By Eric Howes, KnowBe4 Principal Lab Researcher.
Several months ago we blogged about a startling discovery by threat researchers at Proofpoint: the bad guys had figured out a way to turn Paypal itself into a phishing platform, exploiting the "money request" feature in Paypal, which allows senders to include a personalized message, to phish potential victims via malicious emails delivered through Paypal's own service. Those unwary enough to click the embedded links included in those malicious emails were rewarded with the Chthonic banking trojan.
Recently we encountered yet another successful attempt to convert a legitimate online service into a phishing platform. This time it's LinkedIn, the social networking service familiar to hundreds of millions of users and now a staple in American business culture.
How did this happen?
LinkedIn's Value to Malicious Actors
LinkedIn has been the focus of online scams and phishing attacks for a number of years now, primarily because of the wealth of data it offers on employees at corporations. Just as corporate recruiters ply LinkedIn's treasure trove of employee data to find potential recruits for open positions, malicious actors mine that same collection of data to identify potential marks for business email compromise attacks, including wire transfer and W-2 social engineering scams, as well as a number of other creative ruses including:
1. Credentials Phishes, in which the bad guys use spoofed LinkedIn support notices to trick unwitting victims into coughing up the credentials to their LinkedIn accounts, which can then be leveraged for further mayhem.
2. Advance Fee/Fake Job Offer Scams, which see the bad guys using Connection Requests from fake profiles as the initial contact in schemes designed to trick users into parting ways ways with money or other valuable data.
3. Spoofed/Fake Connection Requests, which allow the bad guys to leverage LinkedIn's reputation with users to spring malicious downloads employees sitting inside corporate networks.
4. Dating/Romance Scams, which are often initiated through LinkedIn's InMail feature but which inevitably lead to scams perpetrated through external email accounts.
5. Spear-Phishing/Whaling, one of the more common uses of LinkedIn by malicious actors, who exploit LinkedIn profile data to hone and target other types of attacks on corporate employees.
The common element in most of these scams is the use of fake profiles whose reputation/trust is enhanced by real LinkedIn users accepting bogus Connection Requests. Once a bogus or fake profile has become sufficiently reputable it can be used to launch still other types of attacks both inside and outside LinkedIn. In other cases, the bad guys may use compromised but otherwise real and legitimate LinkedIn accounts for the same purposes.
Seeing Double: The Same Phish Delivered Twice
Last week we encountered a use for LinkedIn that we had never seen before: as a platform for launching the same kinds of phishing attacks that are routinely reported to us by customers using the Phish Alert Button (PAB) and who find them lurking in corporate inboxes after these phishes sail past all manner of security solutions. What surprised us most, though, was that we saw the same phish delivered to two different marks, both using LinkedIn's messaging features. But they were delivered in different ways.
In the first case a user reported receiving a standard Wells Fargo credentials phish through LinkedIn's InMail: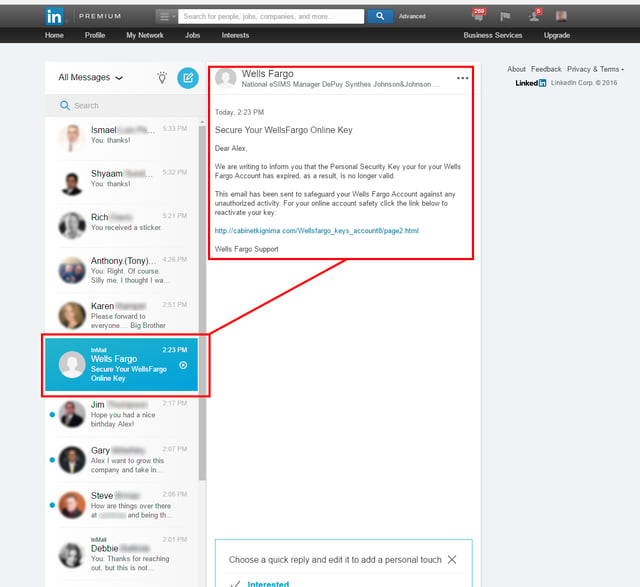
Note that this particular InMail appears to have originated from a fake Wells Fargo account. The supplied link leads to a fairly typical credentials phish (hosted on a malicious domain since taken down):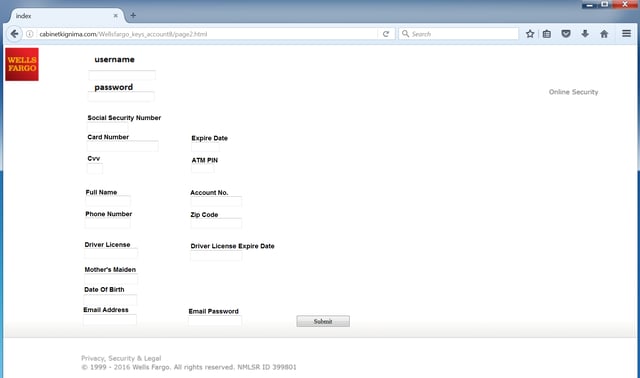
LinkedIn's InMail has been used to initiate all manner of scams, but we had never seen InMail used to launch a standard credentials phish targeted at bank account holders. We did ask the user who reported this phish whether he did, in fact, have a Wells Fargo account. He reported that he did, but insisted that there was no way the malicious actors in this case could have known that.
Given the limited data available (the screenshot above was supplied by the user himself), it appears that the bad guys in this case set up some kind of fake Wells Fargo profile. Whether they had actually determined that the mark did in indeed have a Wells Fargo account we cannot say, given the limited amount of data available. Inasmuch as LinkedIn has implemented restrictions on the use of InMail to thwart its exploitation for mass spam attacks, it struck us as "interesting" that whoever was behind this InMail phish had managed to target an actual Wells Fargo account holder.
The very next day we encountered the same phish again -- but this time delivered to an email account outside of LinkedIn (and reported to us by a customer using the Phish Alert Button):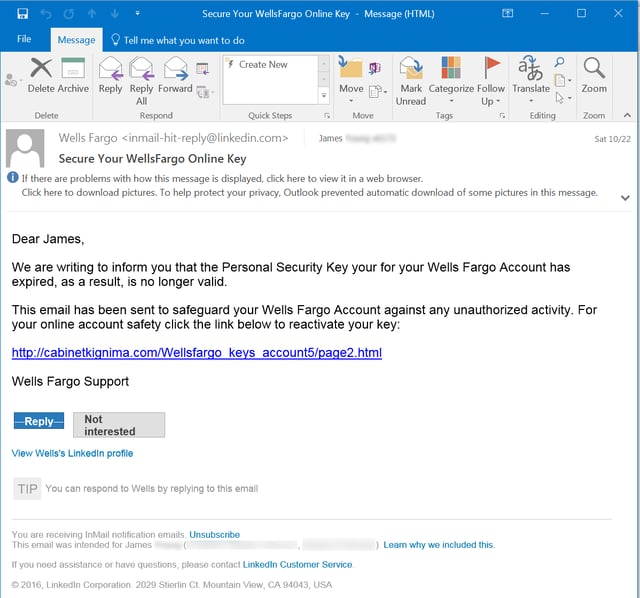
This social engineering attempt is a word-for-word match for the InMail phish we had seen the day before. The malicious link (still working at that point) led to the same credentials phish landing page.
Headers on this email were, shall we say, "interesting." The first thing we noticed was that the email had indeed been delivered through LinkedIn:
Received: from mailb-ae.linkedin.com (mailb-ae.linkedin.com
[108.174.3.149]) (Using TLS) by us-smtp-1.mimecast.com with ESMTP id
us-mta-118-wFQw6xtFNOeLlwhpHORIWw-1; Sat, 22 Oct 2016 18:33:45 -0400
Other data in the headers confirmed that this phish had originated from within LinkedIn:
X-LinkedIn-Class: INMAIL
X-LinkedIn-Template: email_inmail_initial_single_01
X-LinkedIn-fbl:
m2-aszpqrago067ve55ghwd5ifz5vk6ktqv11d0wzmpc7kgw0x6un2596myq0exkir0yvpeay8qttz9zsuf9rt94hcmzprrm9p5mhcll1
X-LinkedIn-Id: 8cj3m-iuls6u15-v5
List-Unsubscribe:
<https://www.linkedin.com/e/v2?e=8cj3m-iuls6u15-v5&t=lun&midToken=AQHpWZLK4QIuBA&ek=email_inmail_initial_single_01&loid=AQHGOsgMLUjQ6AAAAVfuhlpMG9oXbSeWFY9jJELI8ZUGnkgjujC-P_FxhkAidcIE_BjrAVEmuMuz5b3aTAnN&eid=8cj3m-iuls6u15-v5>
Require-Recipient-Valid-Since: [REDACTED];
...as did the URLs used for the several links included in the footer of this email ("Reply," "Not interested," "View Wells's LinkedIn profile"):
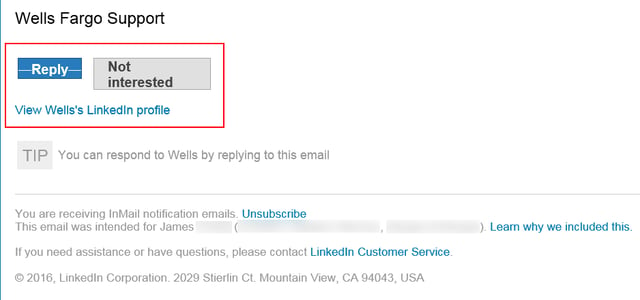
Those URLs were obviously auto-generated by LinkedIn itself when the malicious actors used LinkedIn's messaging features to generate this phish, which hit the external email account of the mark (as opposed to his InMail box, as was the case in the first phish discussed above).
As before, we talked to the targeted user and he confirmed that he, like the first victim, had a Wells Fargo account. He also reported that he had a number of connections within LinkedIn to Wells Fargo employees.
Given that this second phish was also generated by a fake Wells Fargo profile -- undoubtedly the same account used to generate the InMail phish seen by the first victim -- we decided to click the "View Wells's LinkedIn profile" link. By the time we clicked, however, LinkedIn had already taken the account down:
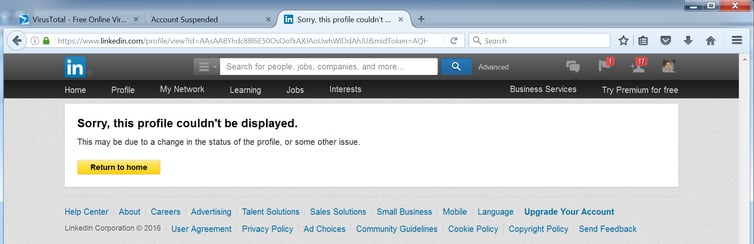
Known Unknowns
It is to LinkedIn's credit that it so quickly disabled an obviously fake Wells Fargo profile used to phish LinkedIn users. That said, without the opportunity to examine this fake or bogus profile, we are unable to identify the precise means through which malicious actors managed to target and then phish likely Wells Fargo account holders using LinkedIn's own messaging features.
Clearly the bad guys set up a bogus Wells Fargo profile on LinkedIn. How they managed to identify and target likely Wells Fargo account holders is unknown. Also unknown is how they managed to generate a credentials phish email using a custom text (as opposed to one of LinkedIn's own canned email templates) and delivered through LinkedIn's own platform to external email addresses. We strongly suspect, though, that these attacks leveraged fake Connection Requests to build the reputation of fake Wells Fargo Profile and generate first and second level connections within LinkedIn to open doorways through which these attacks could be launched. What we don't know is the precise steps through which the bad guys actually managed to accomplish this or the type of account used to do it.
Known Takeaways
What is abundantly clear from this series of Wells Fargo phishes is that LinkedIn has become a viable platform for launching phishing attacks against users who have been targeted for their connections to a high profile financial institution. LinkedIn is now valued not only for its wealth of data on potential targets for all manner of scams and targeted phishing attacks but for its usefulness in generating emails that leverage LinkedIn's own reputation to bypass security solutions implemented by organizations worldwide.
Given the restrictions surrounding the use of LinkedIn's messaging features, we doubt that these kinds of leveraged attacks will ever achieve high volume distribution. But LinkedIn's inherent reputation does lend itself to launching very targeted attacks against corporate lucrative targets. A credentials phish, as we saw in these two cases, is the most basic of phishing attacks. Having proven LinkedIn's viability as a phishing platform, we expect malicious actors will find creative ways to exploit LinkedIn's data and messaging features to launch still more dangerous and creative attacks against LinkedIn users in the near future.
End users need to be trained to recognize these types of targeted attacks. Old-school awareness training simply does not cut it anymore. Users need to be stepped through new-school security awareness training which provides on-demand interactive modules combined with frequent simulated phishing attacks. Start your awareness program with a free one-time simulated Phishing Security Test.
Don't like to click on redirected buttons? Copy and pastethis link into your browser:
https://www.knowbe4.com/phishing-security-test-offer





