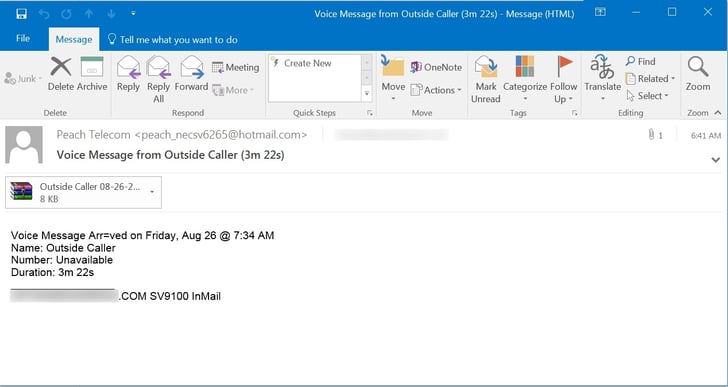
Several days ago we posted about a new ransomware campaign pushing Cerber through malicious ZIP files attached to voicemail-themed phishing emails. Fast on the heels of that campaign comes yet another voicemail-themed ransomware campaign, only this one is pushing Zepto ransomware through zipped .WSF files.
Zepto is a Locky variant or copycat, implementing many of the same features as Locky. It was first seen back in June. Although initial Zepto campaigns employed malicious .DOCM attachments or zipped .JS files, the bad guys turned to pushing Zepto through zipped .WSF files in early August and often try to social engineer users with fake banking data, invoices, shipping information, and of course now even voicemail attachments.
Zepto encrypts a long list of file types on victim PCs using AES-128 and RSA-2048 ciphers. HTML-formatted ransom notes are dropped in folders. Another imaged copy of the ransom note is set as the desktop wallpaper: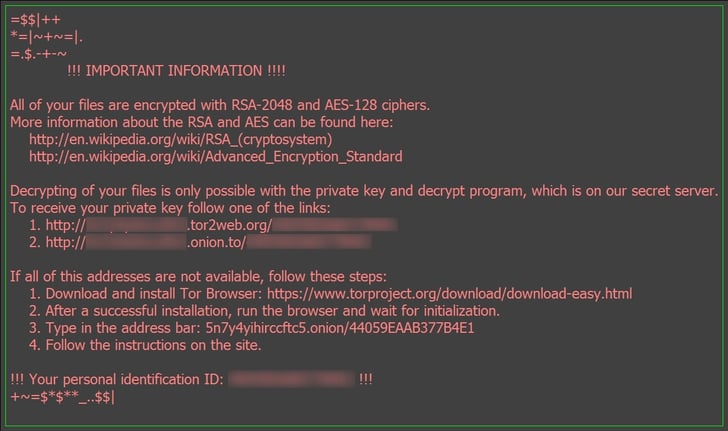
Encrypted files are re-named with a long alpha-numeric string and carry the .ZEPTO file extension. Currently there is no decryptor available for Zepto-encrypted files.
We were alerted to this new Zepto campaign through phishing emails forwarded to us by customers who have implemented the free Phish Alert Button on user desktops and endpoints throughout their organizations. Although we have no hard numbers at this point, this campaign does appear to be a significant one and your users could very well encounter these voicemail-themed phishes landing in their inboxes. Most anti-virus engines on VirusTotal are showing no detection at this point for the zipped .WSF files, although a handful do recognize it as Nemucod, a trojan downloader with a long history of being used to pull down malware onto compromised PCs.
As with most voicemail-themed phishing attacks, one key tip-off that not all is right with the purported voicemail notification email is the format of the attachment. Instead of the .WAV or MP3 files typically distributed by automated voicemail systems, users will encounter a variety of other file formats including .ZIP, .PDF, or .DOC(M).
If your company or organization does use a phone system that distributes voicemail files via email, users should be trained to recognize those emails - the expected text bodies as well as the standard format and naming for any attachments. Users familiar with what internal voicemail notifications should look like are much less likely to fall for poorly constructed, generic-looking fake voicemail phishing attacks like this one.
Free Phish Alert Button
When new ransomware campaigns like this one hit your organization, it is vital that IT staff be alerted immediately. One of the easiest ways to convert your employees from potential targets and victims into allies and partners in the fight against ransomware is to roll out KnowBe4's free Phish Alert Button to your employees' desktops. Once installed, the Phish Alert Button allows your users on the front lines to sound the alarm when suspicious and potentially dangerous phishing emails slip past the other layers of protection your organization relies on to keep the bad guys at bay.

Don't like to click on redirected links? Cut & Paste this link in your browser:
https://www.knowbe4.com/free-phish-alert?




