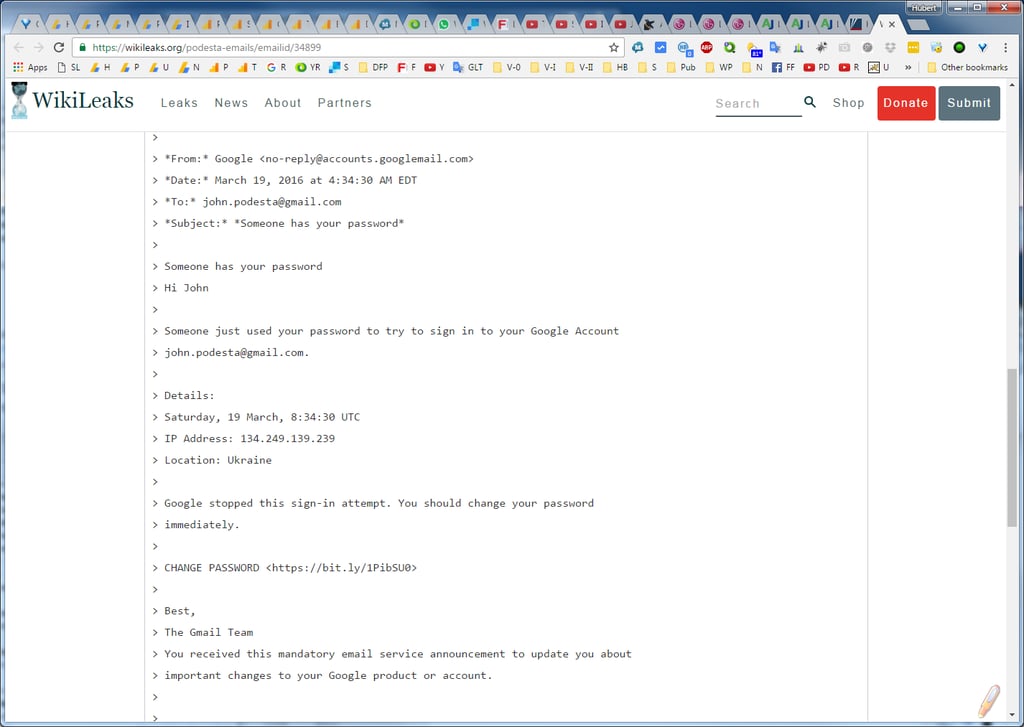
Podesta’s IT team told Podesta the fake gmail email was real.
Podesta’s chief of staff, Sara Latham, forwarded the email to the operations help desk of Clinton’s campaign, where staffer Charles Delavan in Brooklyn, New York, wrote back 25 minutes later, “This is a legitimate email. John needs to change his password immediately.”
But the email was a sophisticated Russian phishing attack
The link to the website where Podesta was encouraged to change his Gmail password actually directed him instead to a computer in the Netherlands with a web address associated with Tokelau, a territory of New Zealand located in the South Pacific.
In the email, the hackers even provided an Internet address of the purported Ukrainian hacker that actually traced to a mobile communications provider in Ukraine. Also note that the hackers struck Podesta on a weekend morning, when organizations typically have fewer resources to investigate and respond to reports of such problems.
The help-desk staffer, Delevan, emailed to Podesta’s chief of staff a separate, authentic link to reset Podesta’s Gmail password and encouraged Podesta to turn on two-factor authentication; “It is absolutely imperative that this is done ASAP,” Delevan said.
Tod Beardsley, a security research manager at the Boston-based cybersecurity firm Rapid7, said the fact that an IT person deemed the suspicious email to be legitimate “pretty much guarantees the user who is not an IT person is going to click on it.”
New-school security awareness training which includes frequent simulated phishing attacks for both Podesta and the IT help desk staffer could have prevented this disaster. Get a one-on-one live demo and see for yourself how easy and affordable this is for your organization.
Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://info.knowbe4.com/kmsat-request-a-demo





