 We sent out some warnings and advisories last week about Spectre and Meltdown, but we want to remind everyone again about some steps you can take to protect yourself.
We sent out some warnings and advisories last week about Spectre and Meltdown, but we want to remind everyone again about some steps you can take to protect yourself.
Remember that the bad guys are also going to jump on this bandwagon with phishing attacks! Here is a live one, just picked from the wild:
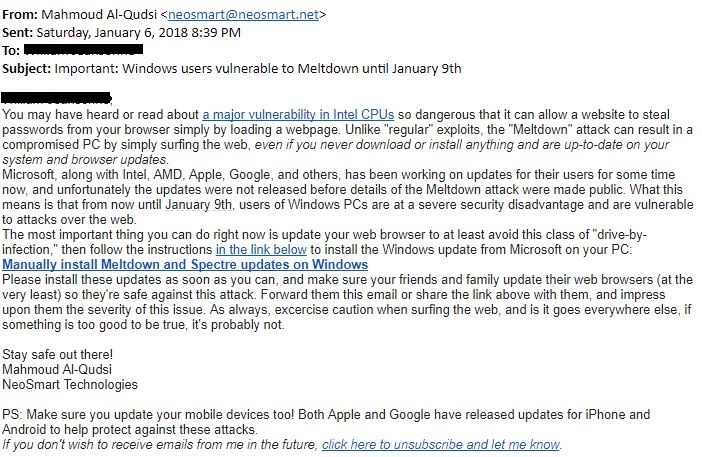
For the most part protecting your network comes down to applying the many patches vendors have been rolling out since the bugs broke into public awareness.
There are three of them, and they essentially enable side-channel attacks and information theft as an unfortunate side effect of the chips having been engineered for speed and efficiency by performing speculative execution.
"Meltdown" (CVE-2017-5754) is a flaw that lets ordinary applications cross the security boundaries enforced at chip level to protect access the private contents of kernel memory. This bug has been found in Intel chips produced over the last decade.
The other two vulnerabilities are being called "Spectre" (CVE-2017-5753 and CVE-2017-5715), and these are more insidious and widespread, having been found in chips from AMD and ARM as well as Intel.
Spectre could enable an attacker to bypass isolation among different applications. Some early reports began to appear at the end of the first week in January that Meltdown at least was being exploited in the wild.
It's also good to remember that an incident like this not only presents you with a challenge, but also with an opportunity to raise awareness and shore up your security. Five things are worth noting:
- First, vendors are working quickly to roll out patches. Microsoft and Google did so last Thursday, and they're not alone. Patch quickly but with discretion: not all anti-virus programs are compatible with the updates.
- Second, your people may notice that some of the services they're accustomed to using seem to be moving more slowly. That may not be in their mind, and it may not be evidence of a problem, but rather a sign that those services, cloud providers in particular, are taking steps to mitigate the risk.
- Third, be alert for social engineering scams related to the bug announcements. These follow most major cyber incidents, and Meltdown and Spectre will be no different. Remind your employees of your patching policies and notification practices, a ready-to-send email to your users is below. Reinforce with your people that they're the last line of defense.
- Fourth, now that ARM and AMD processors are known to be afflicted with Spectre at least, remember that those chips are widely used in distributed, set-it-and-forget-it, Internet-of-things devices. The risk is likely to linger there longest.
- And fifth, the disclosure suggests a human problem. Google found the flaws last summer and vendors have been quietly working to prepare fixes since then. The news broke suddenly, and before fixes were entirely ready, because Google determined that someone, somewhere, had begun to leak the news.
I suggest you send the following to your employees, friends, and family. You're welcome to copy, paste, and/or edit:
You may have read in the press or seen our earlier announcement that it was recently discovered that practically all computer systems worldwide have a hardware bug called "Meltdown" and "Spectre". Hardware and software vendors have been working hard to create software patches to get around this problem and we are in the process to apply these patches on our whole network.
However, bad guys are using this major event to try to trick you into downloading malware that claims to be a patch for the "Meltdown" and "Spectre" hardware issue. Don't fall for it!
In the office, IT will take care of all patching and will notify you about it. Do not act on any emails or popups that tell you to urgently update your computer. At the house, take the same precautions. Patches should only come from official sources like the manufacturer of your PC or the developers of your Operating System (Microsoft Windows or Apple Mac).
The New York Times published an accessible overview of the issue here: https://www.nytimes.com/2018/01/04/technology/meltdown-spectre-questions.html?_r=0
Free Phishing Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack?
Cyber-attacks are rapidly getting more sophisticated. We help you train your employees to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks. Take the first step now. Find out what percentage of your employees are Phish-prone™ with our free test. Did you know that KnowBe4 also supports "Vishing" where you can actually send your users simulated voice mail attacks?
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





