 Aggregated results show 10.5% average rates at which enterprise email security systems miss spam, phishing and malware attachments.
Aggregated results show 10.5% average rates at which enterprise email security systems miss spam, phishing and malware attachments.Here is a summary of findings of email security systems to user mailboxes at companies tested in Cyren’s Email Security Gap Analysis program during the months of September and October 2017.
The Gap Analysis Overview Cyren examined 11.7 million emails forwarded to Cyren:
- Email volume analyzed: 11.7 million
- Test period: September – October 2017
- Average miss rate: 10.5%
Companies included in the tests were from a variety of industries and utilized several different types of email security, ranging from on-premises appliance gateway solutions to hosted email with some level of security filtering embedded in the service.
The percentages discussed in this report are therefore averages which serve as a reference. The gap analysis results can vary significantly, even between companies utilizing the same security solution.
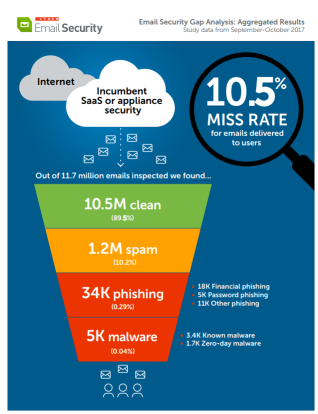
- Out of the 11.7 million emails analyzed by Cyren, 10.5 million (89.5%) were found to be “clean” or legitimate, including 4.67 million newsletter emails (over one-third of legitimate email traffic).
- 1.2 million emails (10.5%) were found to be spam or malicious messages that were missed by the deployed solutions and should not have been delivered to user mailboxes. This 10.5% “miss rate” breaks down into the following categories:
SPAM
1,187,408 emails delivered to users were found to be spam emails, 10.2% of the total email traffic. Spam in this study os defined as unsolicited bulk email, usually identified by content scanning techniques or by sophisticated pattern detection applied to elements of the email itself and email distribution patterns. As noted above, the spam category does not include legitimate newsletter emails.
PHISHING
Phishing emails were identified at 34,143 emails or 0.29% of the email delivered to users. From this total, Cyren identified 18,070 messages as financial phishing emails, 5,456 as password phishing emails, and 10,617 as general phishing.
MALWARE
Cyren found 5,039 emails delivered to users were found to have malware attachments. While this represents a small percentage of the total email delivered (0.04%), the high level of risk associated with malware actually delivered to users obviously makes this of great concern.
Of these 5,039 messages, 3,389 (two-thirds) included attachments with recognized malware signatures. These previously known threats could include, but are not limited to, ransomware, key loggers, rootkits, trojans, viruses, and worms.
1,650 of the malware emails delivered to users by the various systems were “zero-day” malware attachments, i.e., new malware with no previously known malware signatures. Despite the lack of existing signatures, Cyren’s security cloud identified these emails as malicious by utilizing proprietary techniques for detection.
The results presented above are averaged across many companies and different deployed security systems. But it is important to note that even when the email security system is the same, results can vary widely, influenced by an organization’s type of activity and user profile, and by security configuration choices made.
The three mini “case studies” presented below compare the results for different organizations that had deployed security from the same vendor. The percent of malicious emails (phishing + malware) making it through to users was double the rate for a university, compared to the two example businesses shown, which showed similar rates. Here is Cyren's full report: PDF.
We thought it was bad when we saw Cyren's recent analysis that 10.5% of bad emails made it through the filters. It could even be worse than that.
"Mimecast's latest ESRA (email security risk assessment) report found more than 14,277,163 pieces of spam, 9,992 emails containing dangerous file types, and 849 unknown emails with malware attachments -- all missed by the incumbent providers and delivered to users' inboxes.
Overall, the Mimecast security service determined that more than 14 million of the more than 95 million emails, or 15%, were in fact “bad” or “likely bad.”
In other words, the overall false negative rate in aggregate for the incumbent security systems that were tested was 15% of all emails inspected by Mimecast.
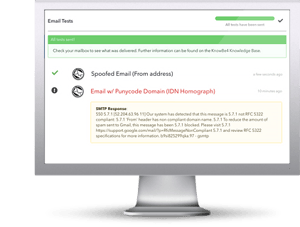
KnowBe4 is excited to announce that now you can use our brand new, innovative Mailserver Security Assessment (MSA), to help you assess your organization’s mailserver configuration settings and check the effectiveness of your email filtering rules.
With email still the #1 attack vector used by the bad guys, MSA helps you to see what types of messages may make it through your filters from the outside.
MSA gives you a quick insight at how your mailserver handles test messages that contain a variety of different message types including email with attachments that contain password-protected, macro zipped, and .exe files or have spoofed domains.
Here’s how MSA works:
- 100% non-malicious packages sent
- Select from 30+ automated email message types to test against
- Saves you time! No more manual testing of individual email messages using MSA's automated send, test, and result status
- Validate that your current filtering rules work as expected
- Results in an hour or less!
Find out now if your mail server is configured correctly, many are not!
Don't like to click on redirected buttons? Copy & Paste this link in your browser.
https://info.knowbe4.com/mailserver-security-assessment-blog





