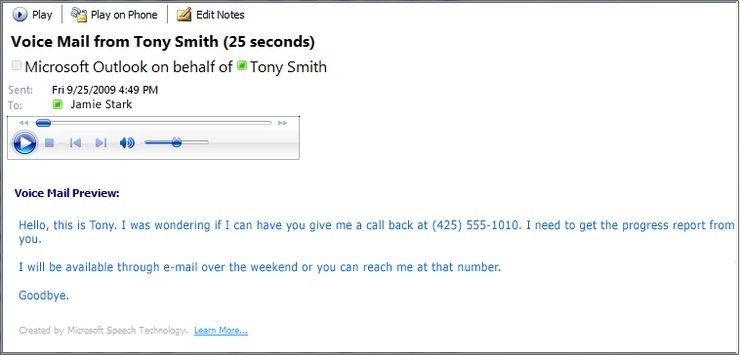
Don't play voicemail messages from suspicious sources. Example displayed in MS Outlook. Image credit: SANS ISC.
Xavier Mertens at the SANS Internet Storm Center had a great item that we have been warning against for a while now.
He started out with: "Bad guys need to constantly find new ways to lure their victims. If billing notifications were very common for a while, not all people in a company are working with such kind of documents. Which types of notification do they have in common? All of them have a phone number and with modern communication channels... everybody can receive a mail with a voice mail notification. Even residential systems can deliver voice message notifications."
One of the currently most prevalent ransomware strains called Cerber has even experimented with text-to-speech synthesizers to threaten victims to pay the ransom.
This new voice mail attack email arrives with an attachment, which supposedly contains a voice message, in a .wav file compressed in .zip folder. The folder actually contains hidden malicious code that will install ransomware and renames files to [original file name].crypted. The delivery mechanism may be exploiting the fact that missed call notification emails are enabled by default in Microsoft Outlook.
Consumers appear to be the first target of this ransomware campaign according to Mertens. The initial phishing attack campaign contained a voice message regarding a modem from Vigor, a UK distributor of ADSL modems for the residential market.
Another version of this attack is pushing Zepto ransomware through zipped .WSF files.
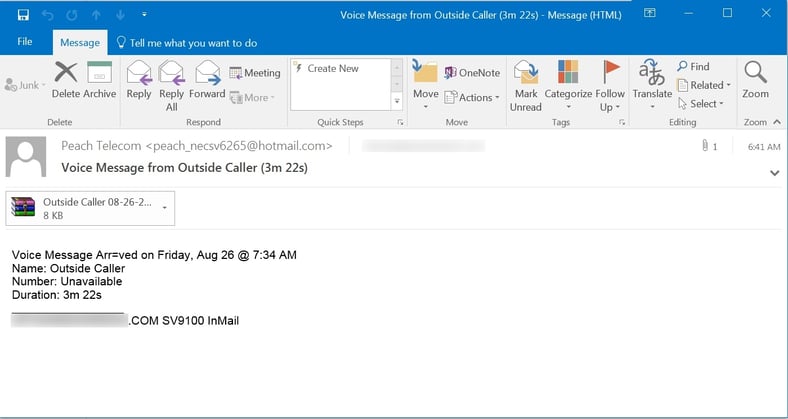
Zepto is a Locky variant or copycat, implementing many of the same features as Locky. It was first seen back in June. Although initial Zepto campaigns employed malicious .DOCM attachments or zipped .JS files, the bad guys turned to pushing Zepto through zipped .WSF files in early August and often try to social engineer users with fake banking data, invoices, shipping information, and of course now even voicemail attachments.
Zepto encrypts a long list of file types on victim PCs using AES-128 and RSA-2048 ciphers. HTML-formatted ransom notes are dropped in folders. Another imaged copy of the ransom note is set as the desktop wallpaper:
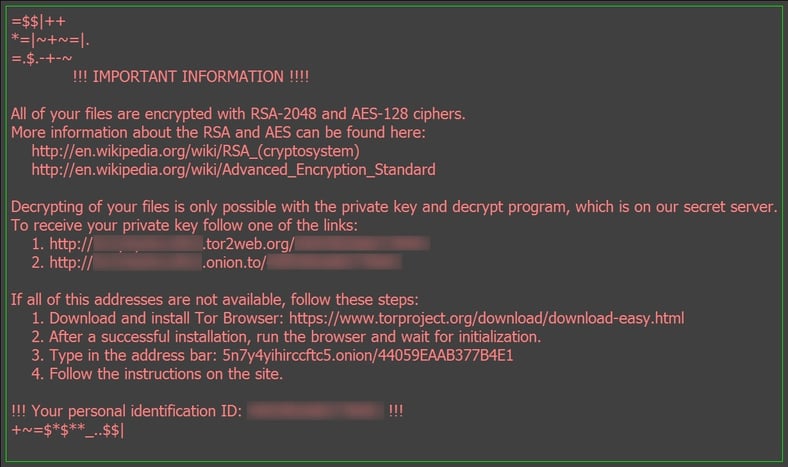
Encrypted files are re-named with a long alpha-numeric string and carry the .ZEPTO file extension. Currently there is no decryptor available for Zepto-encrypted files.
We were alerted to this new Zepto campaign through phishing emails forwarded to us by customers who have implemented the free Phish Alert Button on user desktops and endpoints throughout their organizations. Although we have no hard numbers at this point, this campaign does appear to be a significant one and your users could very well encounter these voicemail-themed phishes landing in their inboxes. Most anti-virus engines on VirusTotal are showing no detection at this point for the zipped .WSF files, although a handful do recognize it as Nemucod, a trojan downloader with a long history of being used to pull down malware onto compromised PCs.
As with most voicemail-themed phishing attacks, one key tip-off that not all is right with the purported voicemail notification email is the format of the attachment. Instead of the .WAV or MP3 files typically distributed by automated voicemail systems, users will encounter a variety of other file formats including .ZIP, .PDF, or .DOC(M).
If your company or organization does use a phone system that distributes voicemail files via email, users should be trained to recognize those emails - the expected text bodies as well as the standard format and naming for any attachments. Users familiar with what internal voicemail notifications should look like are much less likely to fall for poorly constructed, generic-looking fake voicemail phishing attacks like this one.
As we all know, the bad guys use the UK as a beta test for their attacks, and debug the whole campaign before they unleash it on the U.S. So use this as a heads-up and alert your users that they need to watch out for messages like this.
I recommend you send your employees, friends and family something like this, feel free to copy/paste/edit:
"Bad guys have found a new way to trick people into infecting their PC with ransomware. This time it looks like a Microsoft email that tells you about a voice mail that was left for you, and wants you to play the voice mail.
The email has an .zip attachement that supposedly has the voice mail message in a .wav file. However if you unzip the file, the ransomware will encrypt all the files on your computer and possibly all files on the network if you have access. You only get your files back if you pay around 500 dollars.
Do not click on links in "voice mail" emails from someone you do not know, and certainly do not open any attachments!
Remember, Think Before You Click!
Free Phishing Security Test
Did you know that 91% of successful data breaches started with a spear-phishing attack?
Cyber-attacks are rapidly getting more sophisticated. We help you train your employees to better manage the urgent IT security problems of social engineering, spear-phishing and ransomware attacks. Take the first step now. Find out what percentage of your employees are Phish-prone™ with our free test. Did you know that KnowBe4 also supports "Vishing" where you can actually send your users simulated voice mail attacks?
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





