 Rather than steal your user’s credentials, this latest attack takes the OAuth route to gain access to the victim’s mailbox. This gives cybercriminals continual access, regardless of whether the user is logged on or not.
Rather than steal your user’s credentials, this latest attack takes the OAuth route to gain access to the victim’s mailbox. This gives cybercriminals continual access, regardless of whether the user is logged on or not.
We’ve seen a number of these kinds of phishing attacks over the last 12 months targeting mailbox access within Microsoft 365 and even posing as Coinbase. If you’re not familiar with these attacks, rather than trick the phishing victim into providing their Microsoft 365 credentials (which can easily be reset), the attack poses as a legitimate app and asks for application access to your mailbox (for reference, Outlook Mobile does this to facilitate continual access for your mobile phone to access your Microsoft 365 mailbox).
In a recent tweet from Microsoft Security Intelligence, a new App – simply entitled “Upgrade” – was identified asking for OAuth permissions that would allow attackers to create inbox rules, read and write emails and calendar items, and read contacts. It’s also noted that suspicious Inbox Rules are created by this access and appears to exfiltrate emails.
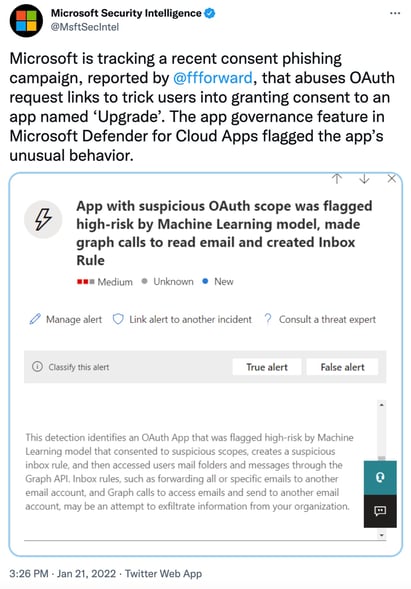
Source: Microsoft Security Intelligence
The good news is Microsoft has disabled this apps access across all of Microsoft 365. However, this does little for organizations, as new apps can be created asking for the same kinds of access.
The pivotal point where the attack can be stopped is when the malicious app is asking for access. Educating your users with Security Awareness Training would help ensure they are aware that – other than something like Outlook Mobile or another legitimate application – no unexpected phishing email EVER needs access to their mailbox.
 Here's how it works:
Here's how it works:




