This Netflix phishing campaign goes after your login, credit card, mugshot and ID!
Paul Ducklin at Sophos wrote: "Think of the big security stories of recent months. Security holes like KRACK [and Meltdown]; a plethora of ransomware attacks ending in extortion; data breaches that were big, bigger or biggest, there are plenty of candidates for the story that got the most attention.
In contrast, phishing attacks rarely make the news these days, even though (or perhaps precisely because) there are so many of them.
Somehow, phishing seems to have turned into an “obvious” problem that everyone is expected to have experienced, learned from, got the better of, and moved on.
But phishing is still big business for cybercriminals: in the last week alone, for example, SophosLabs intercepted phishing attacks that abused the brands of many financial institutions.
Organizations that had their brands hijacked in this way in the past few days include: eBay, PayPal, VISA, American Express, Bank of America, Chase, HSBC, National Australia Bank – and that’s just a random subset of the list, in one industry sector.
Protecting your brand against abuse by phishers is, sadly, as good as impossible, especially if your brand is well-known and widely advertised."
He is right, phishing and spear-phishing are still the bad guys' No. 1 infection vector of choice. This Scam Of The Week covers a phishing campaign that hijacked the Netflix brand.
This phish tries to trick you into handing over your login details, your credit card data, your mugshot and your ID. Here is how the lure looks:
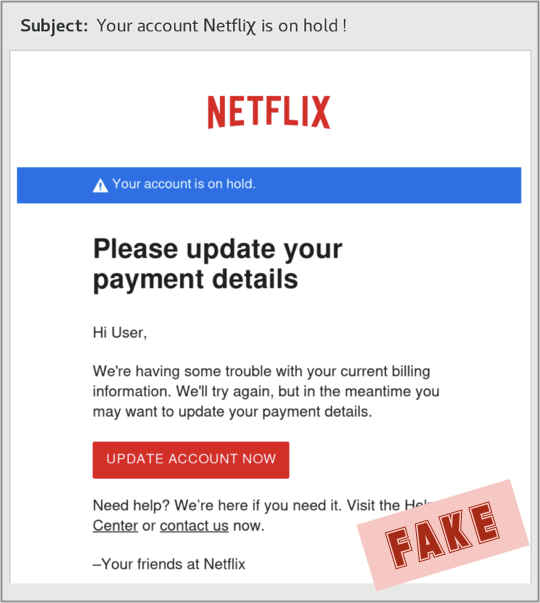
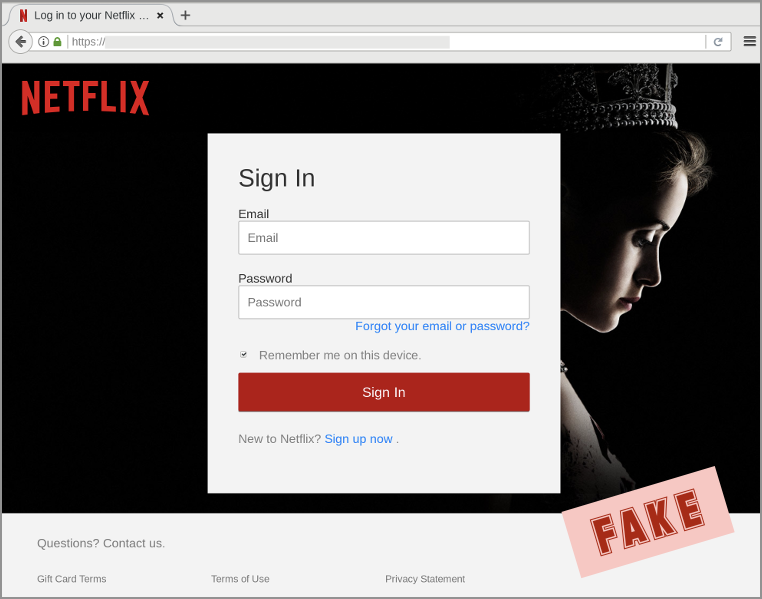
(Note the simple trick, right there in the subject line, of not spelling out the brand-theft text “Netflix” exactly: the crooks wrote the X as the Greek letter chi, so that Netflix came out as Netfli𝛘.) Next, you wind up here and that's where they steal your credentials. But wait, there's more...
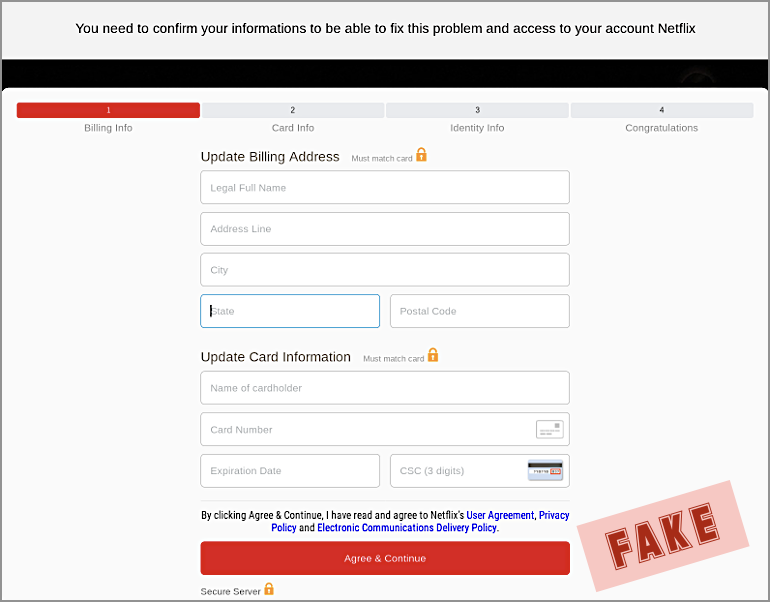
Next, they steal your credit card data:
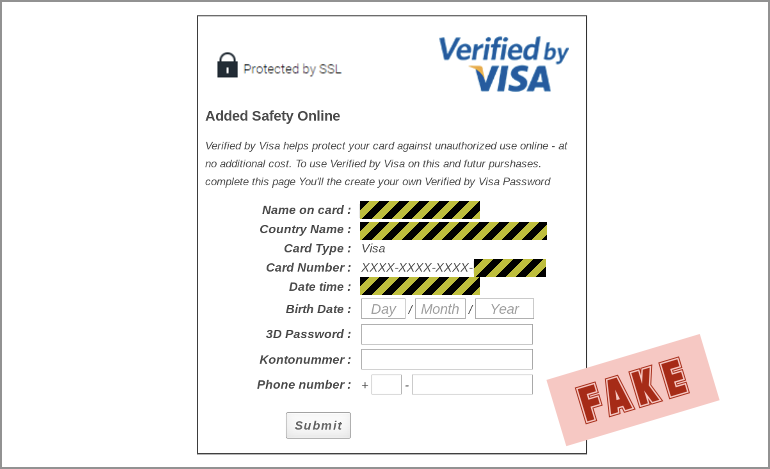
And trying to keep you on the hook they throw in a Verfied by VISA page:
And to add insult to injury, they also make you confirm your identity by taking a selfie holding your identity card. Yikes:
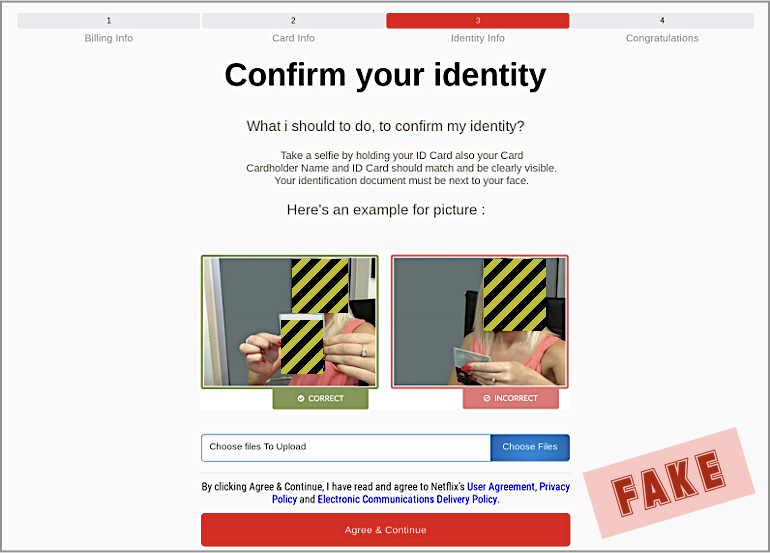
And then they redirect you to the real Netflix login page to keep you in the dark as long as possible.
Ducklin came up with some very good suggestions related to a sophisticated scam like this, so with grateful acknowledgements to Sophos, I suggest you send the following to your employees, friends, and family.
You're welcome to copy, paste, and/or edit:
There is a new sophisticated Netflix phishing attack you need to watch out for. They start very nice that they have some trouble with your billing info, and pretty please with sugar update your payment details. But if you fall for it, they will try to steal your login details, your credit card data, your picture and your ID! Here are the things to Think About Before You Click!
- Never click on a login link or an account verification link in an email. If there is one, bail.
- Check for the green HTTPS padlock. If there isn’t one, bail.
- But if there is a padlock, check the name of the site. If it’s not exactly what you expect, bail.
- Don’t ignore telltales such as spelling and grammar errors. If it looks wrong, bail.
- Guard your ID closely. If you’re asked for a selfie or ID when it isn’t absolutely necessary, bail.
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc

Wouldn't it be great if your users had a way to "roll back time" when they forgot to think before they click on a bad link? Now they can!
KnowBe4 is excited to announce Second Chance, a brand-new security tool for the Outlook email client that you can download and deploy at no cost.
 Second Chance enables your user to make a smarter security decision by giving them a way to back out of that click.
Second Chance enables your user to make a smarter security decision by giving them a way to back out of that click.
Second Chance takes an intelligent look at the clicked URL in email, and asks your user if they are sure they want to do this, in case they clicked on a potentially unsafe or an unknown website. It even prompts your user when they click on a Punycode link!
You might ask: "What happens if my user continues or aborts their action?" If they choose to abort their action, the prompt will be closed, and the URL will not be opened. If they choose to continue, their browser will navigate to the URL they clicked on.
Here's how it works:
- Checks links originated in email messages, including attached Office Documents and PDFs
- Set the message your user gets after clicking a URL
- Set "No Prompt" domains
- Install it standard, command-line or GPO
- Get reporting data on what URL users chose to abort or continue to share with management
Second Chance could one day be the difference between a ransomware infection and a free weekend. Give it a try!
Requirements: Windows 7 (32 or 64 bit) and higher, all installed versions of Outlook 2007 and higher, .NET 4.0 or newer.





