.jpg?width=300&name=iStock-1182077181%20(2).jpg) The latest attack attempts to trick Office 365 users that use Coinbase into giving access to their mailbox via a Consent app rather than trying to steal their credentials.
The latest attack attempts to trick Office 365 users that use Coinbase into giving access to their mailbox via a Consent app rather than trying to steal their credentials.
With over 35 million users, Coinbase users are a pretty sizable target audience. At least that’s what the bad guys are betting on. And, from what we see in this latest attack, they’re also betting that Coinbase users are using Office 365.
In the latest attack, users receive an email impersonating Coinbase asking users to update their terms of service. Upon clicking the link to review the new ToS, users are taken to a legitimate Office 365 logon page (no funny stuff at this point in the attack), and are then presented with a request for access the user’s mailbox and information, citing “coinbaseterms.app” as the requestor (to keep with the ruse that this is about updating Coinbase terms of service).
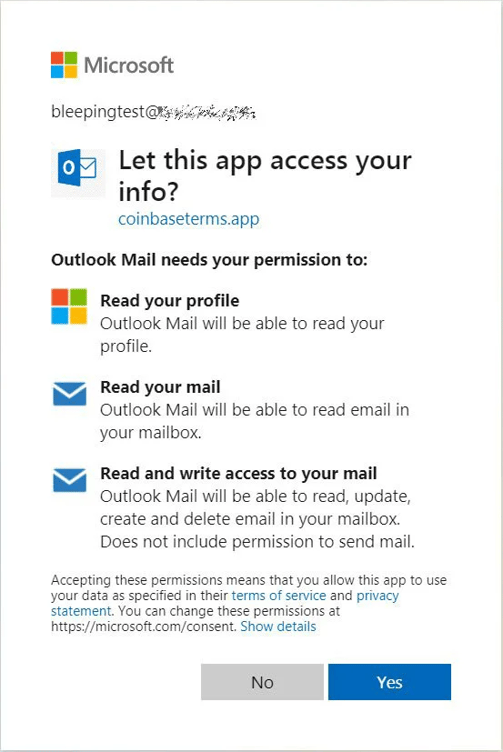
Once access is granted, the app now has access to read the victim’s emails, delete messages, and more. The only way to remove access is administratively.
This kind of attack isn’t new but is instead gaining ground. We’ve seen Consent app-based attacks since the beginning of this year. Our own Data-Driven Defense Evangelist, Roger Grimes has even written a detailed article on how Consent app attacks work and what to do about it.
Users need to be educated via Security Awareness Training that they should be looking for these kinds of attacks and only grant access to legitimate app publishers (such as Outlook for mobile devices).
 Here's how it works:
Here's how it works:




