By Eric Howes, KnowBe4 Principal Lab Researcher.
By Eric Howes, KnowBe4 Principal Lab Researcher.
It's no secret that the threat of phishing emails has been growing at an alarming rate for a number of years. Indeed, ZDNet recently reported that 1 of every 100 emails is now malicious in one way or another, "likely to deliver malware, conduct spear-phishing, commit fraud or other activity conducted by cyber criminals."
Thus, it should surprise no one that cybercrime has become an incredibly lucrative endeavor, pulling in an estimated $1 million per minute for malicious actors.
Even we were surprised, however, to learn that cybercrime, driven largely by phishing attacks on softly defended organizations, is now so lucrative that even dead people are apparently getting in on the act.
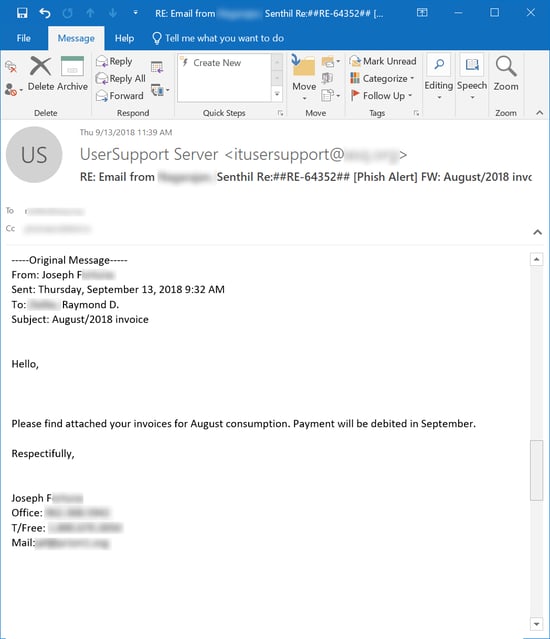
Consider this routine "fake invoice" phish, reported to us by one of our customers using the Phish Alert Button (PAB):
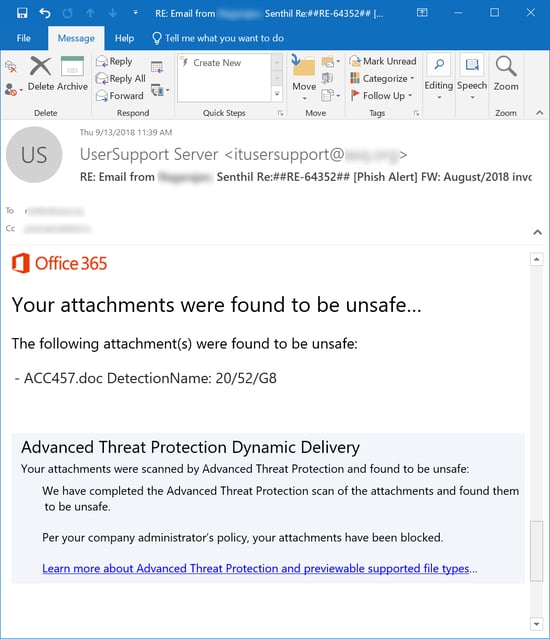
We see large numbers of these phishes every day. Unfortunately, anti-virus scanners don't have a very good track record with the malicious attachments that often accompany them. In this case, however, Office 365 blocked the attachment as malicious:
The user hit the Phish Alert Button (PAB), alerting his company's IT department. In a puzzling response, IT advised the user that the email in question was in fact legitimate despite the fact that Office 365 flagged the attachment:
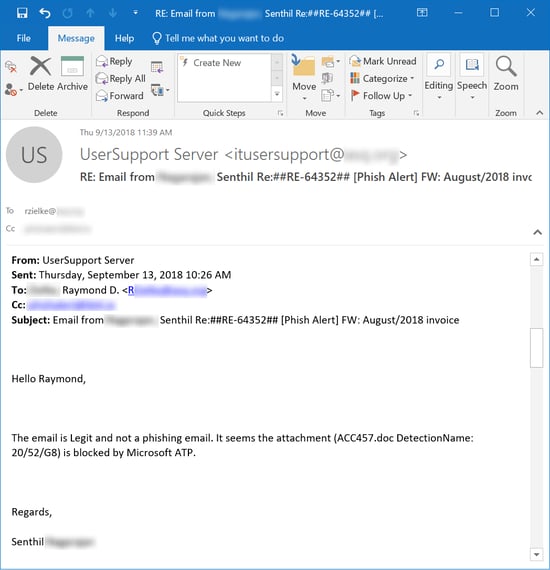
The user wasn't buying it, though. And his reasons for thinking the email malicious went far beyond Office 365's blocking of the attachment:
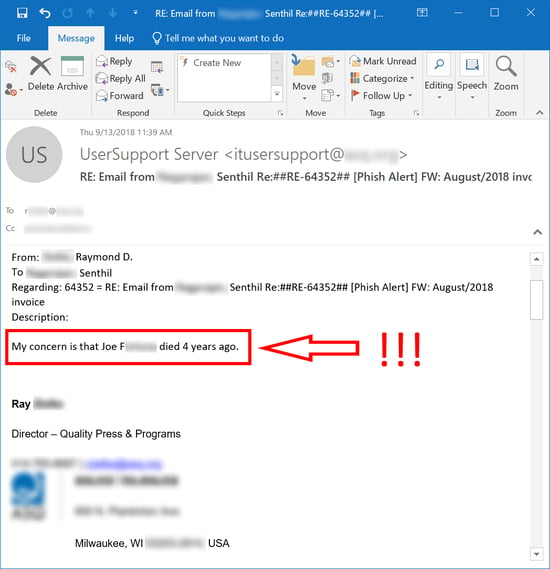
To his credit, the IT guy finally saw the light...
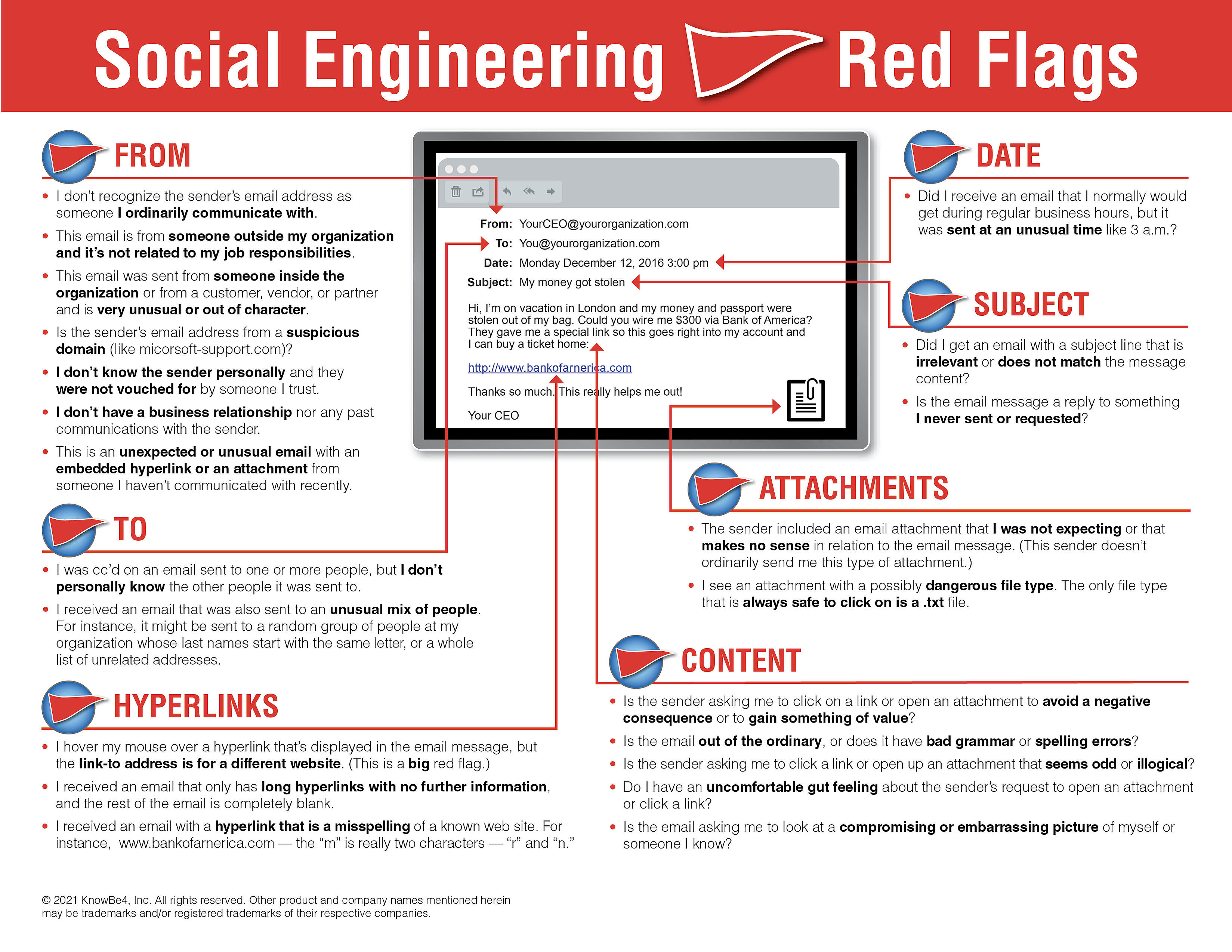
Our New-school Security Awareness Training advises users to watch for 22 different "red flags" that could indicate emails they receive are malicious. We must admit that we hadn't thought of this particular "red flag," and it is a big one: "The email is from someone who died years ago."
If your users are well-trained and on the alert, though, they will be prepared for any eventuality -- even when they get phished from beyond the grave.
Here is the full document with a list of red flags to watch out for. We suggest you share this with your users!