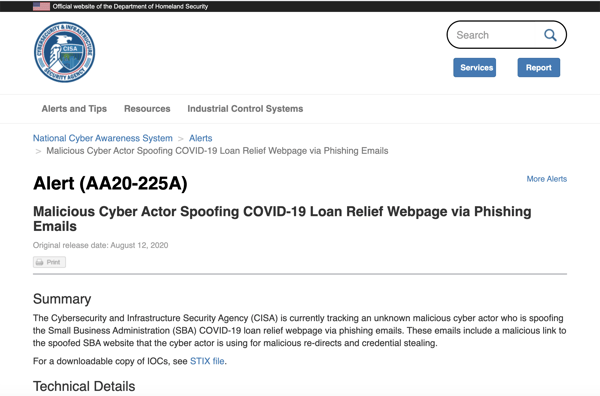
 On Wednesday August 12 the Dept. of Homeland Security issued an alert concerning a phishing campaign using malicious spoofs of the Small Business Administration's (SBA) web site.
On Wednesday August 12 the Dept. of Homeland Security issued an alert concerning a phishing campaign using malicious spoofs of the Small Business Administration's (SBA) web site.
The phishing campaign in question is in fact the same one we reported and documented several days earlier in a blog post.
As we noted, this is a extremely polished campaign that leads with a malicious email almost indistinguishable from actual emails from the SBA. That email announces that the recipient's application for an SBA loan or grant has been approved and provides a link for users to click to obtain more information: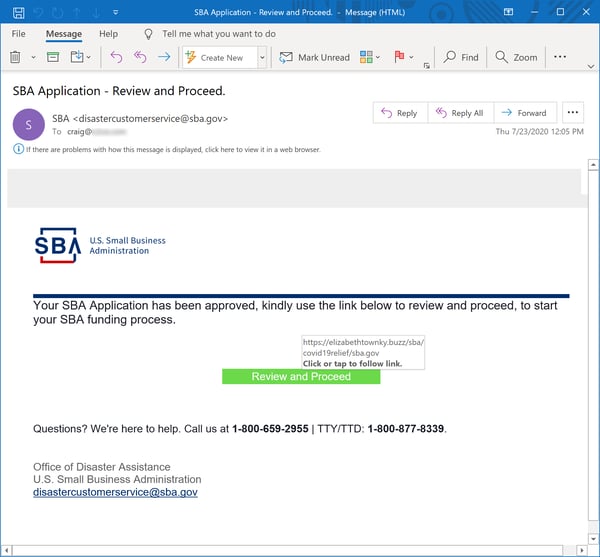
That link takes potential marks to an equally well-spoofed copy of the SBA's login page: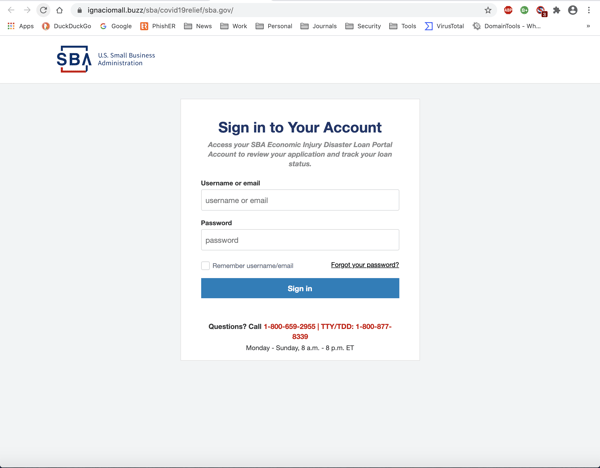
Users who input their credentials will in fact be handing over control of their SBA accounts to malicious actors. SBA accounts contain a variety of exploitable information about applicant organizations, including sensitive bank account information.
With access to an organization's SBA account, malicious actors could conceivably hijack or redirect loan or grant funds to bank accounts controlled by said malicious actors. They could also exploit information in that account for still further fraudulent ends.
The Dept. of Homeland Security's alert contains additional technical information about this phishing campaign as well as recommendations mitigating the threat.
This kind of sophisticated, well-crafted phishing campaign is precisely the reason organizations should be stepping their users through New-school Security Awareness Training and testing them regularly with high quality simulated phishing emails. Your users -- including those in senior positions within your organization -- are your last line of defense.
Well-trained, security-conscious users on the alert for phishing campaigns such as this one are may be the only thing that stands between you and financial disaster during these challenging and precarious economic conditions.
 Here's how it works:
Here's how it works:
