As one of his last actions in office, President Obama expelled 35 Russian diplomats spies in retaliation for Russia interfering with the U.S. election process, after intelligence agencies lined up their stories and all pointed at Putin.
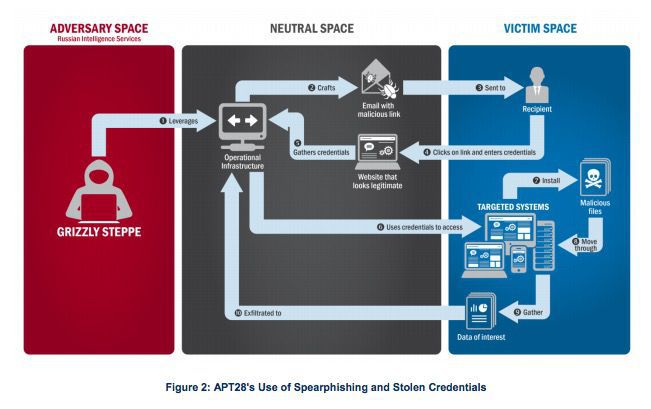
Bloomberg just wrote: "The attack against U.S. democracy began in the summer of 2015 with a simple trick: Hackers working for Russia’s civilian intelligence service sent e-mails with hidden malware to more than 1,000 people working for the American government and political groups. U.S. intelligence agencies say that was the modest start of 'Grizzly Steppe,' their name for what they say developed into a far-reaching Russian operation to interfere with this year’s presidential election."
The hackers sent spoofed phishing e-mails which looked like they came from legit websites. The hackers used social engineering to trick employees to fall for the spearphishing e-mails and got a foothold into the Democratic National Committee and other key e-mail accounts like Podesta for material that would later be leaked to damage Hillary Clinton in her losing campaign against Trump.
“This activity by Russian intelligence services is part of a decade-long campaign of cyber-enabled operations directed at the U.S. government and its citizens,” according to a joint statement from the Federal Bureau of Investigation, DHS and the Office of the Director of National Intelligence. “The U.S. government seeks to arm network defenders with the tools they need to identify, detect and disrupt Russian malicious cyber activity that is targeting our country’s and our allies’ networks.”
 Well, that would start with stepping all employees through new-school security awareness training which includes frequent simulated phishing attacks arriving in everyone's inbox.
Well, that would start with stepping all employees through new-school security awareness training which includes frequent simulated phishing attacks arriving in everyone's inbox.
The FBI knew that the DNC was being hacked, but was not very effective about it. Here is a DNC internal memo:
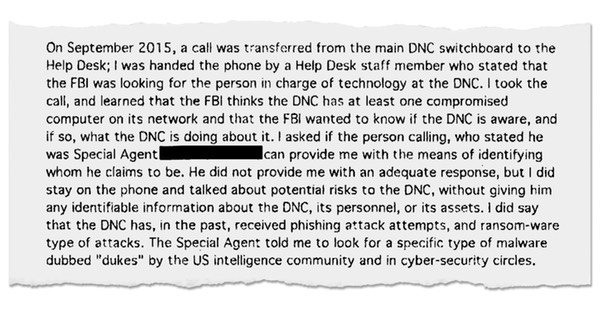
As the New York Times reported earlier this month, the FBI initially just called the DNC system admins:
Mr. Tamene, who reports to Mr. Brown and fielded the call from the FBI agent, was not a full-time DNC employee; he works for a Chicago-based contracting firm called The MIS Department. He was left to figure out, largely on his own, how to respond — and even whether the man who had called in to the DNC switchboard was really an FBI agent.
"The FBI thinks the DNC has at least one compromised computer on its network and the FBI wanted to know if the DNC is aware, and if so, what the DNC is doing about it," Mr. Tamene wrote in an internal memo about his contacts with the FBI He added that “the Special Agent told me to look for a specific type of malware dubbed 'Dukes' by the U.S. intelligence community and in cybersecurity circles."
Part of the problem was that Special Agent Hawkins did not show up in person at the DNC. Nor could he email anyone there, as that risked alerting the hackers that the FBI knew they were in the system.
Mr. Tamene's initial scan of the DNC system — using his less-than-optimal tools and incomplete targeting information from the FBI — found nothing. So when Special Agent Hawkins called repeatedly in October, leaving voice mail messages for Mr. Tamene, urging him to call back, "I did not return his calls, as I had nothing to report," Mr. Tamene explained in his memo.
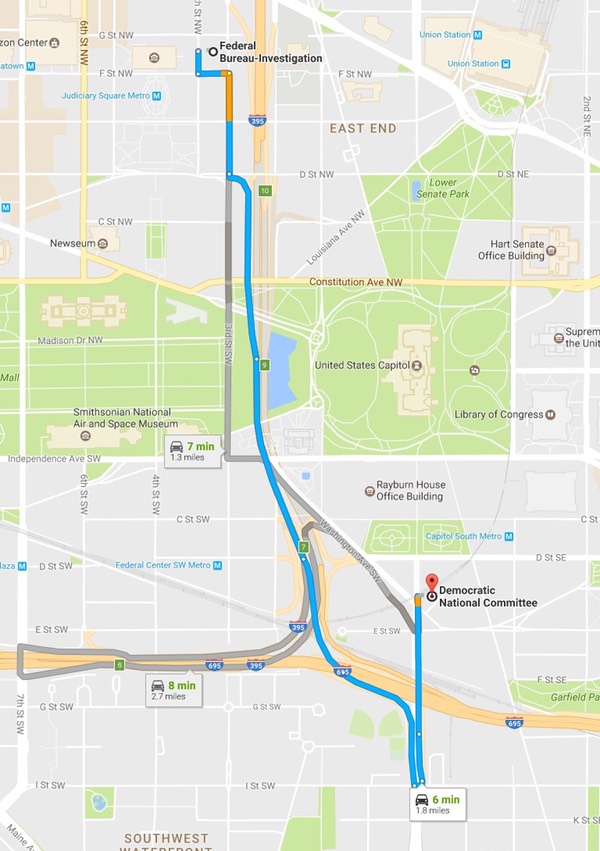
Yup, the DNC stopped returning the FBI agent's calls. What stopped the FBI to simply drive over to the DNC office is a mystery. They are a six-minute drive away from each other.
The initial hackers worked for Russia’s FSB, the successor to the KGB after the USSR imploded. Once the DNC was compromised, the group called “Advanced Persistent Threat 29” or “APT 29,” used stolen credentials to expand its access to directories and other data, and exfiltrated e-mail from several accounts.
“A great deal of analysis and forensic information related to Russian government activity has been published by a wide range of security companies,” according to the statement from the FBI, DHS and DNI. “The U.S. government can confirm that the Russian government, including Russia’s civilian and military intelligence services, conducted many of the activities generally described by a number of these security companies.”
Yes, and we are speaking specifically about the NSA, which has been able to see at least since 2006 what is moving through the wires thanks to sophisticated signals interception tech (SIGINT). Looking at a never-before-seen document leaked by Snowden, The Intercept discovered that the NSA can tell, as far back as 2005, what entity was behind a certain hack thanks to sophisticated signals interception technology.
Snowden tweeted earlier this year that if Russia was hacking the Democrats, the NSA has the goods. Snowden said that tracing back hackers using SIGINT technology “is the only case in which mass surveillance has actually proven effective.” Snowden said that the NSA has a tool called XKEYSCORE that is similar to a global SIGINT search engine that “makes following exfiltrated data easy. I did this personally against Chinese ops.”
Still Hacking
The U.S. government first announced that intelligence agencies had high confidence that the Russian government was behind the hacking a month before the Nov. 8 election. Despite that public declaration, the hacking attacks have apparently continued.
Actors probably associated with Russian civilian and military intelligence services “are continuing to engage in spearphishing campaigns, including one launched as recently as November 2016, just days after the U.S. election,” the report said.
Russia has denied involvement in the election-related hacks.
Yeah, right.
if you are not a KnowBe4 customer yet, at times like this, it is very good to know what percentage of your users are vulnerable to social engineering attacks like described above. We recommend you do your free Phishing Security Test and find out what your phish-prone percentage of your users is.
PS, if you do not like to click on buttons with redirects, here is a URL you can cut/paste:
https://info.knowbe4.com/phishing-security-test-16
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.






