KnowBe4 is expanding fast, we now have 120 employees and we just hired a new controller late May to help out our very busy CFO. Part of the KnowBe4 onboarding is getting through our internal training line-up and then updating your LinkedIn profile, so that happened in the last few weeks.
So guess what, Camille walks up to me and asks: "Did you need me for anything? Did you send me an email?" I'm looking at her somewhat puzzled and say: "No?" She answers: "In that case I just got spoofed".
My obvious first reaction was that our CISO was sending her a phishing security test, as she is a high-risk employee in accounting. But rather being safe than sorry, I got interested, walked up to her desk and had a look at the two emails she just received, one at 12:23 pm and the second one at 1:30 pm.
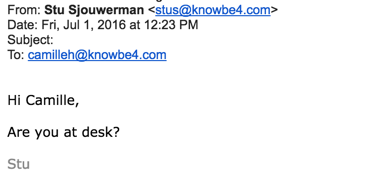
And then, a while later she got another one, purportedly from "me":
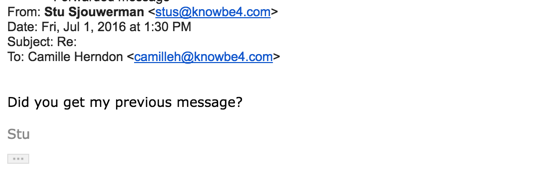
After the second one she stepped up to me. I had a look at the headers. Lo and behold, this was a real CEO Fraud attempt, just a few weeks after she had updated her LinkedIn account. There would have been no other way to get that information so fast online.
The bad guys apparently have this somewhat automated, and get alerts when a new target starts working at a company they are interested in. However, they did not do enough homework, because we step own employees through our own security awareness training and she did not reply and spotted the CEO Fraud attack correctly. Very well done Camille.
CEO Fraud on the rise
No industry is immune to this type of scam. Recent figures reported by the FBI show that in the past 3 years, a staggering 14,032 victims in the US have lost a total of $960 million to cybercriminals due to what they call Business E-mail Compromise. That is a 1,300% increase in reported instances since January 2015!
If those numbers aren't enough to convince you, take a look at some recent news not just in the US but around the world. In January, aerospace company FACC lost around €50 million due to what they call the "Fake President Incident”, their CEO and CFO were fired as a result. A still undisclosed American company lost nearly $100 million due to CEO fraud in April and has since recovered about 75% of that, leaving the total loss around $25 million. As you may guess this doesn't look good so companies try to keep these instances out of the mainstream news as much as possible.
It is not just small companies that need to stay vigilant, companies of all sizes are targeted on a regular basis. All types of employees run the risk of being victims of social engineering which is only the beginning. Hackers are spending more and more time researching employees and companies before they attack in hopes that they will get what they're after.
Lesson learned
Make sure that you step high-risk employees in Accounting, HR, C-level execs and anyone that handles confidential information through their awareness training as an early part of their onboarding procedure.
After initial security awareness training there are a few things to keep in mind to protect your business. A big theme when it comes to email fraud is the sender usually requests the recipient not to tell anyone and to act now. That should be your first red flag. ALWAYS check who the email is actually coming from. Hitting reply on the email (without actually replying) will show you where the email is coming from. If it just doen't sound like the sender, that should also tell you the email is not legitimate.
Can hackers spoof an email address of your own domain?
Are you aware that one of the first things hackers try is to see if they can spoof the email address of your CEO? If they are able to commit "CEO Fraud", penetrating your network is like taking candy from a baby.
Would you like to know if hackers can spoof your domain? KnowBe4 can help you find out if this is the case with our free Domain Spoof Test. It's quick, easy and often a shocking discovery. Find out now if your email server is configured correctly, many are not!
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.knowbe4.com/domain-spoof-test/





