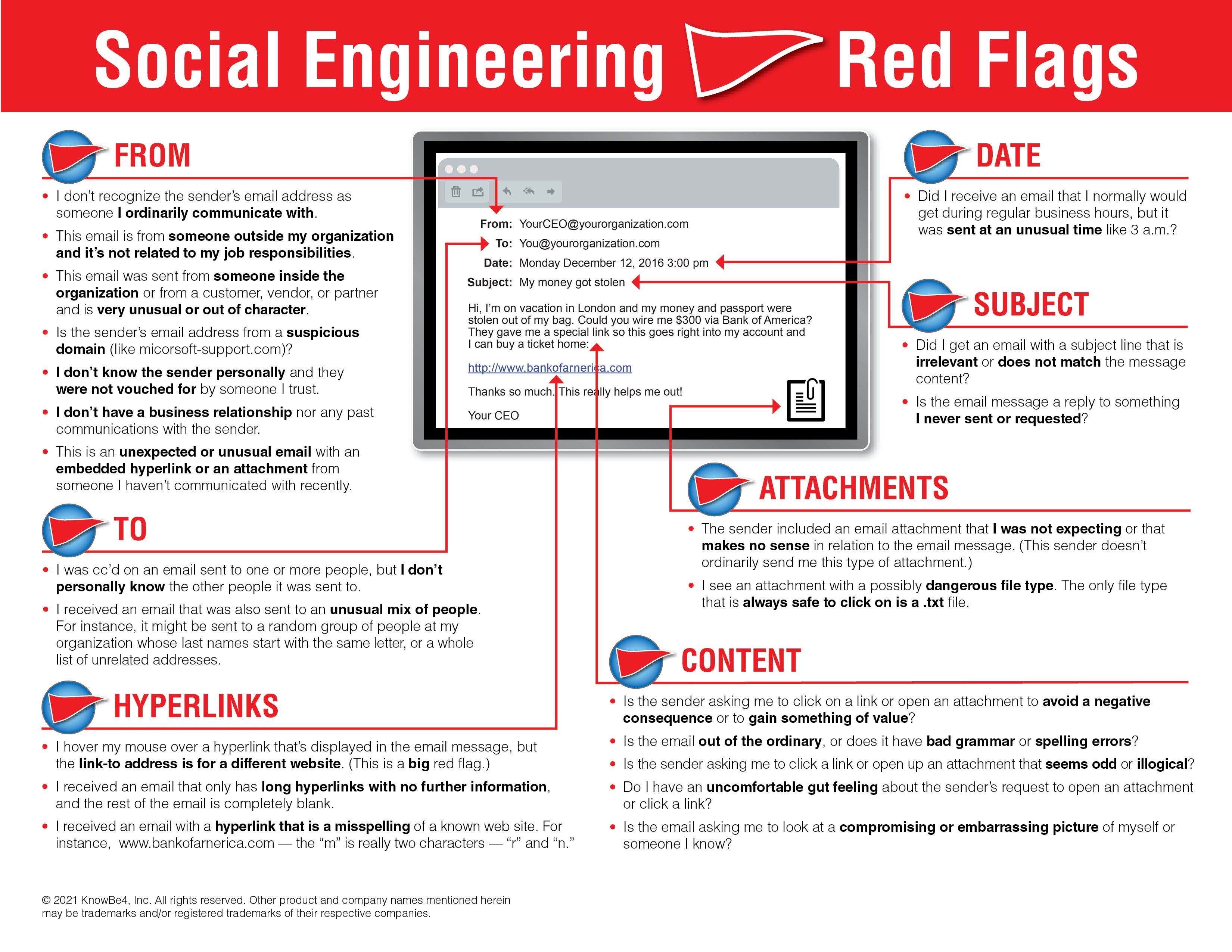
The easiest way to avoid falling for scams and other social engineering attacks is to have an understanding of the tactics employed by attackers, according to Roger A. Grimes, writing in CSO. Grimes outlines some of the most common scams and points out the warning signs that are usually present in these schemes.
One of the most common signs of a scam is the use of “stressor events,” which play on the victims’ emotions to make them act irrationally. There are a wide variety of stressor events, ranging from the mild to the extreme. Scammers can simply try to rush you by claiming that the deal will be called off if you don’t act soon, or they can threaten you with arrest or worse if you don’t pay them quickly. They can also be used as excuses on the scammer’s side, such as a sudden family tragedy affecting their ability to send or receive a transaction.
Grimes says you should also be wary if someone is overly eager to pay full price for an item, particularly if they say they can only pay by check. Scammers often take advantage of people who think that the money is in their possession as soon as their bank clears a check. For instance, they’ll send a check for more than what was requested, and then ask the victim to send the excess money to someone else. If the victim complies, then their money will be in the scammer’s possession before the bank informs them that the check was fraudulent.
Additionally, you should be suspicious if a person is difficult to contact, is unwilling or unable to speak on the phone or meet in person, or comes up with excuses to induce you to send or receive money in an unconventional way. For example, whenever someone asks you to pay them in gift cards, don’t: you’re being scammed. This seems obvious and easily avoidable, but many people still fall for it.
Grimes emphasizes that people don’t fall for scams because they’re stupid. Their ability to resist scams depends primarily on their having knowledge of the scams themselves.
“Don’t shame victims into thinking that they were dumb or a patsy,” Grimes writes. “Intelligence has nothing to do with it. The deciding factor whether someone can be scammed is awareness of the scam presented to them. . . . The number one scam defense is awareness education. Banks are doing it. Employers are doing it. Craigslist is doing it. Many people and businesses try their best to inform people about the various scams.”
Most scams are surprisingly easy to spot once you know how they work. New-school security awareness training can teach your employees about these techniques so that they can recognize and resist social engineering attacks.
 Here's how it works:
Here's how it works:




