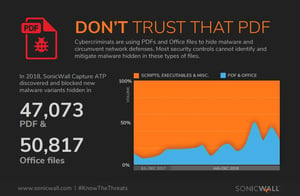
 The use of malware-laden PDF email attachments has spiked in recent months, internet security company SonicWall has found. Over the course of 2018, SonicWall detected 47,000 new attack variants using PDFs, while they observed more than 73,000 of these variants last month alone. 67,000 of these PDFs linked to scammers, while 5,500 contained links to malware downloads.
The use of malware-laden PDF email attachments has spiked in recent months, internet security company SonicWall has found. Over the course of 2018, SonicWall detected 47,000 new attack variants using PDFs, while they observed more than 73,000 of these variants last month alone. 67,000 of these PDFs linked to scammers, while 5,500 contained links to malware downloads.John Oates at the Register notes that, while malicious PDF attachments aren’t a new phenomenon, a surge of this magnitude shouldn’t be taken lightly.
“In many cases, targeted PDFs use zero-day exploits for browsers in order to increase the probability of a successful attack as on-the-ball businesses now patch their systems more quickly to protect against known exploits,” Oates writes. “Other attacks have been known to nick login details by tricking the user into opening malicious PDFs that use remote document loading mechanisms to capture and leak your credentials.”
Most of the attacks observed by SonicWall simply used PDFs to smuggle malicious links through email security filters. Many security filters struggle to analyze content inside PDFs, so an attacker stands a better chance of getting through to their victim if they place the link in one of these files. SonicWall CEO Bill Conner said that PDFs are increasingly becoming a “vehicle of choice for malware and fraud in the cyber landscape,” alongside emails and Office documents.
SonicWall notes that PDFs are generally thought of as a safe file type, so users often don’t hesitate to open them. Given the pervasiveness of PDFs within corporate and government environments, employees need to know how to avoid these attacks. New-school security awareness training can give your employees a thorough, up-to-date education about the threats they face. The Register has the story: https://www.theregister.co.uk/2019/04/19/pdf_malware_warning/






