Over the past few years malicious actors have apparently decided that the future of phishing lies in exploiting trusted online services. Your users have undoubtedly seen the upshot of that decision in their inboxes: an endless stream of malicious emails pushing links to malicious content hosted on services like Dropbox, Sharepoint/OneDrive, Box, Constant Contact, and Evernote -- to name just a few. Now the bad guys have a new favorite online service to exploit: Microsoft Sway.
What is Sway?
Never heard of it? Or maybe you have heard the name but are still a bit fuzzy as to what it is? It's time to make introductions, because the bad guys are increasingly hip to Sway.
Released in 2015, Sway is an online service or productivity tool that you can think of as a cloud-based mashup of Publisher, Powerpoint, and Frontpage. Indeed, Microsoft encourages its use for many of the same kinds of things as Publisher and Powerpoint, particularly online newsletters and short marketing presentations.
The Wikipedia page on Sway usefully summarizes it like this:
"Office Sway is a presentation program and is part of the Microsoft Office family of products. Sway was offered for general release by Microsoft in August 2015. It allows users who have a Microsoft account to combine text and media to create a presentable website. Users can pull content locally from the device in use, or from internet sources such as Bing, Facebook, OneDrive, and YouTube."
Best of all, though,"[t]he program also provides native integration with other services, including YouTube, Facebook, Twitter, Mixcloud, and Infogram." Because what's the point of offering an exploitable online service to everyone with a Microsoft account if it doesn't integrate with social media and other online productivity tools?
During the last month or so customers using KnowBe4's free Phish Alert Button (PAB) have reported a rapidly rising number of phishing emails that leverage Microsoft Sway.
So far the bad guys have not yet fully exploited Sway's integration with other online services. (Give them time.) What they are doing, though, is skillfully deploying Sway to leverage the inherent trust that users place in Microsoft in order to trick them into clicking through to slick, convincing web pages that offer your employees an inviting opportunity to cough up their login credentials. Nice, huh?
Let's take a look.
Swaying Users to the Dark Side
The bad guys have been using Sway to support four different social engineering schemes. All lead to credentials phishes. (So far.)
1. Spoofed Microsoft Teams
As we documented in another recent blog post, malicious actors have recently warmed to yet another Microsoft offering: Microsoft Teams -- a competitor to Slack that has seen strong strong adoption growth among Microsoft customers who already use its Office 365 suite of productivity tools.
As it turns out, Sway is the perfect tool for rolling convincingly spoofed Microsoft Teams emails such as this one:
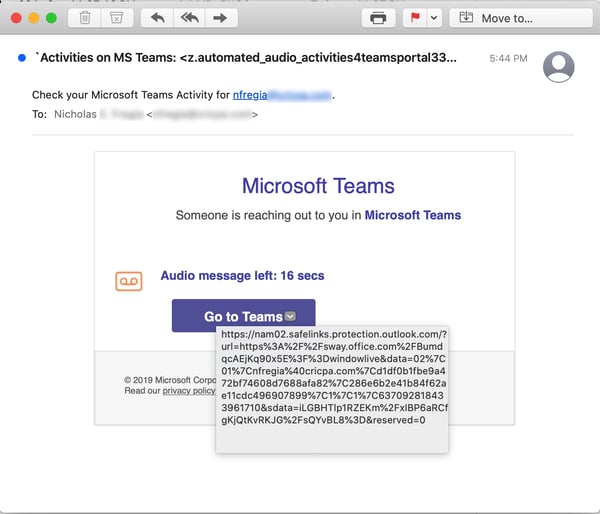
How many of your users would notice that the link in the above email points to Sway and not Microsoft Teams? And even if they did notice, would they even bat an eye given that the link still clearly promises to take users to a recognizable Office URL?
Office 365's Safe Links "time-of-click" URL protection service simply waves trusting users through to the landing page on Sway, which is simple and well-designed.
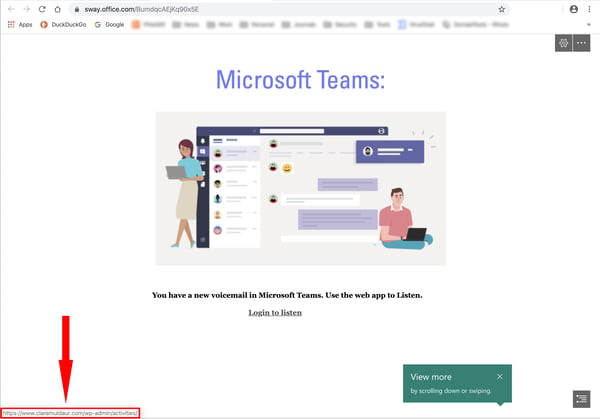
Somewhat predictably, the link here shuffles users on to a pixel-perfect spoof of Microsoft's own login page...
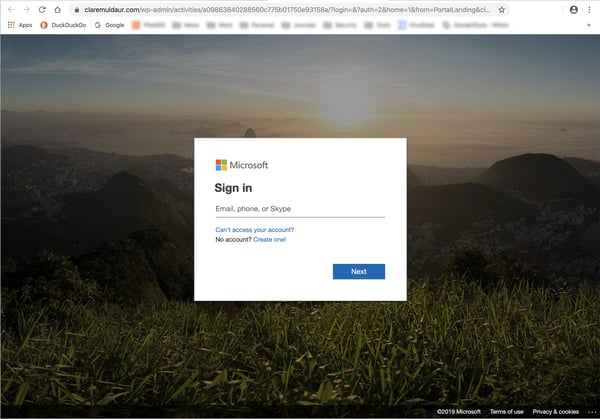
...which is hosted on a third-party web site.
What makes this phish particularly dangerous is the fact that the malicious actors behind it have constructed an almost perfectly seamless branding experience. From start to finish users are given every reason to believe that they remain within the familiar cocoon of Microsoft's Office 365 productivity suite.
2. Employee surveys
Malicious actors have also noticed that private companies and other organizations are increasingly turning to online surveys in order to ensure they remain on top of their employees' needs and expectations amidst an increasingly competitive job market.
Always happy to help, the bad guys are now doing surveys, too...
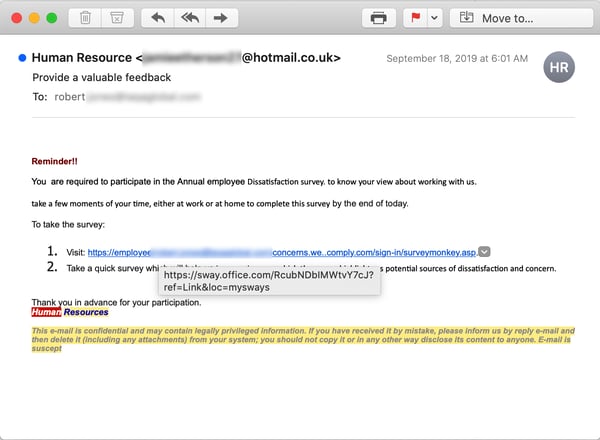
...though the malicious party behind this Sway-based phishing email apparently has a decidedly unique take on just what employee surveys ought to be measuring:
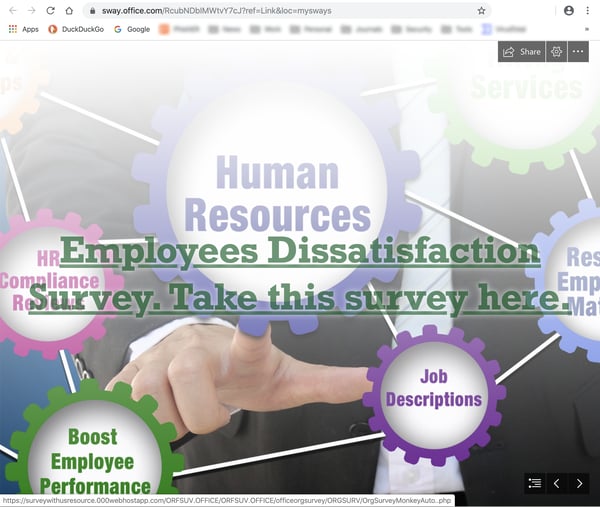
As before, the link takes users into the welcoming arms of a Microsoft credentials phishing page.
3. Fake file-sharing
Sway even turns out to be useful for that reliable old stand-by of phishers the world over: the fake file-sharing scam.
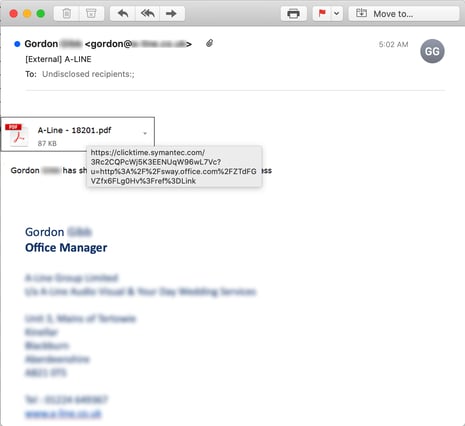
Though the above email is fairly minimalist -- relying on a fake file attachment graphic to do most of the heavy lifting -- a URL pointing to an Office.com web site certainly doesn't hurt to sell the con.
Users who take the bait will find themselves once again in familiar territory.
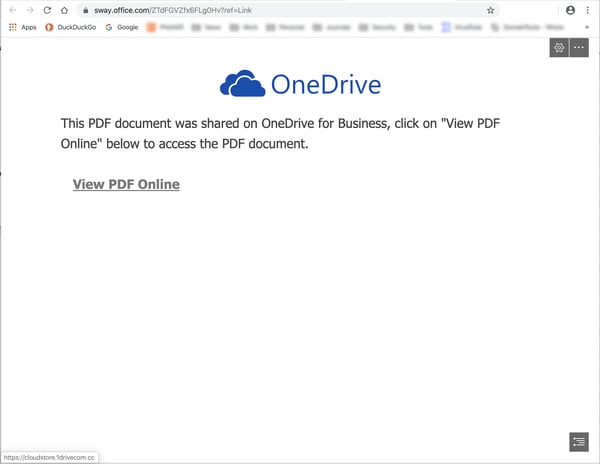
And note that the bad guys here have taken care to register a malicious domain that preserves the branding experience established on the preceding Sway page.
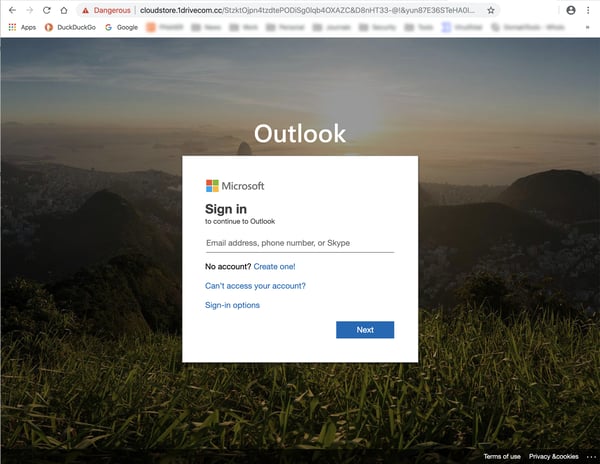
4. Fake voice mail
Proving itself an enormously flexible tool, Sway can even be pressed into service to handle another surging phishing genre -- the fake voice mail phish.
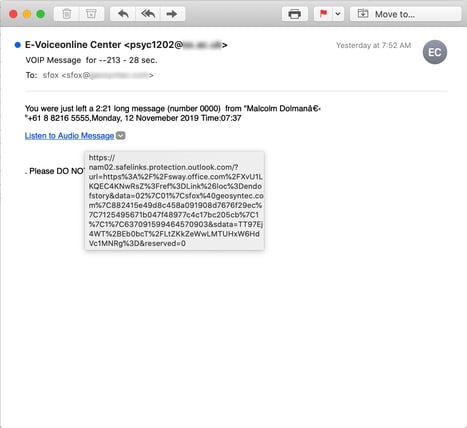
Having been conditioned to expect an "everything-and-the-kitchen-sink" design philosophy from Microsoft, how many users will simply shrug when they discover their voice mail is now apparently being handled through that new Microsoft thingie?
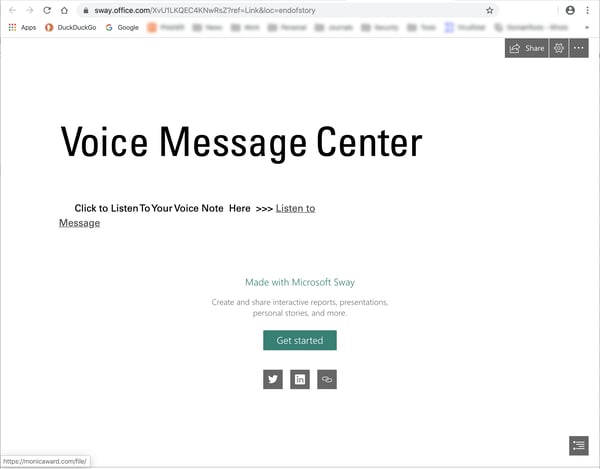
We won't bother showing you the inevitable spoofed Microsoft login page that follows (because you already knew it was coming).
5. Spam, Spam, Wonderful Spam
Even routine, otherwise low-rent spam can be spruced right up with a little Sway!
Yes, that email leads with a rather severe, bare bones pitch. Where it ultimately takes punters, though, is a decidedly more inviting front door to a cam babes scam.
Conclusion
Your users are inundated with fairly useless advice for staying out of trouble online. "Look out for typos and spelling errors." "Avoid untrusted web sites."
Such advice, however well-meaning, is useless because malicious actors are increasingly turning to trusted online services and tools like Microsoft Sway -- allowing them to manufacture slick, convincing phishing experiences for your users that exploit online brands that they already work with everyday.
When the bad guys are cloaking their malicious emails in trusted online brands like Microsoft, your users need help. That means New-school Security Awareness Training, which gets them up to speed on all the latest tricks used by the bad guys and keeps them on their toes with simulated phishing emails that test their mettle against the very latest social engineering tricks malicious actors are actually using "in the wild."
 Here's how it works:
Here's how it works:
