 In this Scam Of The Week we are warning against a new wave of phishing scams. In the industry this is called the "secure doc" theme. It's getting very popular with the bad guys. We see a spike of malicious ones coming in at the moment.
In this Scam Of The Week we are warning against a new wave of phishing scams. In the industry this is called the "secure doc" theme. It's getting very popular with the bad guys. We see a spike of malicious ones coming in at the moment.
There are active phishing campaigns both using fake DocuSign and Secure Adobe PDF attachments trying to trap employees into opening them up. One user reported receiving one of these, with the "from" address spoofed as coming form their own attorney. That's a nasty form of spear-phishing.
It is also interesting to see that "secure doc" emails are one of the most misflagged categories of real emails that we see. Users have trouble figuring out whether a "secure doc" email is real or a phish -- even when dealing with secure document delivery services that are used/contracted by their own employers.
Send your users a heads-up
I suggest you send your users something like the following. Feel free to copy/paste/edit, and add a line or two how your own organization uses secure documents.
"I'm warning you about a recent wave of phishing attacks that try to trick you into opening "secure documents". You receive an email that looks like it is a DocuSign or EchoSign or Secure Adobe PDF notification with an important document attached that needs to be looked at.
The bad guys try to trick you into opening and clicking the attachments, and "enable macros" or "enable editing" but when you do, your workstation gets infected with malware or ransomware.
When you receive this type of document, which you did not ask for, and it's from someone you do not know, be very cautious and if you want to be sure, delete the email. If it looks like it comes from someone you do know, pick up the phone, use a phone number you know is valid (not a phone number from the suspicious email itself), and verify if this actually was sent by them and what the purpose was."
Here are some actual phishing attack examples. The bad guys use the "secure document" theme to trick users into clicking on dangerous links or attachments in three different ways:
1. Dangerous links in email bodies
The bad guys spoof legitimate secure document delivery services (such as those from Proofpoint, DocuSign, or Cisco) to trick users into clicking malicious links in the bodies of emails. In many cases what users encounter is a web page attempting to perform a login or email credentials phish. Note the fake DocuSign branding around the web page borders.
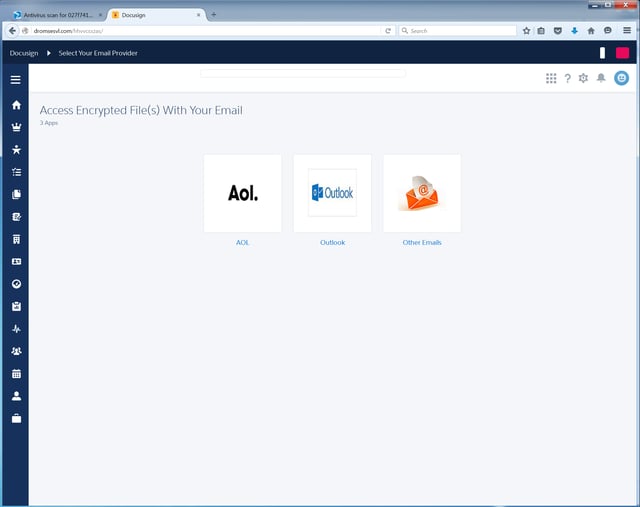
2. Dangerous links in PDFs
The bad guys also create elaborate PDFs designed to convince users that they are handling "secure" or PDF documents containing "protected" content that can only be accessed by clicking a particular button or word. In fact, what users are clicking on is a malicious link that will open in the browser.
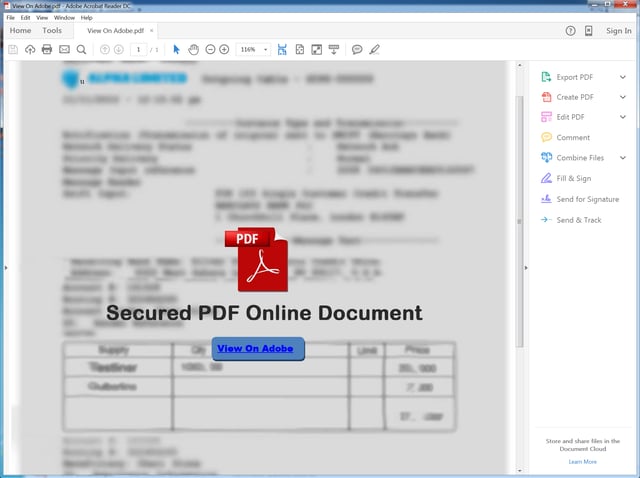
3. Malicious macros in Word Docs
The bad guys use a similar ruse to trick users into enabling macros after opening malicious Word Docs. Far from enabling allegedly "secure" content, what users are in fact doing is kicking off a download process that will likely result in the installation of Ransomware or a banker Trojan.
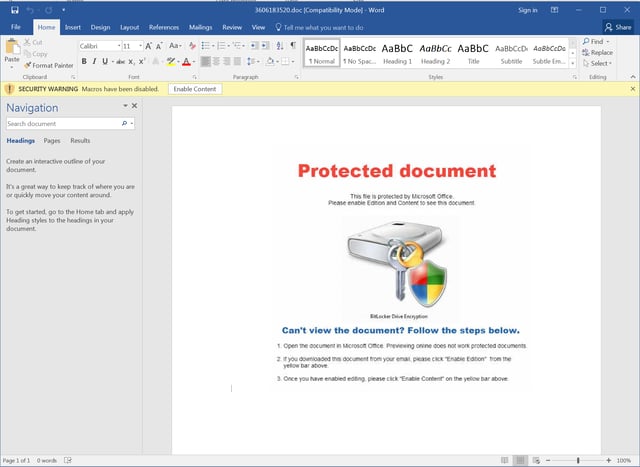
For KnowBe4 customers, here are the latest template updates and in which campaigns you can find them:
Online Services:
"You've received a Document for Signature": phish spoofs a DocuSign secure document delivery email.
"Please sign the contract": phishing email claims to deliver a secure Adobe PDF document for signing.
Banking:
"You've received a secure message": email spoofs a Cisco-delivered secure message from a financial institution.
Attachments with Macros:
"Re: lawsuit subpoena": email purports that a macro-laden Word doc attachment is in fact a legal subpoena.
Current Events:
"Alert: Prince Dies, See His Last Words On Video": fake news alert that claims to offer new information on the sudden death of the celebrity.
"Help! Disaster in Ecuador Leaves Hundreds Dead and Thousands Homeless": phishing email spoofs a Salvation Army appeal for donations to aid quake victims.
If you are not a KnowBe4 customer yet, send a (free) Phishing Security Test to your users, and find out what the Phish-prone percentage of your employees is. Often a very effective way to get IT security budget for new-school security awareness training.
Don't like to click on buttons with redirects? Cut and paste this link in your browser:
https://info.knowbe4.com/phishing-security-test-16
Related Pages: Phishing





