 People are one of the most common factors contributing to successful data breaches. Let’s dive in deeper into the latest Verizon Data-Breach Investigations Report (DBIR) to find out how and why users are a contributor to the problem.
People are one of the most common factors contributing to successful data breaches. Let’s dive in deeper into the latest Verizon Data-Breach Investigations Report (DBIR) to find out how and why users are a contributor to the problem.
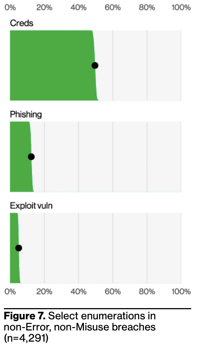
In this year’s newly-released Data Breach Investigations Report, they outline how attackers gain initial access to an organization: “The three primary ways in which attackers access an organization are stolen credentials, phishing and exploitation of vulnerabilities.”
In the figure below, it’s evident that the first two are the primary problem:
Source: Verizon
In fact, use of stolen credentials tops the list of action varieties in data breaches. And while this and phishing are categorized separately in the report, they are intertwined tightly.
According to the report, approximately 90% of initial access involves social engineering and people. Putting this together, it becomes evident that social engineering is used primarily to obtain credentials from a victim that has no idea they are being scammed.
To put it bluntly – your organization needs to ensure it doesn’t become a victim of a credential harvesting attack. Otherwise, you may just become part of the statistics in the report.
Security Awareness Training is key in helping to reduce the likelihood users will fall for social engineering scams – whether in email, on the web, in a text, etc. – designed to harvest credentials (or any other malicious outcome).
In essence, Security Awareness Training is your countermeasure to the “Human Element.”
 The Training Preview includes:
The Training Preview includes:




