 Social engineering and phishing are responsible for 70% to 90% of all malicious breaches , so it’s very important to keep your employees at a heightened state of alert against this type of cyber attack at all times. You want an organizational culture to have a healthy level of skepticism which can spot and report potential phishing attacks before they’ve had a chance to be successful.
Social engineering and phishing are responsible for 70% to 90% of all malicious breaches , so it’s very important to keep your employees at a heightened state of alert against this type of cyber attack at all times. You want an organizational culture to have a healthy level of skepticism which can spot and report potential phishing attacks before they’ve had a chance to be successful.
It can be harder during times of Covid-19 “work-from-home” rules to get employees to pay attention to security awareness training. Different people learn in different ways. Some people like to see videos, others learn the most by reading, and a growing number of people like their education gamified.
I’m a big believer of sending out the occasional email blast as part of a normal training routine which shares up-to-date training. You can select from any of our KnowBe4 blog entries. The blog is updated many times a day with current events. We have some specific COVID-19 resources on the blog most days and dedicated resources.
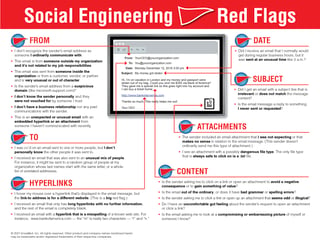
But perhaps the most personally requested single piece of education I get asked for repeatedly after every nearly every webinar I do is KnowBe4’s Red Flags of Social Engineering poster.
Note: It comes in 32 localized languages, but only the English version is free to the public. The other languages require a paid subscription.
The Social Engineering Red Flags PDF lists 22 different signs that anyone can use to investigate an incoming email to see if it is suspicious. It includes common sense things that I think most of us might notice when we open an email. Things like potentially dangerous attachments, grammar issues indicating the sender is not a native language speaker, an unusual request, sent at a strange time, etc. But the PDF puts almost two dozen “red flags” all in one place. It’s a quick, easy read that reinforcements several key signs that might indicate a suspicious email.
Number One Most Suspicious Sign
If I had to pick the most important hint, the single most suspicious red flag to me is a strange-looking hyperlink which does not directly point to a valid, trusted domain; especially if it goes out of its way to fraudulently appear as if it points to a legitimate domain or trusted brand (e.g., microsoftustechsupport@outlook.com, techtalk@google.com.rogueserver.biz, returns.amazon@amazongproducts.ru, etc.). I think teaching people to always hover over ANY URL links and how to recognize bogus links is one of the single best training topics possible. If you can teach this single skill, you’re going to stop a lot of phishing from being successful.
The second most important sign is simply recognizing unexpected requests, which if performed, could lead to something bad. It could be a request to do many different things, including:
- Open and read a document
- Click on a link
- Visit a website
- Provide login credentials
- Process an invoice
- Change banking or payroll information
- Buy gift cards
Stressor Events
Most phishing emails contain a “stressor event”, which is a statement from the sender that if the user doesn’t perform the requested action now, then there will be very negative consequences. For example, the invoice has to be bought now or the important business deal is off; or your password must be verified now otherwise your account will be permanently locked. Train your employees to spot stressor event requests and how they should make them stop, look, and think before acting.
In order for training to be effective, it must be done more than once a year or once a quarter. Ideally, training should be done at least monthly to get the most bang for the buck. We know that security awareness training is best when done at least once a month along with simulated phishing campaigns to test your user’s ability to spot potential phishing emails. Organizations that do this routinely take the percentage of users who will click a phishing email from about one-third or higher to about 5%. That’s a HUGE decrease in risk! You can read more about how to bring down your organization’s own phishing success rate here: https://blog.knowbe4.com/2020-phishing-by-industry-benchmarking-report.
If you haven’t seen or used our Social Engineering Red Flags PDF, I encourage you to download (https://www.knowbe4.com/hubfs/Social-Engineering-Red-Flags.pdf) and distribute.
 Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't one and done. Continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!




