It was all over the news. A server outage at a major newspaper publishing company on Saturday that prevented the distribution of many leading U.S. newspapers, including the Wall Street Journal, New York Times, Los Angeles Times, Chicago Tribune and Baltimore Sun.
An unnamed source revealed they found files with a . RYK extension, and it looks like this was a targeted ransomware attack using the specialized Ryuk ransomware family. This strain is the latest incarnation of the earlier HERMES ransomware which is attributed to the capable and active Lazarus Group that operates out of a Chinese city just north from North Korea and reportedly controlled by the N.K. Unit 180 spy agency.
Unlike spray-and-pray ransomware, Ryuk is mainly used for tailored attacks and its encryption scheme is specifically built for focused infections, such that only crucial assets and resources are encrypted in each targeted network, carried out manually by the attackers.
Reality Check: "It Is Very Hard To Keep A State-sponsored Bad Actor Out Of Your Network"
Security experts believe that the Ryuk crew targets and penetrates selected companies one at a time—charging exceptionally large ransoms—either via spear-phishing, RDP connections, or other yet unknown penetration techniques. Ryuk is not decryptable at the time of this writing, and it is very hard to keep a determined state-sponsored "Advanced Persistent Threat" bad actor out of your network.
The publisher said in a statement Saturday that: “the personal data of our subscribers, online users, and advertising clients has not been compromised. We apologize for any inconvenience and thank our readers and advertising partners for their patience as we investigate the situation.”
Any organization today needs to apply defense-in-depth, and have weapons-grade backup procedures in place to restore production systems that have been compromised. I'm sure that exactly this is happening there, while they get back online. Also could mean they decided not to pay the ransom, good for them.
Ryuk-HERMES Similarities Are Clear As Daylight
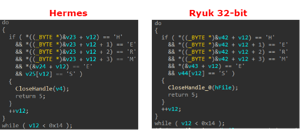
The connections are pretty obvious, shown by Check Point researchers which recently analyzed the two ransomware strains. They pointed at clear similarities between past Hermes strains and current Ryuk samples, which share large chunks of code:
- The function that encrypts a single file is almost identical
- Ryuk and Hermes use the same file marker for encrypted files
- The check for the file marker is also identical
- Both whitelist similar folders (e.g. “Ahnlab”, “Microsoft”, “$Recycle.Bin” etc.)
- Both write a batch script named “window.bat” in the same path
- Both used a similar script to delete shadow volumes and backup files
Ryuk versions for 32-bit and 64-bit systems were discovered, suggesting the ransomware can infect all types of systems, new and old alike. But there are also some differences. The main one is that Ryuk comes with a huge list of apps and services it shuts down before infecting a victim's systems.
"The ransomware will kill more than 40 processes and stop more than 180 services by executing taskkill and net stop on a list of predefined service and process names," Check Point researchers explained in a report. This is one nasty piece of malware.
Now, having said all that, I admit it is early days and this attribution is more a gut-feel estimate than something proven by forensics. There are a lot of "false flag" operations going on, and someone else may have gotten hold of that code. I'll keep this story updated.
[UPDATE 1/12/2019] McAfee casts doubt on Ryuk ransomware connection to North Korea
Security researchers with McAfee have released a report in which they argue that the recent Ryuk ransomware attack on Tribune Publishing Co., which disrupted the distribution of various major US newspapers, was not carried out by North Korean hackers, as various media outlets have claimed. According to the report, the threat actors | (Read More)
How Vulnerable Is Your Network When An APT Has Penetrated Your Systems?
Want to find out if your endpoint security software will block ransomware strains like Ryuk?
Bad guys are constantly coming out with new malware versions to evade detection. That’s why we’ve updated our Ransomware Simulated tool “RanSim” to include a new cryptomining scenario!
This new cryptomining scenario simulates a Monero cryptocurrency-mining operation on the local machine. Monero mining is the most popular cryptocurrency mined by real-world malware and takes a lot of CPU and GPU cycles to process the data necessary to generate the currencies.
Try KnowBe4’s NEW Ransomware Simulator tool and get a quick look at the effectiveness of your existing network protection against the latest threats.
RanSim will simulate 13 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 14 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complementary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Don't like to click on redirected buttons? Copy and paste this link into your browser:
https://info.knowbe4.com/ransomware-simulator-tool-1
Image credits: Check Point