Larry Abrams at Bleepingcomputer reported on a new strain with a few unusual features:
"A new ransomware that pretends to be from a fake organization called the Central Security Treatment Organization has been discovered by security researcher MalwareHunterTeam. When the Central Security Treatment Organization, or Cry, Ransomware infects a computer it will encrypt a victim's files and then append the .cry extension to encrypted files. It will then demand approximately 1.1 bitcoins, or $625 USD, in order to get the decryption key."
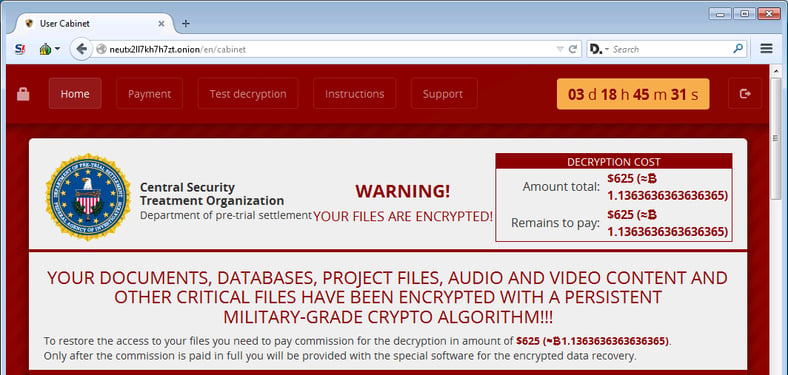
Abrams continued: "For example, like Cerber, this ransomware will send information about the victim to the Command & Control server using UDP. Furthermore, it will also use public sites such as Imgur.com and Pastee.org to host information about each of the victims. Last, but not least, it will query the Google Maps API to determine the victim's location using nearby wireless SSIDs."
This strain is clearly created by experienced coders that know what they are doing. Just look at the list of advanced features this Version 1.0 came out with. Looking at the resources spent to create this strain, you can expect a massive wave of attacks to follow soon. These bad guys have the resources and then some:
- Uses UDP to communicate with the Command & Control Server to evade detection
- Uses social networks to upload and host information about the victims using fake PNG files
- Queries Google Maps API to identify victim location using nearby wireless SSID's (!)
- Deletes the system Shadow Volume Copies
- Stays persistent after reboots using a random scheduled task
- Uses TOR payment site that requires the victim's personal ID from ransom note
- Has functioning support page to communicate with the criminals
- Includes a free (drag & drop, imagine that) decryption of one file to prove the files can be decrypted
Full technical details at Bleepingcomputer.
Be advised, if you are going to pay the ransom first make sure the one free decrypted file actually works. This strain is currently being analyzed and while there is no known free decryption right now, you can check the Central Security Treatment Organization Ransomware Help Topic in case one becomes available. Another great reminder to ALWAYS think befor you click!

Get your Updated Ransomware Hostage Rescue Manual
Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
- What is Ransomware?
- Am I Infected?
- I’m Infected, Now What?
- Protecting Yourself in the Future
- Resources
Don’t be taken hostage by ransomware. Download your rescue manual now!
Don't like to click redirected buttons? Cut & Paste this link in your browser:





