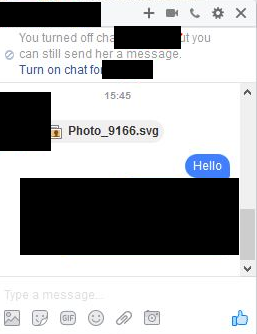
Users who clicked the file to open it were, unbeknownst to them, launching an embedded and obfuscated Javascript that performed at least two key actions:
First, the malicious Javascript redirected users' Chrome web browsers to a spoofed Youtube page that prompted users to install two Chrome extensions allegedly needed to view the (non-existent) video on the page. (Whether users of other browsers were similarly exploited is not known.)
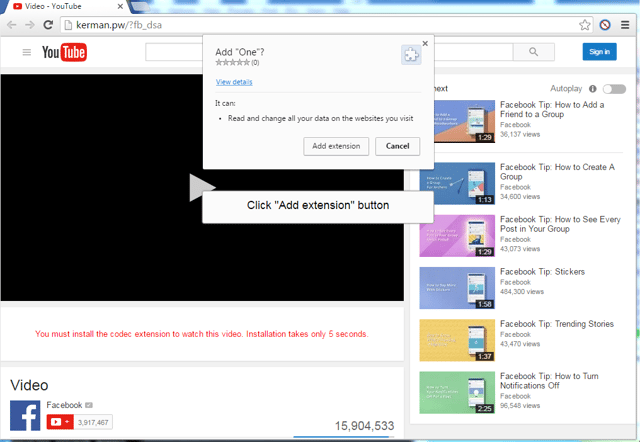
This fake video codec ruse, of course, is a widely used tactic among malicious actors of all kinds on the internet designed to trick users into installing potentially unwanted or outright malicious software.
In this instance, the two Chrome extensions were used to allow the malware a limited degree of self-propagation by exploiting the "browser's access to your Facebook account in order to secretly message all your Facebook friends with the same SVG image file."
Second, on some users' PCs the embedded Javascript also downloaded and launched an instance of Nemucod [PDF], a trojan downloader with a long history of pulling down a wide variety of malicious payloads on compromised PCs. Users unlucky enough to encounter this version of the malicious script saw their PCs being taken hostage by Locky, a sophisticated crypto-ransomware variant that's been cutting a wide swatch of destruction online since February of this year. Locky victims can expect to pay $400-$600 to recover their files. And ransomware outbreaks inside corporate networks bring with them a daunting cluster of headaches beyond the mere cost of the ransom itself.
The Upshot
It's worth noting that the two malicious Chrome extensions used to propagate this malware were quickly taken down from the Google Play store. Facebook itself began filtering .SVG files. Such a prompt response was exactly what was needed and, indeed, expected from these companies. In recent years both Google and Facebook have become extremely aggressive in blocking malicious links and files that bad actors have attempted to spread through these companies' respective platforms.
Moreover, Facebook itself denies that Locky was installed as part of this attack, although some uncertainty remains as to whether the researchers in this case might have encountered two slightly different variants of the same underlying malware.
Nonetheless, despite the laudable efforts of Google and Facebook to contain malware and other types of attacks and scams, malicious content continues to leak through even the most hardened of their defenses. This is not the first time Facebook features like Messenger have been leveraged to spread malware, nor is the first time that malware has appeared on the Google Play store. And fake Youtube sites pushing fake codecs have been a dime-a-dozen affair for a number of years.
Conclusion
As we pointed out when discussing LinkedIn and Paypal (yet another well known online service the bad guys managed to convert into a phishing platform earlier this year), these kinds of highly popular online services are particularly dangerous when exploited by malicious actors because of the inherent trust placed in them by users, who aren't likely to be expecting malicious attacks from contacts on LinkedIn or friends on Facebook.
IT security departments should regard popular social media services as potential attack vectors and take appropriate steps to educate their users about the threats that lurk in online venues that are otherwise widely trusted by default.
Free Ransomware Simulator Tool
How vulnerable is your network against ransomware attacks?
Bad guys are constantly coming out with new versions of ransomware strains to evade detection. Is your network effective in blocking ransomware when employees fall for social engineering attacks?
KnowBe4’s Ransomware Simulator "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 10 ransomware infection scenarios and show you if a workstation is vulnerable to infection.
Don't like to click on redirected buttons? Cut & paste this link into your browser:
https://www.knowbe4.com/ransomware-simulator





