The long-standing argument over whether or not to pay may have come to an end, with a resolution from the U.S. Conference of Mayors calling on cities to not pay up.
Unless you’ve been under a rock, you’ve heard the reasons for and against paying the ransom demand during a ransomware attack. Those in for paying the ransom cite lower remediation costs (as would have been the case in the recent City of Baltimore attack, which will cost the city over $18M compared to the initial ransom of just $76K), and faster remediation time (the average ransomware attack spans 9.6 days). It’s been demonstrated that decryption keys provided upon payment of the ransom work to decrypt anywhere from 87%-100% of the encrypted data.
Those against paying cite that this will only incentivize more attacks from more cybercriminals and won’t guarantee an ability to recover. I’d add that just because you’ve got the decryption key, doesn’t mean that you’ve rid your environment of any additional malware that made it through either.
The resolution, sponsored by Baltimore mayor, Jack Young, establishes that the conference of mayors vehemently opposes paying the ransom:

So, if you subscribe to the viewpoint of the mayors, what should you do?
- Have isolated backups – lots of them. Modern variants of ransomware are even nasty enough to search out for backup files and delete them, disable Windows’ Volume Shadow Copy service, and even lever backup software APIs to delete backups stored elsewhere. It’s nasty stuff. So, follow the “3-2-1 Backup Rule” and make sure you have backups in the cloud/offsite where ransomware can’t touch them. Without paying the ransom, you’re either going to restore backups or start manually installing systems.
- Put up a layered defense – you’ve got to keep ransomware from infecting the initial machine; once you do that, it’s game over for the attack. Having a layered defense that includes scanning email, the web, DNS, and the endpoint is the minimum you should have in place.
- Secure the user – unless it was an RDP attack, your users are almost always involved; they need to be present to click on the malicious link or attachment to initiate the ransomware badness. Educating them with continual Security Awareness Training with phishing testing reinforces the need for the user to participate as part of your defense, teaching them to report phishy emails to Incident Response with one click, and avoid the attack altogether.
Even if you are in the “pay the ransom” camp, you should still follow the steps outlined above, as 8% of your data not being recoverable can amount to a material portion of your critical data.
Whether you agree with the mayor’s conference or not, ransomware remains an ongoing problem and is a question of “when” and not “if”. So be ready - ransom or not.
Pay or Not Pay the Ransom? What’s Your Opinion?
 As an IT pro, you did not sign up for this, but you are finding yourself in the trenches of a slow cold cyber war between nation states. Ransomware is one of the tactics being used. The debate over whether to pay or not to pay the ransom once your system is encrypted is still in full swing. There are arguments on either side of the question. .
As an IT pro, you did not sign up for this, but you are finding yourself in the trenches of a slow cold cyber war between nation states. Ransomware is one of the tactics being used. The debate over whether to pay or not to pay the ransom once your system is encrypted is still in full swing. There are arguments on either side of the question. .
In many cases, the costs of not complying with the demand can cost many millions more than paying and may not be a realistic option for some smaller cities. And once your system is compromised with ransomware there may be residual malware left behind and the only way to totally reduce that risk is to build back up from bare metal. Discuss this nettlesome issue at KnowBe4's Hackbusters Forum:
https://discuss.hackbusters.com/t/pay-or-not-pay-the-ransom-whats-your-opinion/4416
Free Ransomware Simulator Tool
How vulnerable is your network against ransomware attacks?
Bad guys are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s "RanSim" gives you a quick look at the effectiveness of your existing network protection. RanSim will simulate 15 ransomware infection scenarios and 1 cryptomining infection scenario and show you if a workstation is vulnerable.
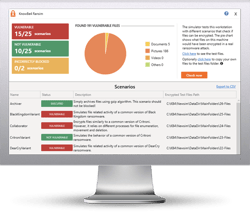 Here's how it works:
Here's how it works:
- 100% harmless simulation of real ransomware and cryptomining infections
- Does not use any of your own files
- Tests 16 types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





