.jpg?width=300&name=iStock-1219225761%20(1).jpg) It’s no surprise that phishers and scammers are using the avalanche of new information and events involving the global coronavirus pandemic as a way to successfully phish more victims. Phishers have always used titillating news headlines to push malicious emails past users’ normally more skeptical defenses. Scandal and death have always sold well for news sources and scammers alike. Sadly, phishers appear to have zero ethical issues exploiting the world’s biggest and deadliest healthcare issue in a century as a way to trick people.
It’s no surprise that phishers and scammers are using the avalanche of new information and events involving the global coronavirus pandemic as a way to successfully phish more victims. Phishers have always used titillating news headlines to push malicious emails past users’ normally more skeptical defenses. Scandal and death have always sold well for news sources and scammers alike. Sadly, phishers appear to have zero ethical issues exploiting the world’s biggest and deadliest healthcare issue in a century as a way to trick people.
Phishing campaigns involving COVID-19 have exploded. Phishing increased 667% in March 2020 alone mostly due to phishes using a coronavirus subject line. But all of us are also getting a ton of legitimate coronavirus emails at the same time. It can be hard to discriminate between the legitimate and fake COVID-19 emails for many users. User rates for clicking on COVID-19 simulated phishing tests are around 9% versus 4% for other types of common phishing themes, like banking-related subjects. The COVID-19 email subjects seem to be doubly tempting to users, at least right now. Because of that, I’ve put together this handy blog article discussing some of the top types and signs of fake COVID-19 emails along with lots of examples.
Big News!
Fake coronavirus phishing emails share nearly all the same “red flags” of social engineering as regular phishing emails, but with pandemic-related subject lines and content. The most common COVID-19 phishing emails have subject lines which announce some sort of BIG NEWS! These include fake celebrity deaths from the coronavirus, fraudulent cures and vaccine announcements, and fake COVID-19 information. Here’s an example of a COVID-19 phish that claims something to do with a vaccine. We are all clamoring for the vaccine. All you have to do is download and open the file attachment.
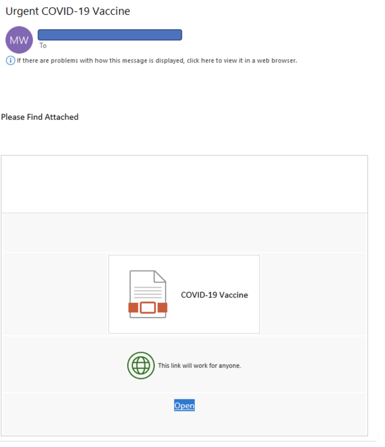
Immediate Stressor Events
All phishers love events that allow them to pressure potential victims into doing things they would not ordinarily do with “stressor events”, which call for the victim to do something immediately or else face negative consequences. The coronavirus pandemic is full of potential stressor events.
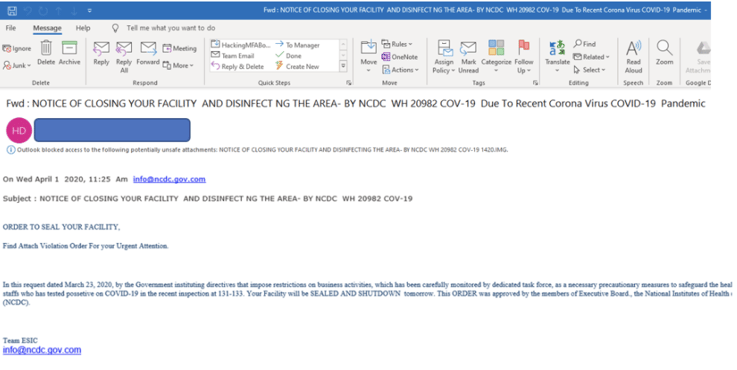
In the example below, the phisher is claiming the victim’s organization has been ordered by the government to close and shutdown, and it asks the victim to open a related file attachment, a “violation order” (that was luckily blocked by Microsoft Outlook by default).
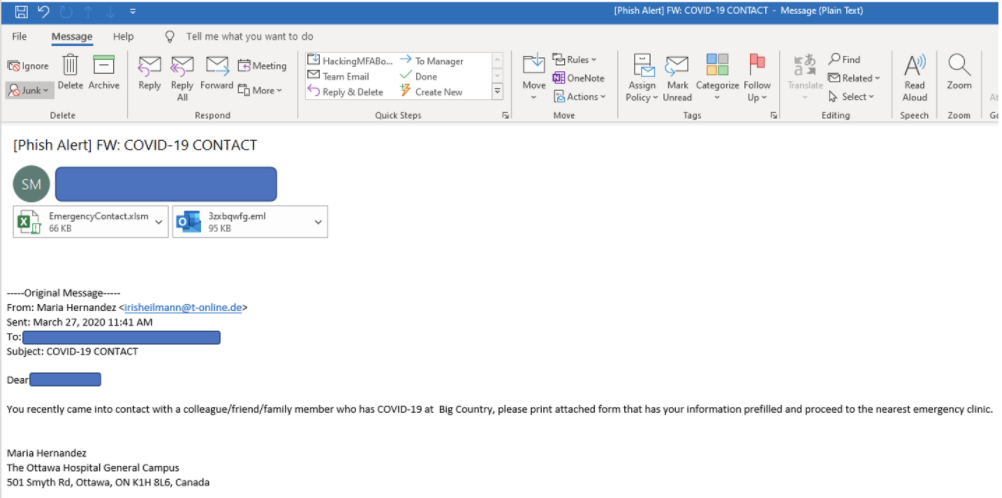
Here’s another claiming the potential victim came in contact with a COVID-19 infected person and to open the attached file to find out which emergency clinic to head to for testing. That’s a pretty big stressor event.
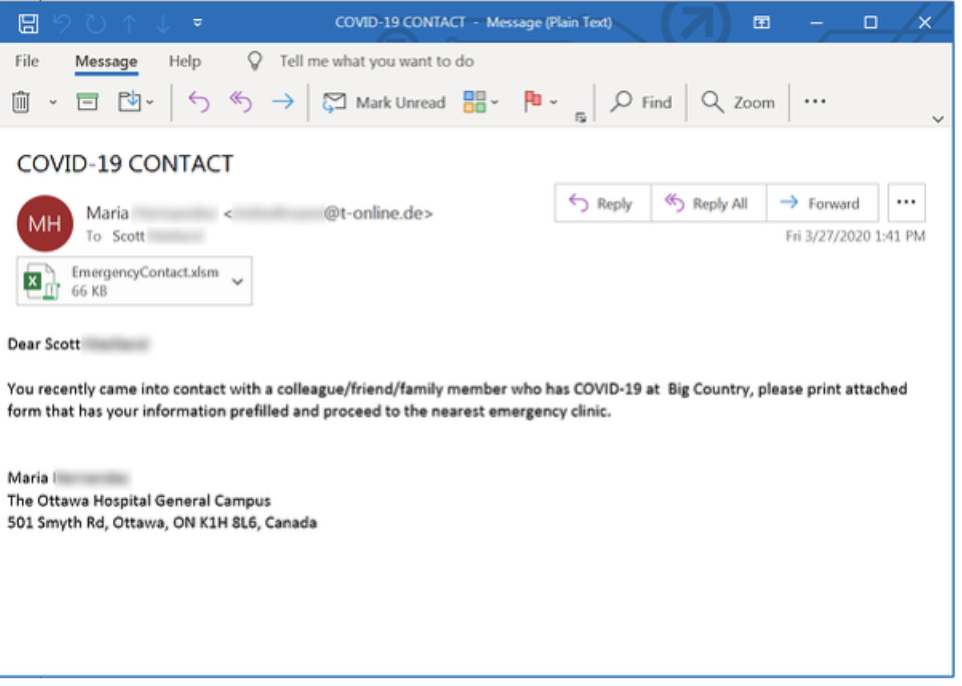
Dangerous File Attachments
The top sign I’m personally seeing of a likely suspicious coronavirus phish is a potentially dangerous file attachment (see the example below). The email is telling me I HAVE TO open or link to download a potentially dangerous file from a strange URL.
So far, none of the legitimate emails I’ve received related to COVID-19 have had a file attachment. Most have URL links to other content, but those links are legitimate links pointing to trusted domains. The phishing emails have links to Google Docs, Apple iCloud Drive, and O365 locations that I never, never get redirected to by legitimate organizations. If a file attachment isn’t coming from a legitimate domain name I trust, I’m not downloading it or clicking on it.
Multiple Mis-Matched Domains Involved
This is pretty standard phishing stuff, but with a COVID-19 angle added. In this example (see below), the BEC scammer is pretending to be an ongoing vendor looking to confirm that I can deliver some product or service during the COVID-19 pandemic. It’s a pretexting attack that will no doubt lead to a second email with them supposedly “ordering” something to begin the real BEC scam.
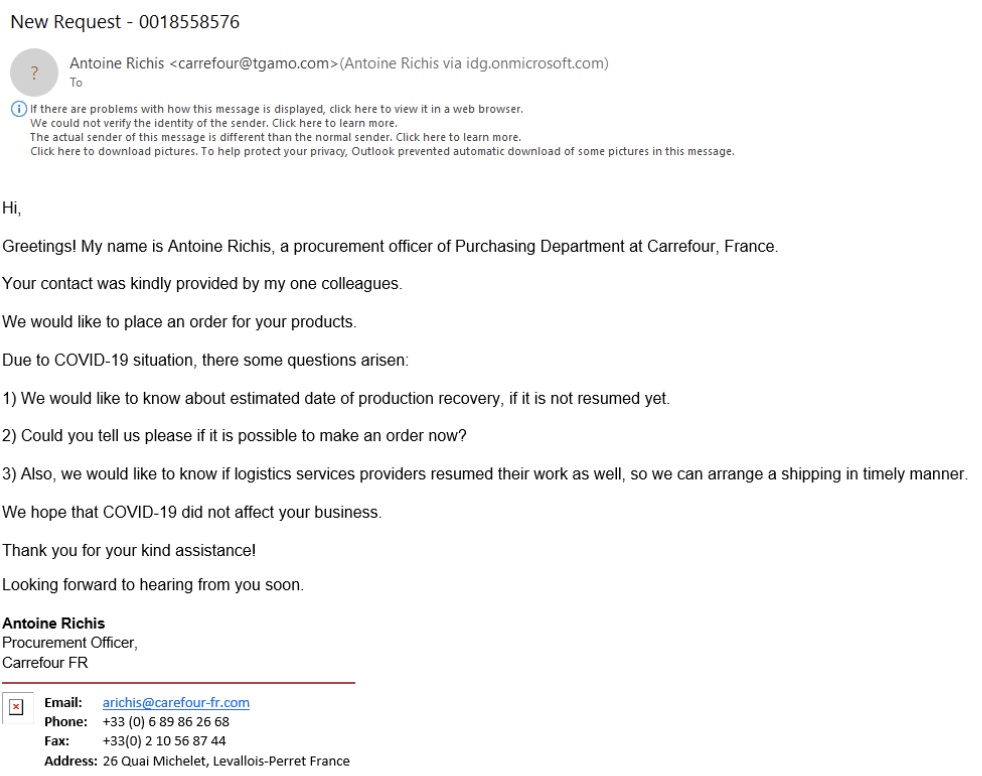
The obvious phishing sign is that the email shows two different email addresses belonging to two different domains (carrefour@tgamo.com and arichis@carefour-fr.com), neither of which is the claimed legitimate company domain of carrefour.com. Tgamo.com isn’t an active domain. And carefour-fr.com isn’t carrefour.com. A legitimate employee of Carrefour would not misspell their domain as carefour.
News From WHO
The World Health Organization (WHO) is heavily involved in the fight against coronavirus and is often in the news. Phishers like to push emails out claiming to be from WHO. Uh, the WHO doesn’t have time to send emails out to individual personal users (see an example below).
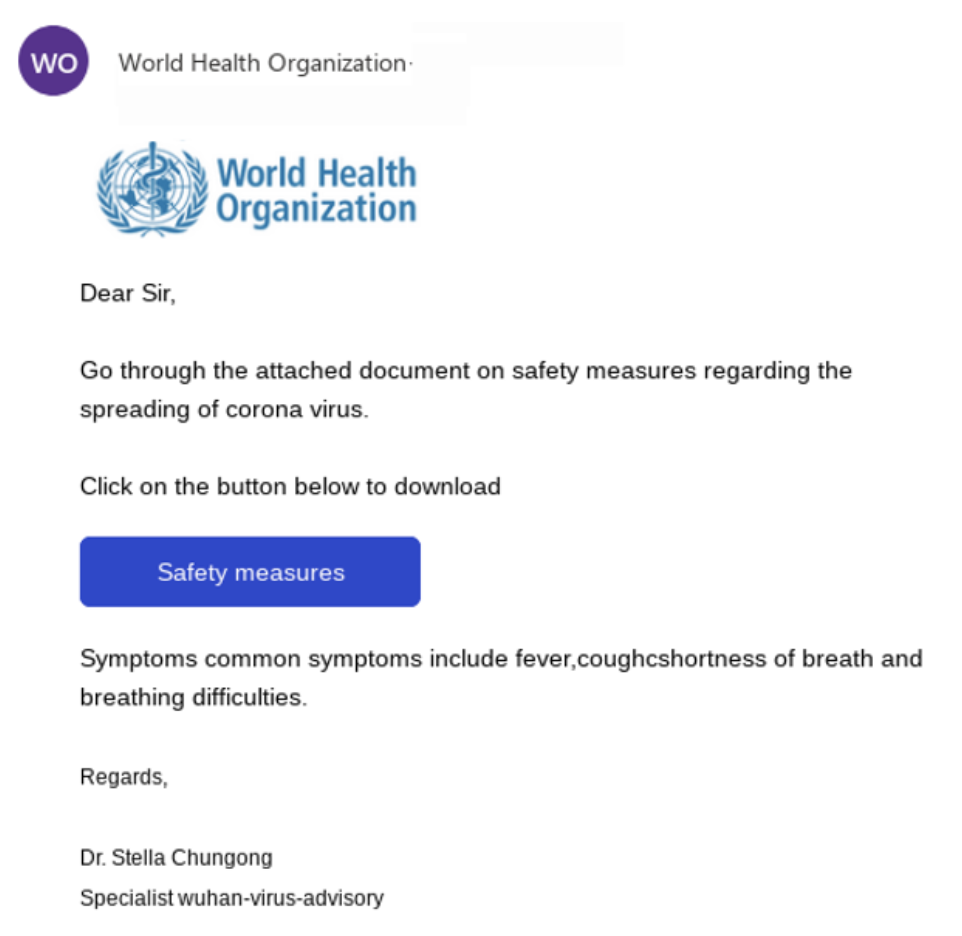
Here's another WHO example:
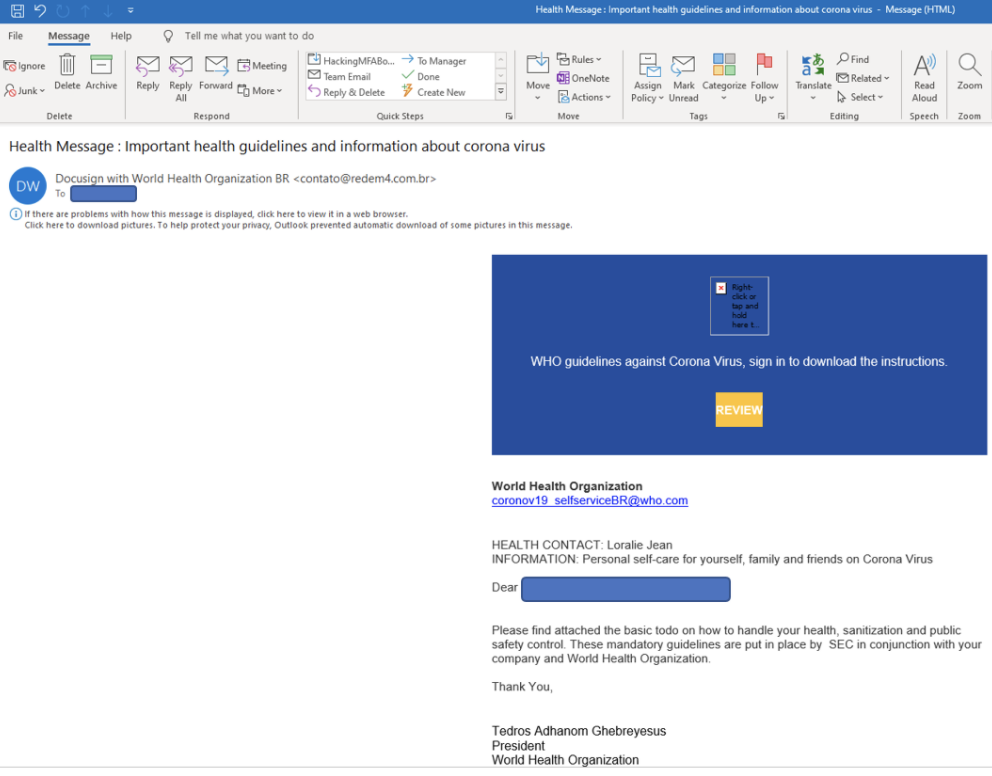
I wonder if the real WHO has ever used the phrase “todo” in a real email to help people? I’m guessing not.
Accessing Relief Funds
Everyone who’s hurting for money can’t wait for a little government relief. Phishers have sent out tens of millions of fake, “Here’s your COVID-19 funds!” emails (see example below), including before the government had actually approved any funding. Why let the fact that the law hasn’t been passed yet stop a good scam?
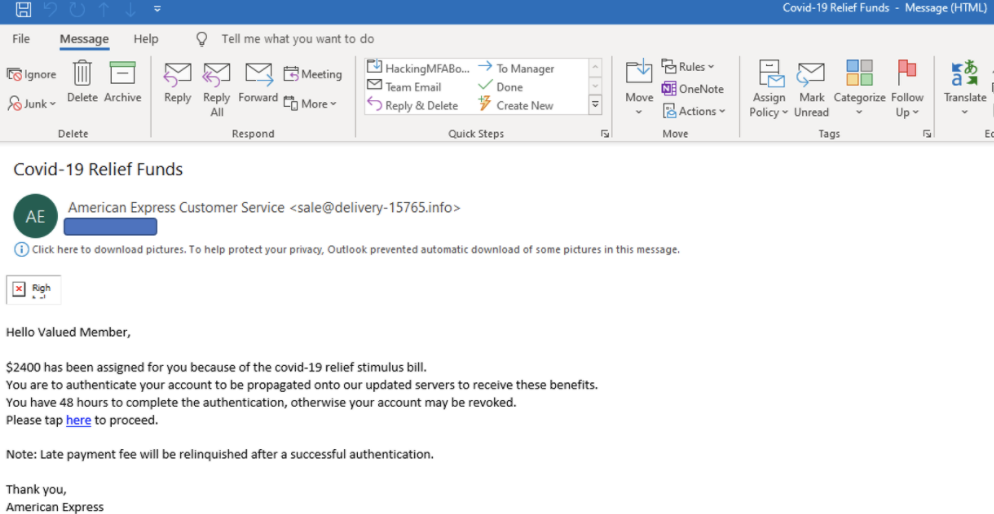
The big signs of mischievousness include why American Express would be delivering U.S. government funds in the first place when the checks are coming from the U.S. Treasury department or why Amex would be sending an email from a .info domain? But I’m sure there is some small percentage of potential victims who fall for this type of trap.
Fake Infection Maps
A bunch of COVID-19 phishes including URL links to purported, but fraudulent, COVID-19 spread/infection maps. The links to the maps end up delivering malicious executable code and scripting instead. In the example below, the user is being offered a bogus link to open up a fake infection map, which is really just a malicious Java application. You can see in the email message that the potential victim’s email client did not support Java (lucky for them).
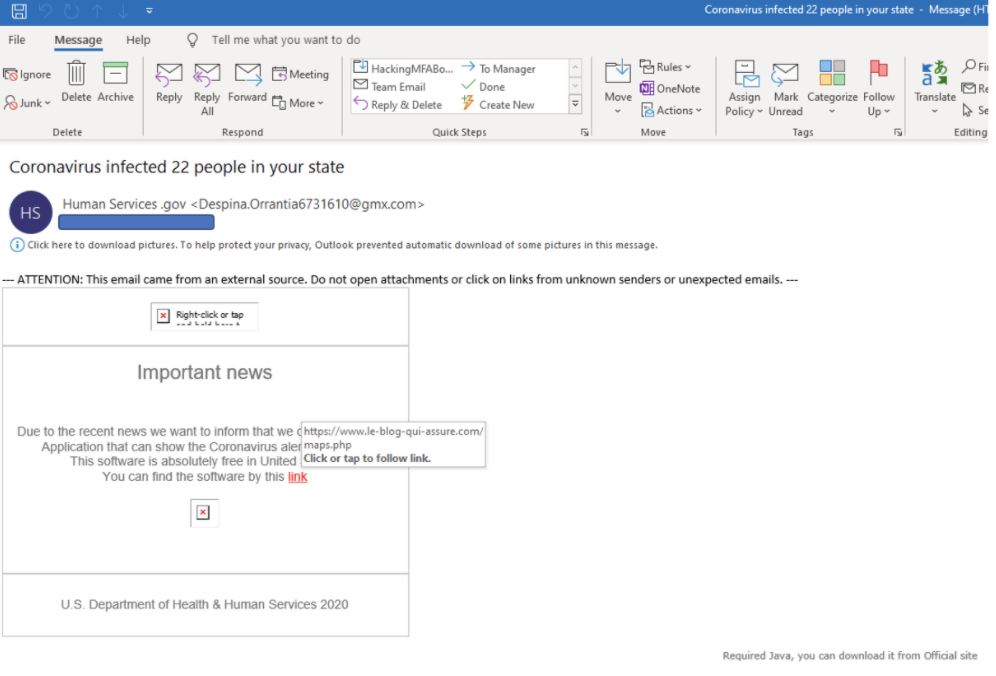
Here’s another example of a ploy to get someone to click on a link to a fake infection map.
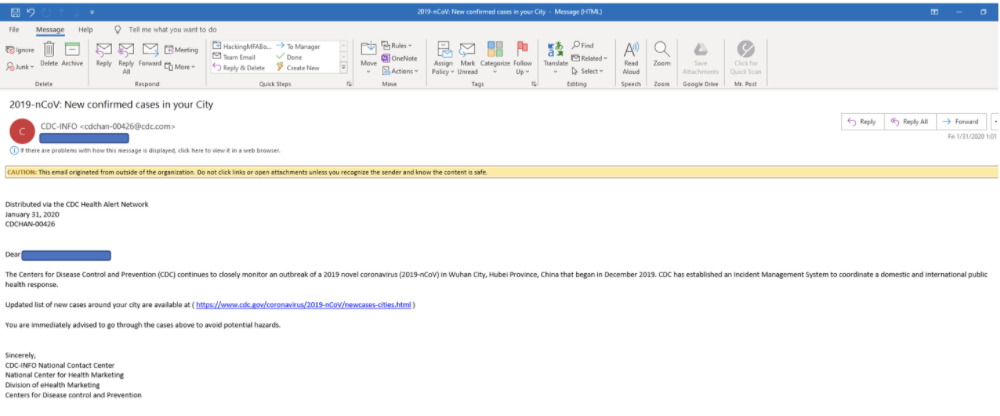
Emails from the CDC
The Centers for Disease Control and Prevention (CDC) is one of the most respected U.S. government agencies for disseminating official information about the coronavirus pandemic status and response. But the CDC rarely sends out mass emails to the general public. In fact, I haven’t seen one official email from the CDC, but I have seen tons of fake CDC emails. So, if you receive an email from the CDC about COVID-19, it’s highly suspect. KnowBe4’s real-time phishing statistics revealed that CDC-related emails were the second most common clicked on email subject in Q1 2020.
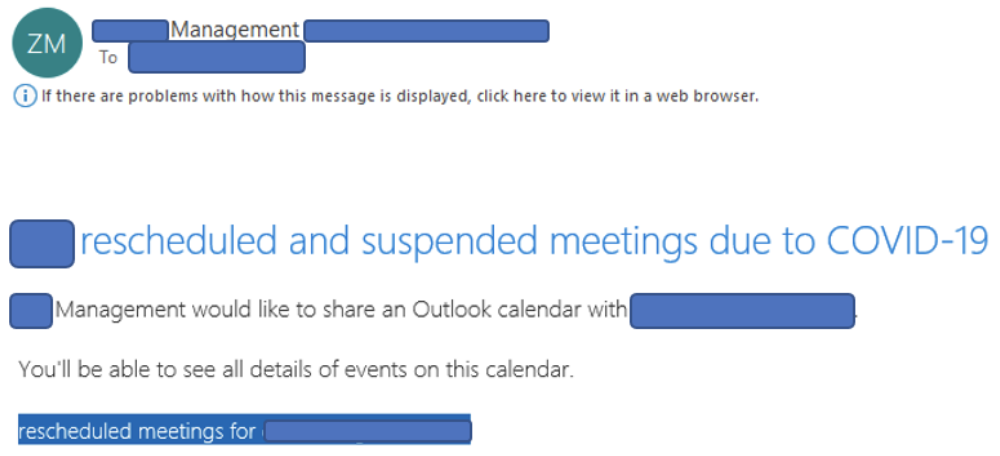
Three of the other most popular phishing email subjects spotted in-the-wild during the same period were:
- List of Rescheduled Meetings Due to COVID-19
- SharePoint: Coronavirus (COVID-19) Tax Cut Document
- Confidential Information on COVID-19
Here’s an example of fake rescheduled meetings.
Fake Contactless Delivery Notices
Although I don’t have a graphical example, a lot of phishers are sending emails claiming to be from a shipping company (e.g., FedEx, UPS, etc.) explaining that they could not deliver a package to someone because of the new “contactless” delivery procedures. They ask the potential victim to click on a link to complete the delivery.
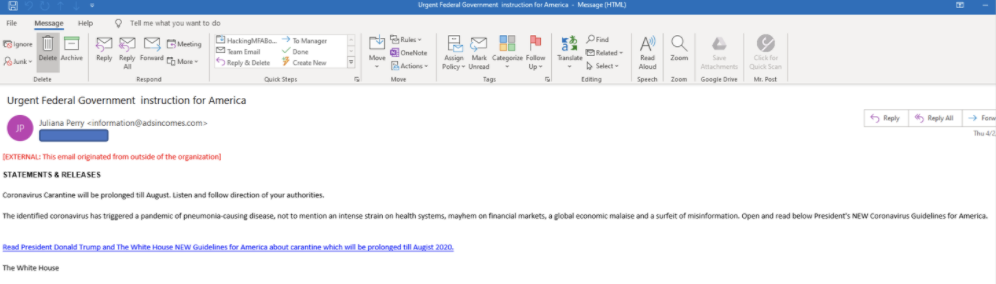
Emails Explicitly Avoiding Using the Words COVID-19 or Coronavirus
Phishers know that computer security defenders are on the lookout for fake emails with subject lines referring to COVID-19 or coronavirus, so they will intentionally avoid using those exact terms while still referring to them indirectly. Here’s an example that ended up in my inbox, which used the phrase “current situation” instead of coronavirus or COVID-19.
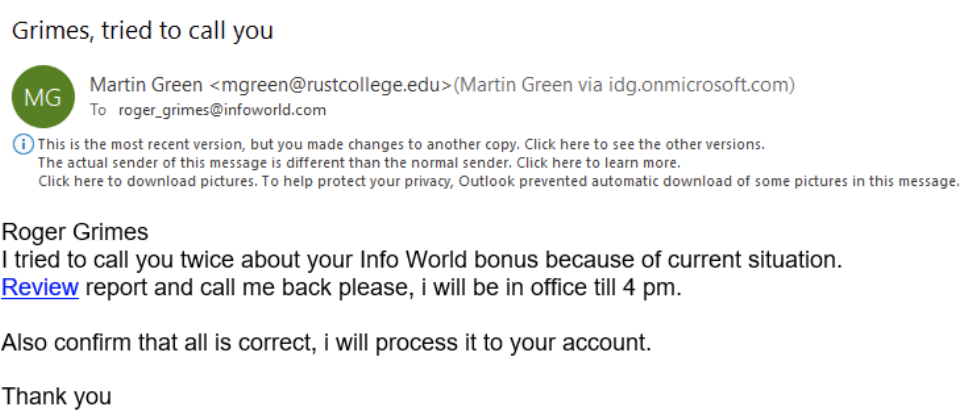
Although I used to work for InfoWorld (until December 2019), I don’t know Martin Green and I’m not sure why any official working for InfoWorld would be sending email from “Rust College” and why that “Rust College” account would be sending from a Microsoft 0365 domain instead of rustcollege.edu. All these are signs of “disjointed branding”, which is highly correlated to phishing emails (and not legitimate emails).
When I hovered over the related link, I got this URL:
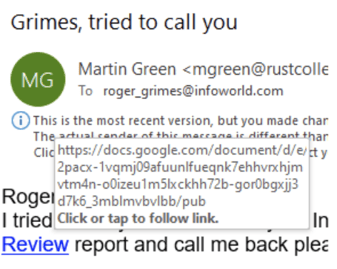
It led to a Google docs link, which no doubt leads to a document which contained malicious links or scripting.
Focus on Shelter in Place Brands
Always be aware of phishers increasing the focus on brands that will increase in popularity during the pandemic, such as Netflix and Zoom. For example, this KnowBe4 blog story details how over 639 fraudulent domains have been registered with the word Netflix in them. Those will no doubt mostly end up as fake Netflix login pages to capture real Netflix login information and credit card numbers.
Normal Misspellings and Grammar Issues
And yes, COVID-19 phishers misspell words just as much as normal phishers. In the example below, they misspell the English word quarantine as carantine.
Smishing
Let’s not forget all the recent smishing-related COVID-19 alerts (example shown below). The example was widely reported in news media and by law enforcement agencies.

With SMS URL links, what you see is what the link really is. I fired up one of my isolated forensics VMs and went to the URL. It was unresponsive and down. It’s likely that the URL was disabled by computer security responders within hours of being broadcast by the phishers. I wanted to make sure the URL was completely fake and did at one time exist as a real domain. So, I did a Whois lookup query on the domain (see below).
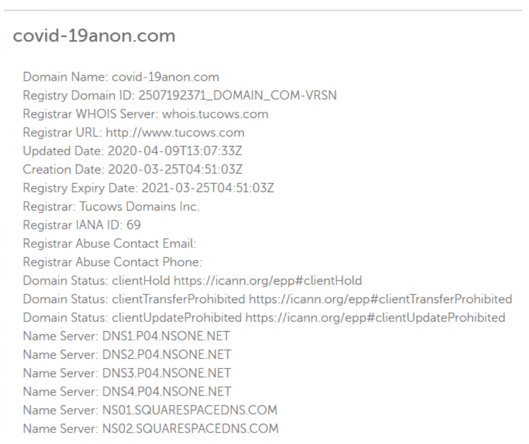
It was created on March 25, 2020, during the pandemic’s peak and updated on April 9th. My best guess is that it was shut down on April 9th. The shutdown was the update. Anytime I come across a relatively new domain, especially in this case, barely a month old, it is highly suspicious.
Summary
There are a lot of coronavirus-related phishing campaigns going on. You can pass this blog article around to your co-workers to help teach them how to avoid some of the most popular types of COVID-19 phishing scams. Make sure you and your co-workers Stop, Look, and Think, before performing a potentially dangerous action. KnowBe4 has prepared some other coronavirus-related resources for you and your co-workers: https://www.knowbe4.com/coronavirus-security-awareness-resources.
 Here's how it works:
Here's how it works:




