An interesting Q1-16 threat report from the folks at Proofpoint. Every day, they analyze more than 1 billion email messages, hundreds of millions of social media posts, and more than 150 million malware samples. Banking Trojans and ransomware dominated the malware landscape while CEO Fraud gained speed. Their numbers make a clear case to allocate budget for new-school security awareness training.

In their Quarterly Threat Summary they revealed that ransomware vaulted into the top ranks of the most preferred malware by cybercriminals. Nearly one-quarter of document attachment-based email attacks in the first quarter featured the new Locky ransomware.
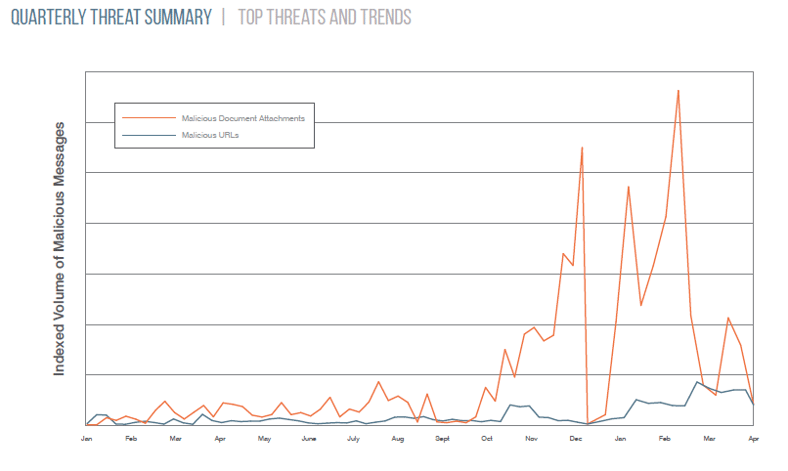
“The massive email message volumes associated with Dridex banking Trojan malware gave way to our discovery of the new Locky ransomware,” the report revealed. Here is a graph that shows the exploding number of malicious attachments.
The Locky ransomware strain is spreading to victims’ systems rapidly. Forbes claimed Locky infects approximately 90,000 systems per day and typically asks users for 0.5-1 Bitcoin (or $420) to unlock their systems. “Ransomware is back in a big way with new variants and techniques emerging regularly. Organizations need defenses that can stop these attacks before they can encrypt data and take critical systems offline,” the report said.
More C-level employees are at risk of targeted messages with business email compromise on the rise. Attackers have used more social engineering to trick users to complete tasks or run malware.
Some key takeaways from Proofpoint’s Q1 2016 research:
- CEO Fraud, aka business email compromise attacks, are increasingly mature and differentiated. 75% of these phishing attacks rely on fake “reply-to” spoofing to trick users into believing messages are authentic.
- Email continues to be the top threat vector, with malicious message Q1 2016 volume increasing by 66% over Q4 2015, and more than 800% over the same period in 2015. “Email represents the first line of attack for advanced threats and targeted attacks. It serves as a beachhead from which threat actors can pursue further malicious activities,” researchers pointed out.
- Java and Flash Player vulnerabilities continue to pay dividends for cybercriminals as Angler was the most used exploit kit, accounting for 60% of total exploit kit traffic. Neutrino and RIG exploit kit use was also up with an 86% and 136% increase, respectively.
“Threat actors employ a variety of highly effective lures that target departments (such as human resources and accounting) and specific people,” the report disclosed. “These lures use a variety of mechanisms to convince users that attackers’ requests for information or money transfers are legitimate.”
In other words, their social engineering attacks are getting better and better. Your organization needs to match these attacks and create a human firewall that resists these attempts.
Find out how affordable this is and be pleasantly surprised. Get a quote now:
Related Pages: Ransomware





