By Eric Howes, KnowBe4 Principal Lab Researcher. If you've been paying attention to the news over the past week or so, you've undoubtedly noticed that the majority of the stories on your preferred news site are now linked to the Coronavirus (aka COVID-19). Unfortunately, ignorance, fear, misinformation, and even malicious disinformation appear to be spreading almost as fast the virus itself -- a turn of events some are now calling an "infodemic."
Put another way, despite our sophisticated computing devices and globe-spanning information networks we seem to be no less vulnerable than previous generations to the very worst of human behavior that tends to rear its ugly head during health crises such as this one. We just happen to do our FUD (fear, uncertainty, doubt) more quickly and efficiently than our parents and grandparents. (Hooray for us.)
Plenty of news outlets have already reported on the rise of coronavirus-related phishing emails. We figured it might be useful to provide a short survey -- with a generous helping of screenshots -- of the virus-themed emails that have been reported to us by customers using the Phish Alert Button (PAB). These run the gamut from ordinary spam attempting to leverage the crisis for quick financial gain to downright dangerous emails designed to exploit fear and ignorance in order to compromise victims' online accounts and install malware.
The Spammers
Unsurprisingly, some of the very first signs of trouble we spotted amongst the emails being shared with us involved plain old spam -- unsolicited commercial email (UCE). These range from the crude and simple spam emails pushing products of unknown or dubious effectiveness...
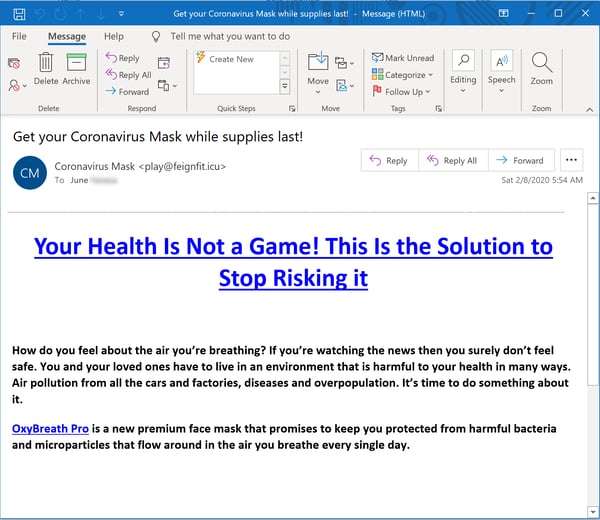
...to more polished emails hawking health products that have quickly become scarce as panic-buying sets in -- esp. medical face masks and hand sanitizers.
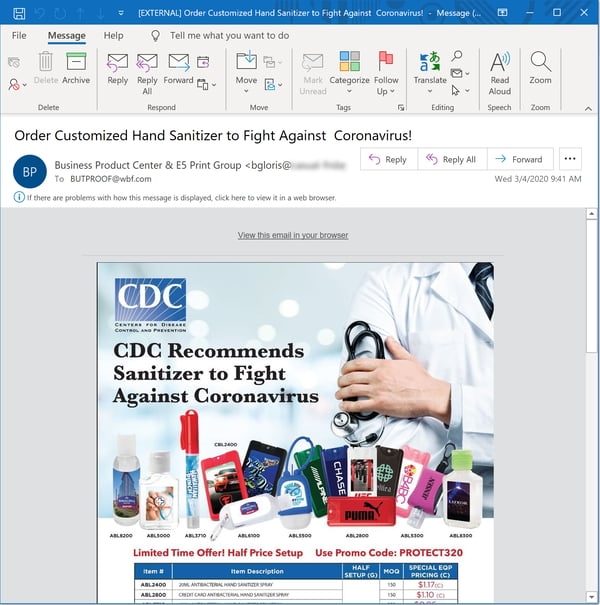
Note the prominent placement of the logo for the CDC (Centers for Disease Control) and the unspoken suggestion that the CDC somehow endorses or approves of this company's offerings.
It's worth noting that your email inbox is hardly the only place where you will encounter this kind of exploitative commercial behavior. Just in the past 24 hours Facebook and Amazon have both announced that they are cracking down on listings and advertising for health products susceptible to price-gouging and other forms of fraud.
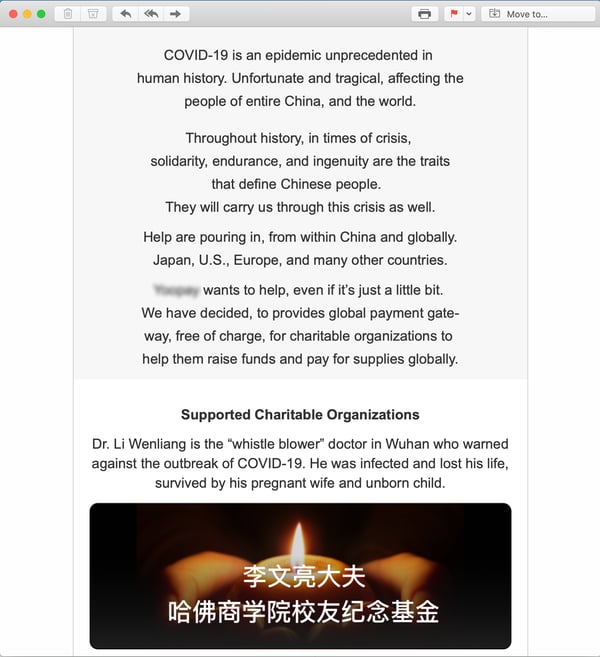
Still other companies have apparently decided that the coronavirus offers the perfect opportunity to stage an online public relations event -- publicized, of course, through spam, as this Chinese online payment processor does by cynically wrapping itself in the mantle of reputable charitable organizations and dead doctors.
The Scammers
Hot on the heels of the spammers are the outright scammers, some of whom are not above dangling the hint of a vaccine for the coronavirus in their spam-driven campaigns pushing medical face masks and other related health products.
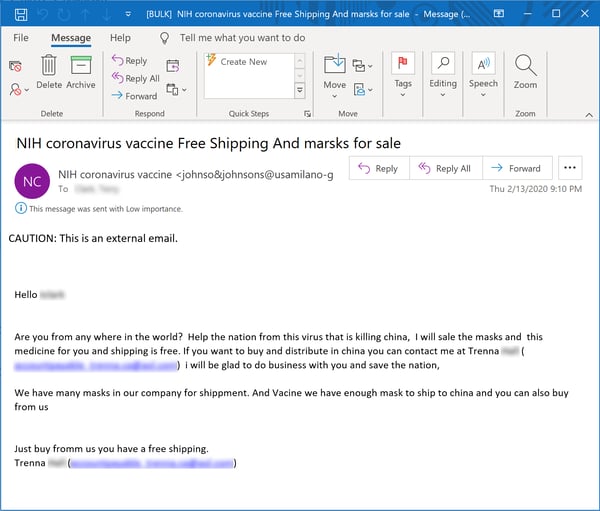
Note how the Subject: line teases a "coronavirus vaccine" to get users' eyeballs on the main body of the email, which appears to be just another low-rent email pushing the usual face masks as well as some poorly described "medicine." Note also how this email drops references to the NIH (National Institutes of Health) as well as Johnson & Johnson, a well-known provider of medical products. No pricing or shipping info is offered (thankfully). We have to wonder, though -- given the shaky state of the English in use here -- whether the party behind this spam fully understands the implications of sprinkling words like "medicine" and "Vacine" (sic) like so much salt and pepper in an email peddling medical face masks to a worried and concerned public.
But why just hint at or tease the commercial availability of a vaccine when you can pose as some kind of medical whiz and brazenly claim to be offering the very thing that actual medical authorities have already stated will not be available -- even under the most optimistic scenarios -- for at least another year?
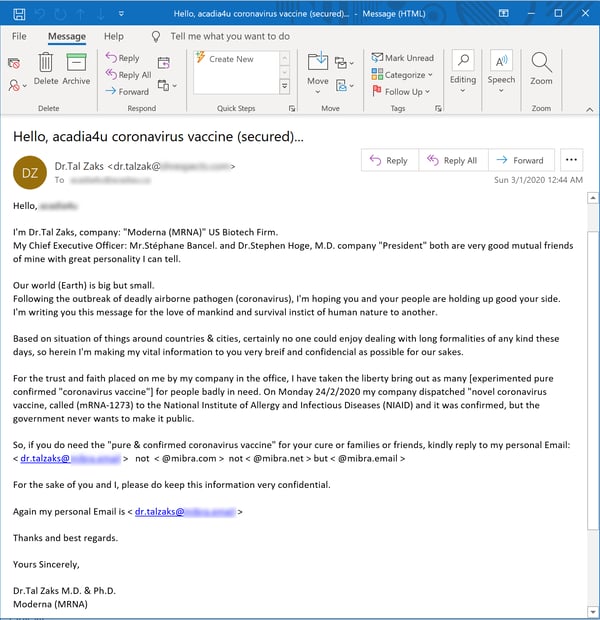
No web link to click on is offered in the above email (again, thankfully), and we haven't attempted to contact whoever is behind it to get the particulars on whatever scam that is undoubtedly being run here on the desperate and gullible among us. (And, no, we wouldn't recommend trying this at home.)
The Bad Guys
Then, of course, there are the folks who make no apologies for what they do: the Bad Guys. As soon as it became apparent that the virus had started to hop borders and threaten populations across the globe, malicious actors began doing what they do best: exploiting fear and ignorance to peddle malware and gain access to the user accounts of paranoid punters keen for information about the virus.
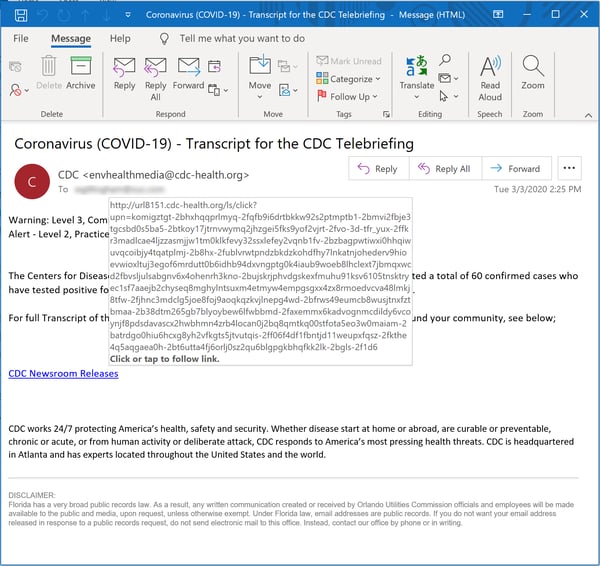
We spotted our very first coronavirus-themed phishing email on Feb. 4 (a date which now seems like several ages ago). Predictably, it went straight for the jugular -- spoofing the CDC...
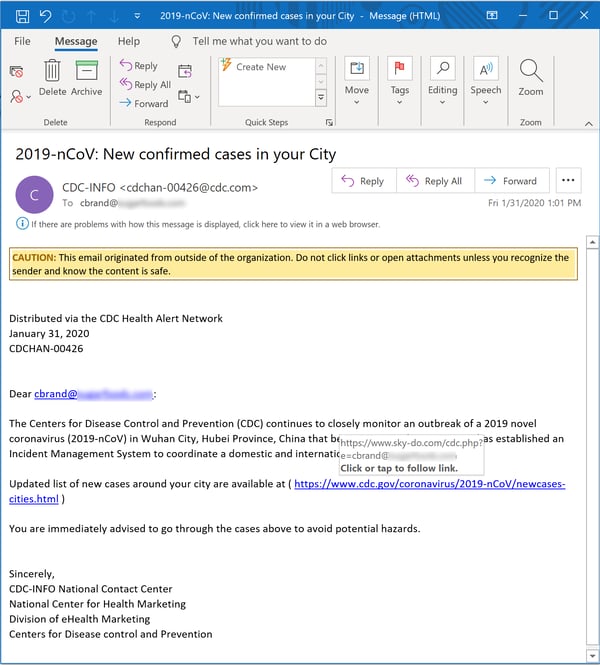
...in an effort to trick users into clicking through to a straight-up credentials phish.
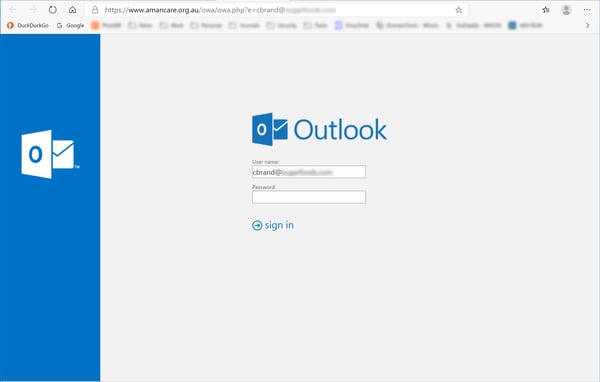
It was an obvious and potentially very effective ruse, leveraging the authority of the CDC in a well-crafted email that reads as if it could have been ripped straight from a press release by the CDC itself.
One month later this campaign is still going strong, with around a half-dozen or so variants of that initial phish -- all spoofing the CDC in order to facilitate the theft of online credentials.
It wasn't long, though, before the bad guys opened a second front in their campaign to exploit the fears and concerns of unwitting users: HR. This shouldn't have been a surprise. Malicious actors have an established track record of spoofing HR departments -- again, leveraging the inherent authority enjoyed by HR within most organizations -- for malicious purposes.
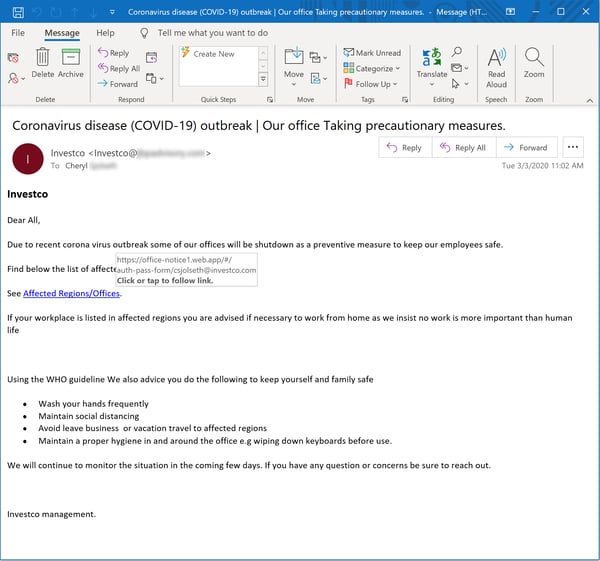
As with the decision to spoof the CDC, this is a smart strategy given that HR departments within many organizations have already been messaging their employees with news and updates about the virus as well as its potential effects on business operations.
As with the earlier CDC-themed phishes, this batch of malicious emails attempts to step users through a credential phish.
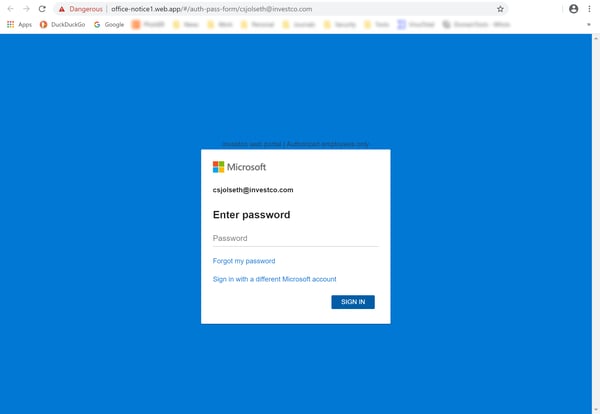
Although credentials phishes have typically been the sine qua non of so many malicious emails over the years, we figured it was only a matter of time before we encountered emails peddling out-and-out malware. Sure enough, just as news organizations began reporting that the number of COVID-19 infections worldwide had sailed north of 100,000, they finally arrived.
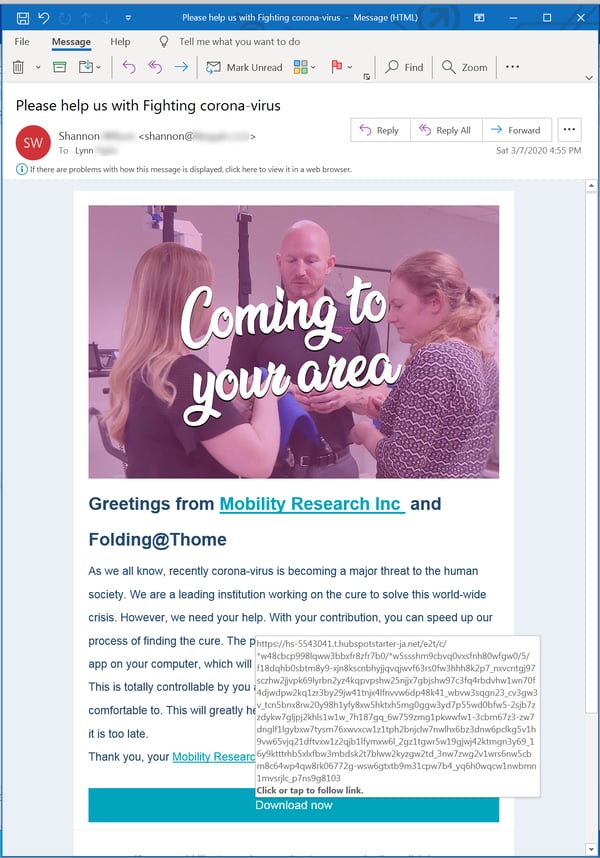
The above employs a rather cleverly designed social engineering scheme that changes up the usual strategy for motivating clicks. Instead of exploiting users' fear and ignorance, this one appeals to their more charitable instincts -- inviting readers to participate in some kind of distributed computing effort to find a "cure" by downloading and installing a software program on their machines.
Anyone installing this software will not be finding aliens, Bitcoin, or even the coronavirus itself. Oh, no. For their selfless efforts unsuspecting users will instead be installing a curiously named trojan horse (foldingathomeapp.exe) that is currently flagged by less than half the engines on VirusTotal.
The End of the World as We Know It
One might think that bad guys pushing malware would be as low as it could go. Not so, unfortunately.
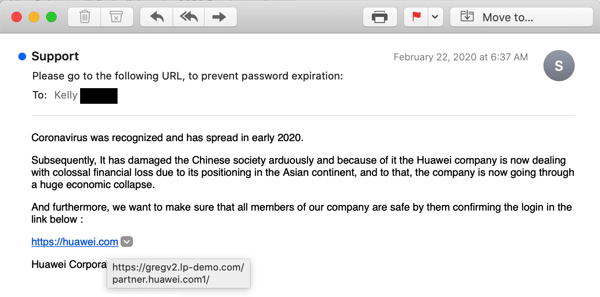
Peddling fake vaccines and malicious software was bad enough. The above, however, goes nuclear in its efforts to manipulate users into clicking a malicious link -- invoking not only the unraveling of Chinese society but the financial collapse of one of the country's more successful (and controversial) high-tech companies: Huawei.
And for what?
We're still not quite sure, as the landing page for the embedded link had already been been taken down by the time we checked it. Given the dire context provided by the email body, it sure looks like it could be another credentials phish. Somehow, though, the alarmist tone of this malicious email would seem to suggest something more serious -- and devious.
Conclusion
In reviewing the rising tide of spam and phishing emails following in the wake of the coronavirus as it spreads around the world, we are struck by a bit of succinctly-put advice from John Oliver about the proper way for handling yourself in the midst of this health crisis: "Don't be complacent, and don't be an idiot."
What does that mean?
It means, first and foremost, paying attention, staying informed, and taking the precautions recommended by recognized medical authorities. It also means, though, that one should avoid trading in FUD -- fear, uncertainty, and doubt -- which only makes the crisis worse and could put the health and lives of real people at risk.
And, finally, if you're working in IT, it means educating your employees about the kinds of malicious emails that are undoubtedly already landing in their inboxes and teaching them to spot and handle these emails correctly, lest your users end up opening the door for malicious actors to their own endpoint machines as well as your organization's wider network.
You can also check out our coronavirus phishing and security awareness resources to help keep your network secure while users are working from home.
 The Training Preview includes:
The Training Preview includes:
