 The New Verizon DBIR is a treasure trove of data. As we covered here, and here, people are one of the most common factors contributing to successful data breaches. Let’s drill down a bit more in the Social Engineering section.
The New Verizon DBIR is a treasure trove of data. As we covered here, and here, people are one of the most common factors contributing to successful data breaches. Let’s drill down a bit more in the Social Engineering section.
They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.
"The most convincing social engineers can get into your head and convince you that someone you love is in danger. They use information they have learned about you and your loved ones to trick you into believing the message is truly from someone you know, and they use this invented scenario to play on your emotions and create a sense of urgency. Figure 35 shows that Pretexting is now more prevalent than Phishing in Social Engineering incidents. However, when we look at confirmed breaches, Phishing is still on top."
A social attack known as BEC, or business email compromise, can be quite intricate. In this type of attack, the perpetrator uses existing email communications and information to deceive the recipient into carrying out a seemingly ordinary task, like changing a vendor's bank account details. But what makes this attack dangerous is that the new bank account provided belongs to the attacker. As a result, any payments the recipient makes to that account will simply disappear.
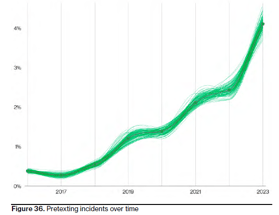
BEC attacks have nearly doubled
It can be difficult to spot these attacks as the attackers do a lot of preparation beforehand. They may create a domain doppelganger that looks almost identical to the real one and modify the signature block to show their own number instead of the vendor's.
Attackers can make many subtle changes to trick their targets, especially if they are receiving many similar legitimate requests. This could be one reason why BEC attacks have nearly doubled across the DBIR entire incident dataset, as shown in Figure 36, and now make up over 50% of incidents in this category.
Financially Motivated External Attackers Double Down on Social Engineering
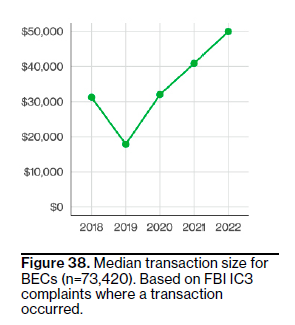
Timely detection and response is crucial when dealing with social engineering attacks, as well as most other attacks. Figure 38 shows a steady increase in the median cost of BECs since 2018, now averaging around $50,000, emphasizing the significance of quick detection.
However, unlike the times we live in, this section isn’t all doom and gloom. Law enforcement has a process to work together with banks to help recover money stolen from BEC attacks. Over half of the victims have been able to get back at least 82% of the money that was stolen.
 [RELATED READING] Social Engineering Breaches Double, Leading to Spiraling Ransomware Costs
[RELATED READING] Social Engineering Breaches Double, Leading to Spiraling Ransomware Costs
"Social engineering incidents have almost doubled since last year to account for 17% of all breaches, according to Verizon's 2023 Data Breach Investigations Report (DBIR) released June 6 (which analyzed more than 16,312 security incidents, of which 5,199 were confirmed data breaches).
The report noted that this preponderance of human fallacy within incidents comes along with findings that the median cost of a ransomware attack has doubled since last year, reaching into the million-dollar range. The evidence taken together points to a gaping need for organizations to get in control of the security basics — or else face a spiraling cycle of inflation when it comes to data breach costs." Full article in DARKReading
 Here's how it's done:
Here's how it's done:




