 By Eric Howes, KnowBe4's Principal Lab Researcher
By Eric Howes, KnowBe4's Principal Lab Researcher
Over the past six to nine months .DOC and .JS file attachments have dominated the news surrounding the rise in phishing attacks. The reasons are obvious and understandable: those two file types (usually packaged in .ZIP files) are commonly used to deliver extremely dangerous ransomware and banker trojans. Your organization's employees should be wary of another file type, however, that we are seeing delivered as a malicious attachment: .HTML files.
Although not nearly as prevalent as .JS and .DOC file attachments, .HTML attachments are common enough -- and dangerous enough -- that we decided to review how the bad guys present these attachments to unsuspecting users and trick them into coughing up data that could be used to exploit your organization. Note that these phishing emails are reported to us through the KnowBe4 Phish Alert Button, which means they were missed by all existing security layers.
All the example HTML attachments discussed below were seen within the past three weeks.
Why Use .HTML Attachments?
So far as we can tell, .HTML attachments have two main advantages that the bad guys exploit when using them in phishing attacks:
1. Reduced chance of AV detection
Carefully crafted .HTML files can reduce the chances that phishing emails sporting those attachments will be stopped by email security software or devices. While .EXE and Office files (.DOC, .XLS, etc.) pose obvious threats in a Windows environment and have a long history of being used in malspam (malicious spam email), .HTML files are not commonly associated with email-borne attacks -- at least not recently (several years ago they were being used to deliver malicious Javascript). Moreover, .HTML files can be used to embed URL redirects to evade AV scanners that check only URLs that appear in the bodies of emails. HTML files can also be used to deliver obfuscated web pages (usually base64 encoded) that might slip past even scanners that do check .HTML attachments.
2. User familiarity
Although your users and employees may not recognize the potential threat of .HTML attachments, that doesn't necessarily mean they aren't familiar with them. HTML attachments are commonly used by banks and other financial institutions to deliver secure documents and messages as well as to enable users to conduct banking business in a secure environment.
Many of your users will have seen emails like this (Cisco Registered Envelope Service). Note the .HTML attachment.
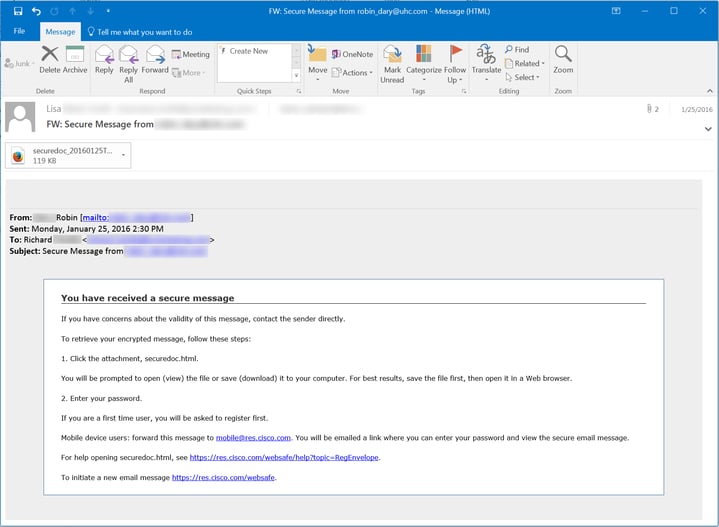
If your organization is in the financial services industry, or if your employees regularly interact with financial institutions during the course of their job, it's likely that your employees may view .HTML attachments as simply routine and non-threatening. And there-in lies the danger.
The Danger of .HTML Attachments
While .HTML file attachments have been used to deliver malcode (usually via embedded Javascript) to endpoints, the .HTML attachments we've seen over the past six months have typically been used for that lowliest and most common of phishing attacks: the credentials phish. In a credentials phish users are tricked into believing they are being asked to log in to a trusted online institution or web service. The login form they see, though, is fake, and the usernames and passwords they enter are quietly being harvested by the bad guys for future exploitation.
Let's take a look at the three most common ways that users and employees are social engineered into coughing up secure credentials.
1. Online banking
This is the granddaddy of phishing, and it shouldn't come as any surprise that the bad guys use .HTML attachments to spoof bank login pages, given that banks themselves are big users of .HTML attachments. Bank credentials phishes are a familiar affair. The email body warns recipients of some urgent problem or issue requiring them to log in to their online bank accounts. Strangely, the HTML pages used for these phishes more often resemble the targeted bank's home page than any actual HTML attachment used by a bank.
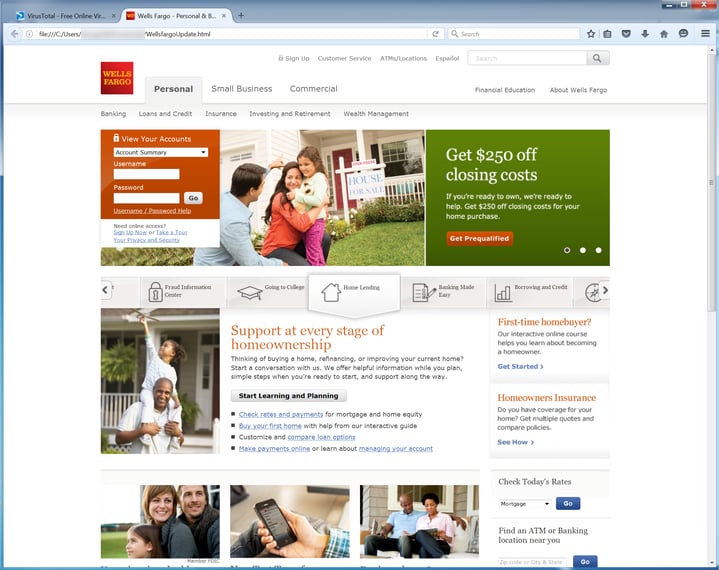
We do occasionally see malicious .HTML attachments that loosely resemble legitimate bank .HTML attachments, though. Compare this spoofed Navy Federal attachment ...
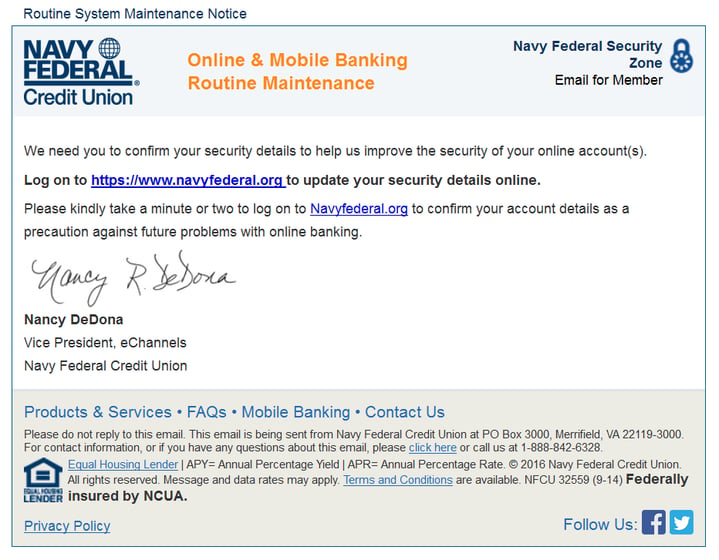
...with an actual .HTML attachment from Chase bank:
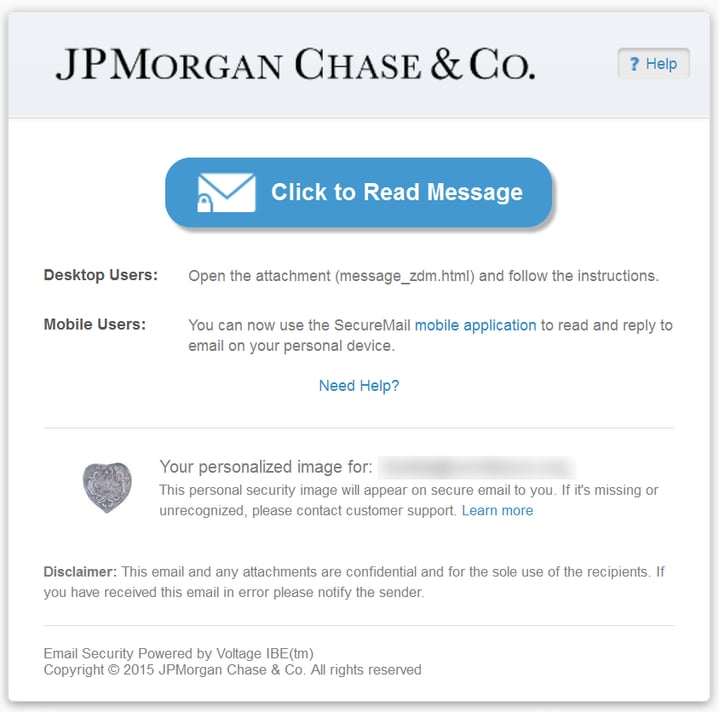
2. Popular online services
The bad guys also spoof popular online services, creating login pages that are well nigh indistinguishable from the real thing. Here's a fake Google login page:
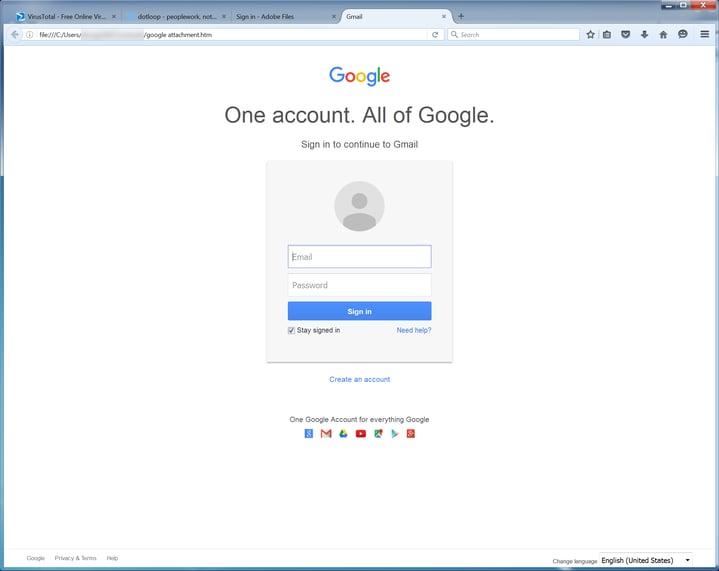
How many users will be savvy enough to realize that the HTML attachment they opened might not actually be a safe means to log in to their Google account?
Not all spoofed login forms are service or brand specific, however. We have been seeing an increasing number of brand-agnostic email login forms, delivered both as .HTML attachments and live online web pages. Although this .HTML attachment prominently features the Google brand, it advertises to potential victims that the form will accept credentials for any manner of email address or account:
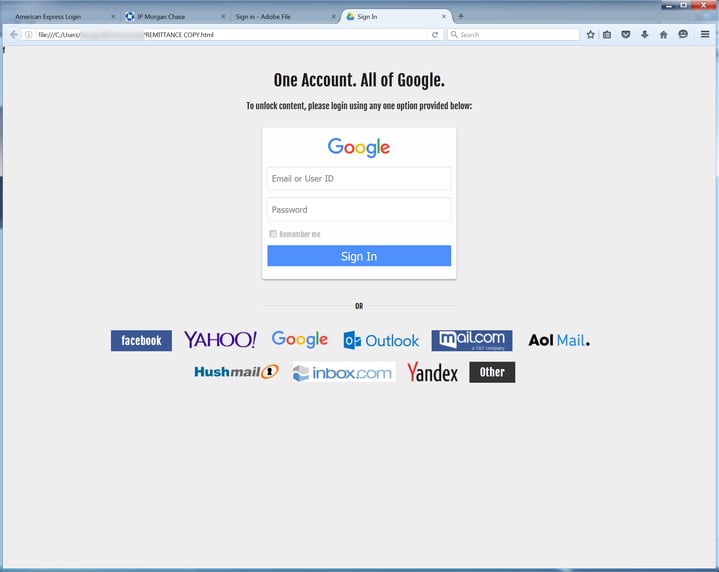
Users could easily use their work email logins, thus opening a door directly into their employers' corporate networks.
3. Secure doc/message
As we recently noted in this space, the bad guys often use the ruse of providing a secure document or message delivery service to trick users into opening potentially malicious file or coughing up secure credentials. The two most common approaches used to trick users into supplying secure credentials to access a "secure doc" of some sort are the Adobe ID login:
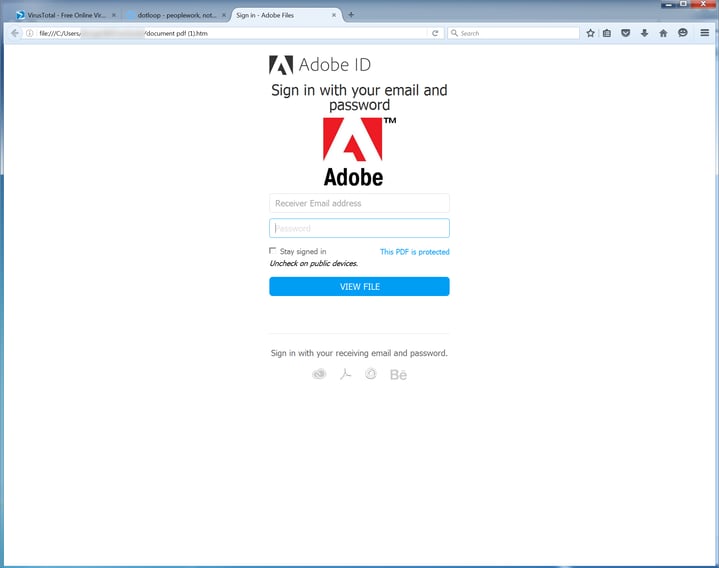
...and a version of the brand-agnostic web form that we saw just above:
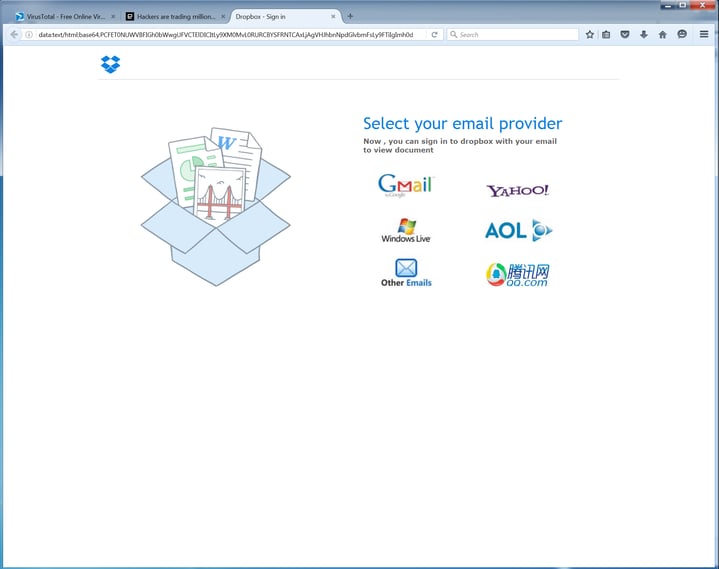
Note the text in the above example telling users they are logging into Dropbox to access the promised document. And the "Other Emails" option means the bad guys are only too happy to accept users' login credentials for their place of employment.
Your Best Defense: Educating Users
Untrained users who aren't technically savvy often work with very simplistic mental models of how the online threat landscape operates. Thus, while many users may finally recognize that .EXE and .PDF files are potentially dangerous or "bad," those same users will likely regard .HTML attachments as harmless and "good." If your employees persist in this thinking, they may well find themselves giving away the keys to the kingdom -- your kingdom.
Your employees need to be educated about the wide variety of potentially malicious email attachments -- including .HTML attachments -- they may encounter in their inboxes. The HTML attachments we've shown in this blog piece are not widely detected by anti-virus scanners, and it's very likely they will end up in front of your users.
Regular Security Awareness Training is critical to ensuring that your employees recognize and correctly respond to the actual threats they will encounter. Find out how affordable this is for your organization and be pleasantly surprised.
If you do not like to click on redirected buttons, here is a link you can cut&paste:
https://info.knowbe4.com/kmsat_get_a_quote_now





