Ransomware continues to be a successfull business for the cybercriminals of the world. It can easily get past even the best anti-virus software through a user just clicking once on malicious ads, or links and attachments in phishing emails.
Once the hacker has access to your network, your files are locked up and held ransom. Often the only way to get them back is to pay the criminals in Bitcoin, their currency of choice.
8 On Your Side Tampa interviewed KnowBe4 Founder and CEO Stu Sjouwerman to get his take on ransomware. See the full interview here:
“They’re making boatloads of money. This is a very successful criminal business model,” Sjouwerman. He admits it’s a huge problem for businesses in Tampa Bay, but individuals can be targets too. While PC users are more vulnerable, hackers recently successfully targeted Mac computers.
“It’s very evil,” said James Ullery, President of LEDtampa.
Ullery's company fell victim to Ransomware last year. Once files were encrypted they had to pay the ransom (one Bitcoin, around $500 right now) within 12 hours, or the ransom would increase.
“$500 we felt was far less expensive than the inconvenience of losing your data,” Ullery admits he paid the ransom.
Most of the time, ransomware hackers will give victims their information back once they pay.
“If their reputation was, these guys don’t give you your files back, they would stop making money,” said Sjouwerman.
If you fall victim, one way to keep from paying hackers is to wipe out your computer’s hard drive and reinstall the operating system. Another way to avoid paying is if you have full backups ASIDE from the infected network.
“You need weapons grade backups, even if you’re just on your own, at the house,” he said.
LEDtampa did have backups, but they weren’t current so they paid. The company now performs full weekly backups for fear this could happen again.
“It makes you feel somewhat violated, like somebody snuck into your house or your business and they took something that belonged to you,” Ullery said.
ABC Action News also interviewed Ullery, more about this story here.
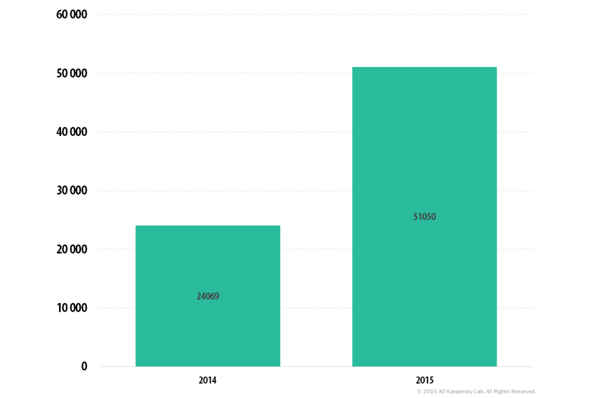
Ransomware continues to grow in infection numbers as well as different types. The trend for cybercriminals has them focusing more on businesses, since the likelihood of getting a larger sum of money per attempt is much greater than from individuals. Kaspersky (a Russian antivirus company) detected ransomware on over 50,000 computers in 2015, more than double the 24,000 from 2014.
Just today we wrote about 3 newer strains making recent headlines: Maktub uses social engineering tactics to both encrypt and compress files, which can all be done offline. PETYA completely locks users out by overwriting the Master Boot Record (MBR) rather than simply encrypting certain files. PowerWare is a fileless ransomware written in Windows PowerShell aimed at enterprises such as health care organizations.
Experts agree the best defense against ransomware is prevention. Proper security awareness training given to all employees could have prevented LEDtampa from being attacked. Users are truly the most important part in maintaining network security. Of course if the unthinkable happens you should always report it to the FBI's Internet Crime Complaint Center (IC3).
Get the most informative and complete ransomware hostage rescue manual.
This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with ransomware.

