By Eric Howes, KnowBe4 Principal Lab Researcher.
Yesterday we spotted an unusual phishing email that we'd like to share with readers. If nothing else, it tells us that the increased security-related customer messaging adopted by many online service providers has paradoxically provided malicious parties of all kinds with new material to exploit when social engineering users.
First, a bit of background, though.
The Good Guys Step Up Their Game
Over the past few years online service providers like Microsoft, Facebook, Twitter, and Paypal (among others) have been stepping up their security game by messaging customers when they detect unusual or worrisome activity on their users' accounts. Consequently, ordinary users have been seeing an increased number of emails and other types of security-related messages from service providers.
Here, for example, is a typical email notice from Google that Gmail users can expect to see when they log in to their accounts from new devices, browsers, or locations:
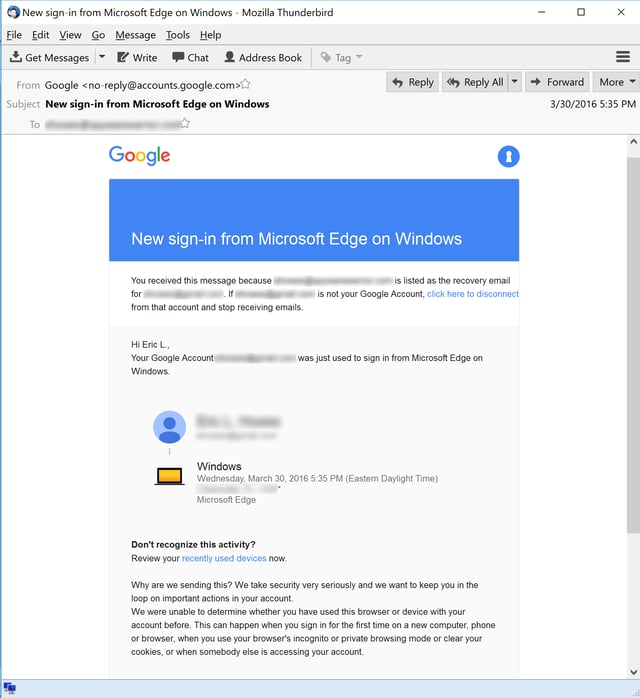
And here's a Twitter notification warning one user over a potentially compromised account:
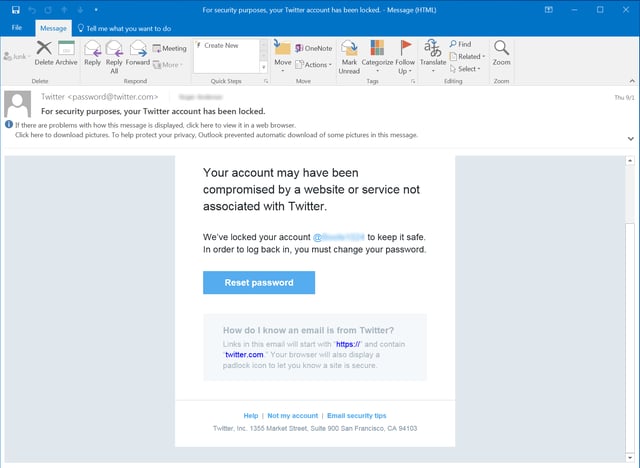
Microsoft sends similarly worded notices when it detects what it deems "unusual sign-in activity" on user accounts:
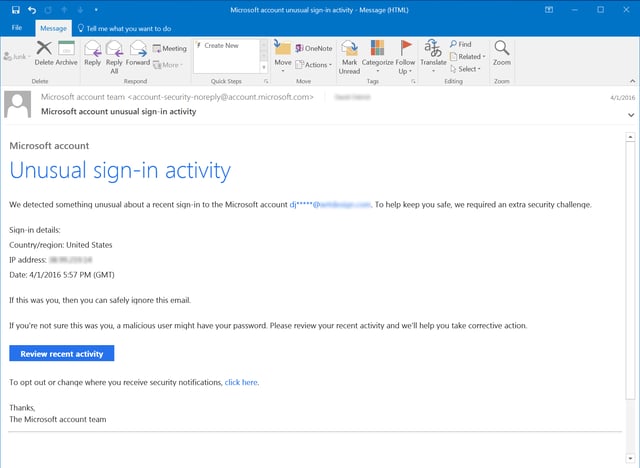
And then there's the hair-raising security warning that one Yahoo Mail user encountered earlier this year.
The Bad Guys Move In
To no one's surprise the bad guys have been exploiting this increased security messaging for their own malicious ends, sending copycat/lookalike security messages designed to exploit user confusion, ignorance, and laziness. Many of the fake security-related emails that we seen have been predictably bad -- plagued with unprofessional design and graphics, poor spelling and grammar, and unbelievable claims that should alert anyone who bothers to look carefully and skeptically.
We have seen plenty of fake security notice phishes that could prove plenty convincing to ordinary users, however. Consider this fake Paypal security notice warning potential marks of "unusual log in activity" on their accounts:
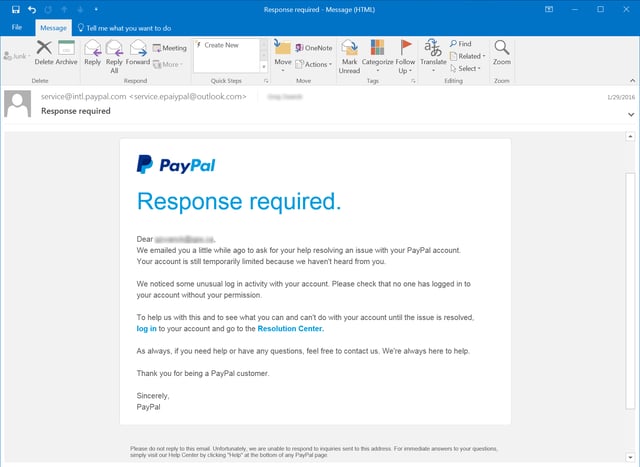
As you might expect, the provided links whisk clueless clickers to a credentials stealing web site. Users foolish enough enter a username and password on that site really will start to see "unusual log in activity" on their Paypal accounts.
And here's a fake Microsoft notice, almost identical in appearance to the example provided above of an actual notice from Microsoft concerning "Unusual sign-in activity":
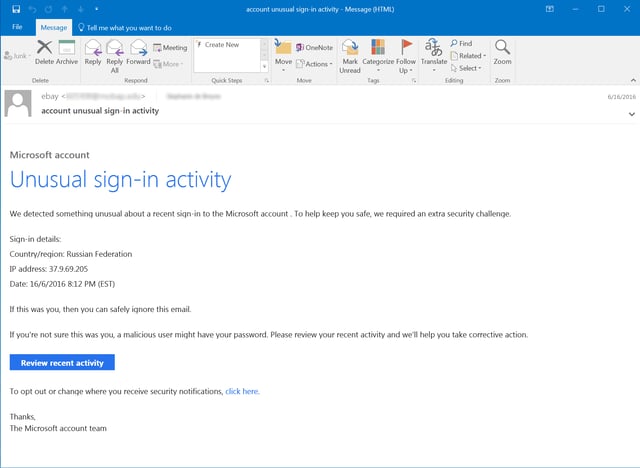
As with the fake Paypal notice, the provided link in this email ("Review recent activity") leads to a credentials phish.
Scam Artists Take Notice
Tech support scams have plagued users for years. Typically tech support scammers have trolled for victims via search advertising, aggressive pop-ups at dodgy web sites, and cold call phone campaigns in which the bad guys pose as tech support personnel from Microsoft or recognized hardware vendors like Dell.
In response, a number of companies have been cracking down on tech support scam advertising. Bing recently went so far as to ban third-party tech support ads.
Determined to hang on to a reliable source of ill-gotten revenue, though, scam artists have developed an array of new tricks to hook unsuspecting users. We encountered yet another one of those tricks just yesterday:
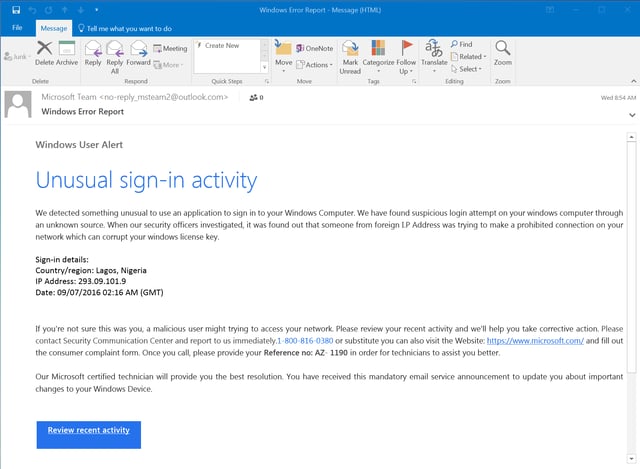
Yes, it's the same "Unusual sign-in activity" text that we saw above in two different versions (one legit, one malicious). While malicious, this one is unusual, though, in that it points users to a 1-800 number instead of kicking users to a credentials phish, as we saw in the previous malicious version of this email.
This phish also provides victims with a link to a remote tech support site -- presumably to be used after victims call the 1-800 number and begin working with the fake tech support personnel on the other end.
Put simply, this phish is merely another gateway to a tech support scam. Where tech support scam artists previously directed victims to phone-based tech support scams through browser pop-up messages...
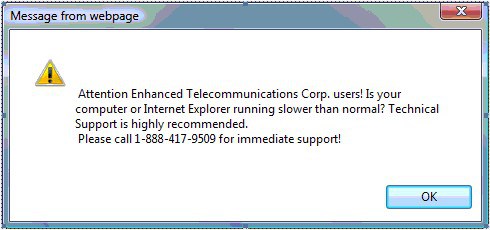
...web-driven pop-ups...
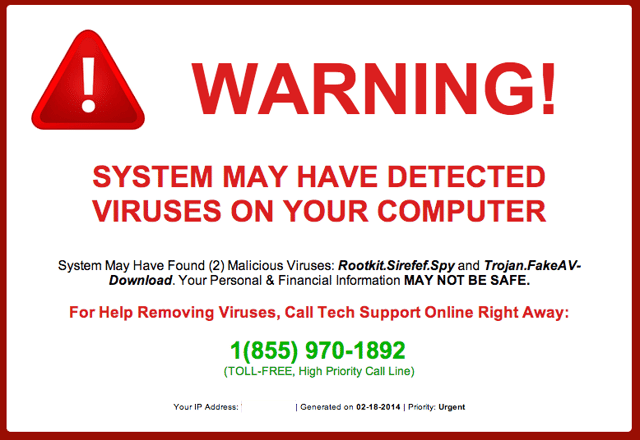
...and full page web ads...
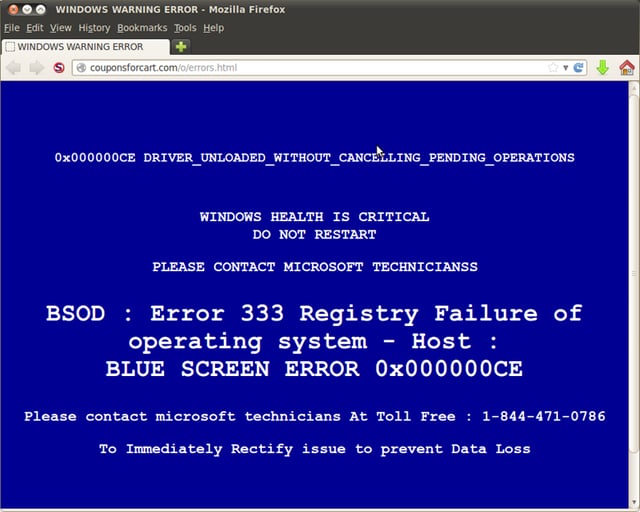
...they are now exploiting the same attack vector -- phishing emails spoofing real security messaging from online services -- as other malicious actors who routinely spring credentials phishes and malware on unsuspecting users.
We've already seen evidence that this particular phish is working. Here's one user complaint we dug up via a search on the 1-800 number used in the phish:
I have received an email from Microsoft Team telling me that there is suspicious activity on my account coming from Nigeria. When I try to contact Microsoft I have been sent to 20 different voice systems and have not - after an hour- been able to talk with any one or find out if this is actually from Microsoft. Is there any one who can tell me what this is about? I am totally frustrated with Microsoft as it is impossible to talk with a live human being - but rather you get passed from one robot to the next. GET YOUR ACT TOGETHER MICROSOFT...
We strongly suspect that users who don't manage to get a live person when they call ("All of our support personnel are currently assisting other customers. Please stay on the line...") will have their phone numbers flagged for followup calls.
Final Thoughts
It's worth noting that this particular scam, in its current phish-driven form, could easily be adapted to target employees working in corporate environments where tech support is remotely provided, whether by native IT personnel working at other company locations or by a Managed Service Provider.
In such cases, clueless employees could easily be tricked into assisting malicious actors establish remote desktop connections right through your firewall and straight to employees' desktop PCs or laptops. And once the bad guys are inside the wire, all bets are off.
Effective, new-school security awareness training will head this off at the pass.
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
For instance, KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.

PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo




