The latest security research project has led to a USB cable so malicious that it can be used for just about any kind of attack.
We’ve written before about Kevin Mitnick, KnowBe4’s Chief Hacking Officer demonstrating a malicious USB cable. Despite the possibility, until now, there had only been a single known manufacturer of such a cable.
But a new cable has recently come to light – one developed by security researcher Mike Grover. Mike’s personal project is rather sophisticated in comparison to the cable shows previously by Kevin. Grover’s cable – which looks normal to the user – contains a Wi-Fi chip and is detected as a Human Interface Device.
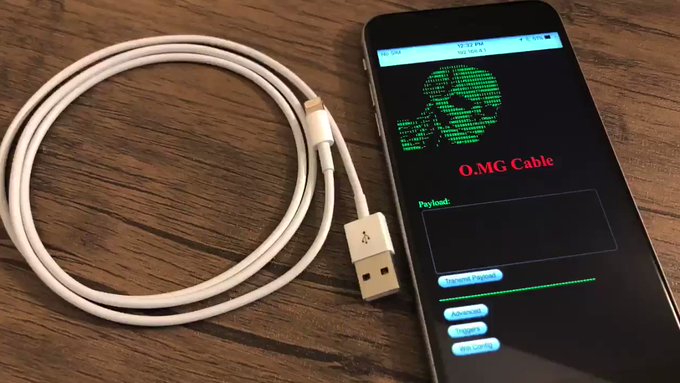
Credit: Mike Grover / Twitter
His cable can be remotely controlled, making it possible to inject commands onto the victim machine, including:
- Keystroke logging
- Downloading of malware
- Installation of Remote Access Trojans
- Opening of fake websites to harvest credentials
- And more
According to his webpage, the next iteration seeks to leverage a JavaScript, which opens up the possibilities of what a cable like this can do – including monitoring the victim machine for inactivity (the perfect time to strike), and silently compromising it without the user’s knowledge.
While Grover’s intentions appear to be white hat – he mentions offering these to security researchers – the presence of yet another cable shows how very possible it is for attackers to infiltrate an organization with little more than a seemingly benign piece of hardware.
Users undergoing frequent Security Awareness Training are taught to be watchful for anything suspicious – which includes cables lying about.
Free USB Security Test
Find out how your users will react to unknown USBs they find!
On average 45% of your users will plug in USBs. Find out now what your user’s reactions are to unknown USBs, with KnowBe4's new Free USB Security Test. Download our special, "beaconized" file onto any USB drive. Then label the drive with something enticing and drop the drive at an on-site high traffic area. If an employee picks it up, plugs it in their workstation and opens the file, it will "call home" and report the "fail" to your KnowBe4 console. And for Office documents, if the user also enables macros (!), additional data is tracked and geomapped.
 How your free 7-day USB Security Test works:
How your free 7-day USB Security Test works:
- Fill out the form on the right, and immediately...
- Download "beaconized" Word, Excel or PDF files
- Copy to any USB Drive, label and drop it
- Reports on opens and if macros were enabled
- Takes just a few minutes to setup
This is fun. Get your USB Security Test now!
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





