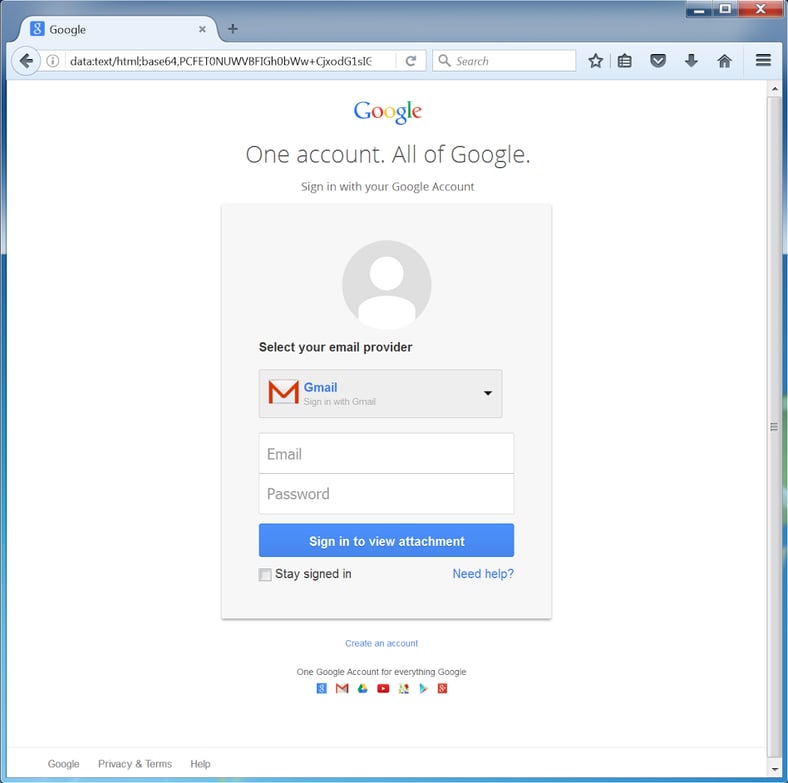
The other thing of note here is that this particular phish spoofed a security alert notice from Google -- just the kind of attack that we discussed in this blog post.
In Podesta's case the bad guys used a bit.ly link -- something else we see all the time. And the landing page for the credentials phish probably looked something like the below...
- Using a terrible password to begin with
- Re-using that password for multiple sites/accounts
- Sharing the password with assistants
- Asking an assistant to email him his password when he forgot it
- Not turning on two-factor authentication
- Not changing passwords after one account was known to be compromised
Don't be that guy and train your users within an inch of their lives to "not be that guy" either...

Free Phish Alert Button
Do your users know what to do when they receive a suspicious email?
Should they call the help desk, or forward it? Should they forward to IT including all headers? Delete and not report it, forfeiting a possible early warning? KnowBe4’s Phish Alert button gives your users a safe way to forward email threats to the security team for analysis and deletes the email from the user's inbox to prevent future exposure. KnowBe4's free Phish Alert for Outlook is an add-in you can download and deploy at no cost.





