 By Eric Howes, KnowBe4 Principal Lab Researcher. The COVID-19 pandemic continues to dominate news headlines as well as the development of malicious email attacks designed to separate users and organizations from their money. Among the more persistent social engineering schemes we've seen deployed by malicious actors are phishing emails that exploit the several financial programs offered by the U.S. federal government to provide monetary relief in one form or another to individuals, businesses, and other organizations.
By Eric Howes, KnowBe4 Principal Lab Researcher. The COVID-19 pandemic continues to dominate news headlines as well as the development of malicious email attacks designed to separate users and organizations from their money. Among the more persistent social engineering schemes we've seen deployed by malicious actors are phishing emails that exploit the several financial programs offered by the U.S. federal government to provide monetary relief in one form or another to individuals, businesses, and other organizations.
These social engineering schemes first popped up back in March and early April during the initial surge of coronavirus-themed phishing emails, and they've been with us ever since. Although some of these malicious emails have targeted businesses and organizations, most of the "COVID-19 Relief" phishes reported to us by customers using the Phish Alert Button (PAB) have been clearly aimed at individual users concerned about their own personal financial situation.
Over the past two weeks, however, we've spotted some interesting and dangerous new variations on this basic phishing attack.
The Development of "COIVD-19 Relief" Phishing
The majority of "COVID-19 Relief" phishing emails reported to us target individual users by employing the oldest trick in the book: the offer of free money. Here's a fairly typical example:
As with the above email, these individually-targeted "COVID-19 Relief" schemes typically invoke a well-known brand or authority to lend credence (of some sort) to the monetary dangle. In addition to the WHO (World Health Organization) we've seen the bad guys spoof the IRS: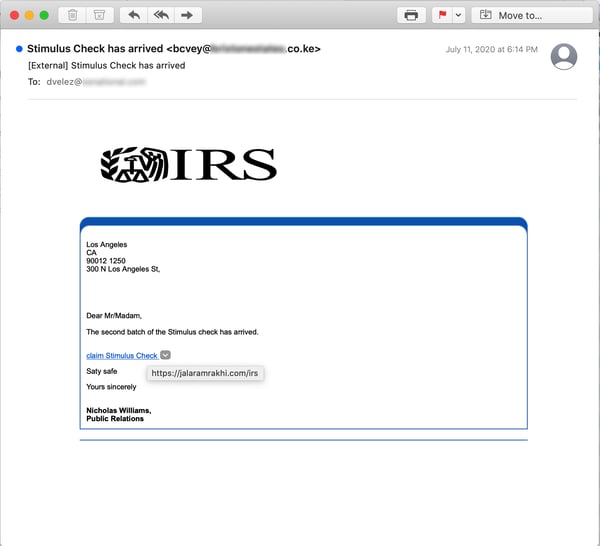
...Microsoft: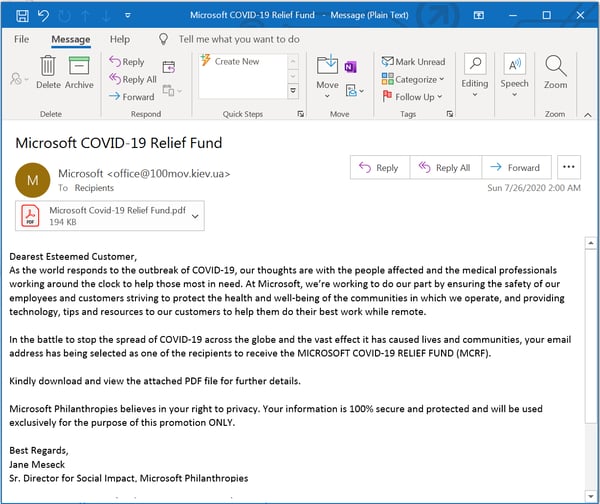
...the UN: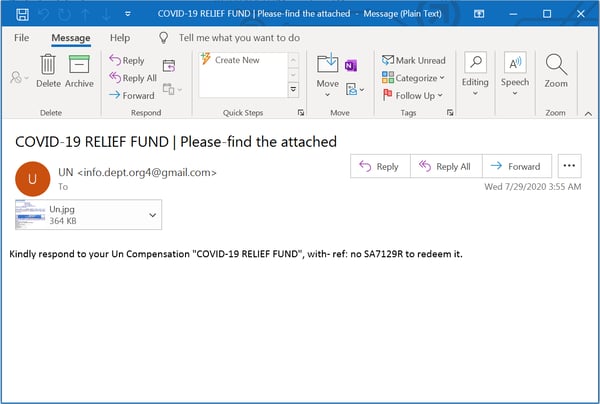
...as well as the Gates Foundation: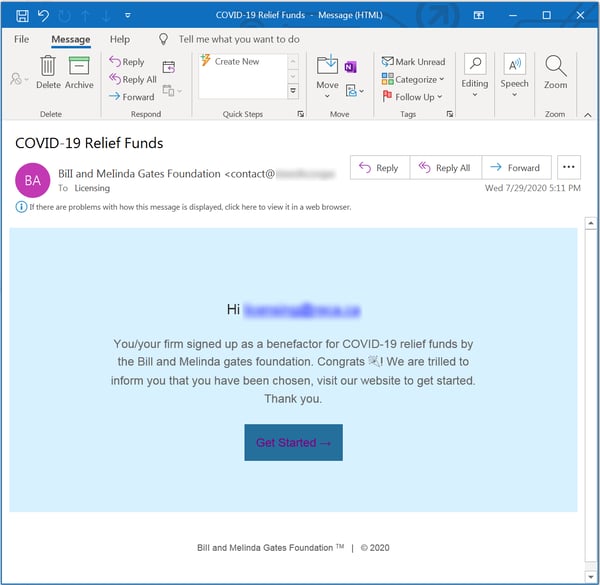
If there have been been similar runs of malicious emails invoking the IMF (International Monetary Fund), the CDC (Centers of Disease Control), or Google, we aren't aware of them. We wouldn't, however, be surprised to learn of their existence, as all of these organizations have proven to be popular with malicious actors looking to establish credibility with end users.
As you might expect, the majority of these individually-targeted emails lead to malware installations or credentials phishes, though some appear to be classic "advance fee" fraud schemes.
Businesses and organizations have also been targeted by fraudsters, though.
As reported by mainstream media, enterprising fraud artists have set their sight on businesses that might have an interest in pursuing in one of the several financial relief programs offered by the Small Business Administration (SBA), the best known of which is the Paycheck Protection Program (PPP). To no one's surprise, these programs have been beset by fraud, much of it involving fake or bogus offers to facilitate loans for cash-strapped businesses and organizations.
Malicious actors who ply their trade through phishing emails, however, have used the SBA for somewhat different purposes: as bait for social engineering schemes that trick recipients into clicking through to credentials phishes and malware installs -- the usual end game for malicious actors attempting to breach corporate networks.
This fairly typical phish spoofs the SBA to dangle a document with information about the approval status for an SBA-backed loan in front of small business owners. 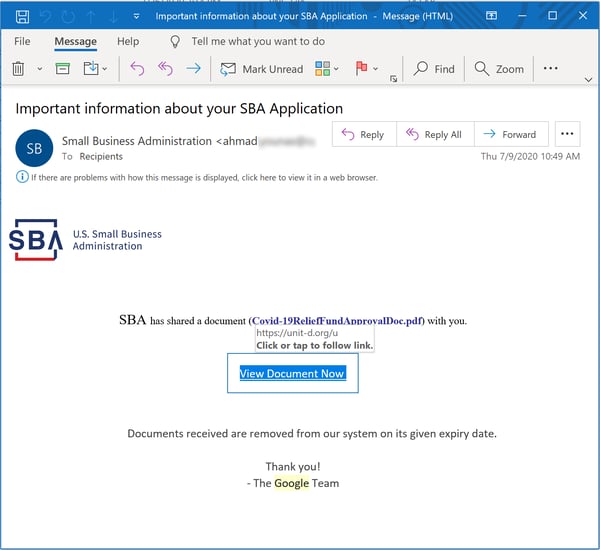
Although the SBA's now familiar logo appears, the email is, curiously enough, signed by "The Google Team." There is no document, of course - only credentials phish:
Other SBA-spoofs deliver malware, however.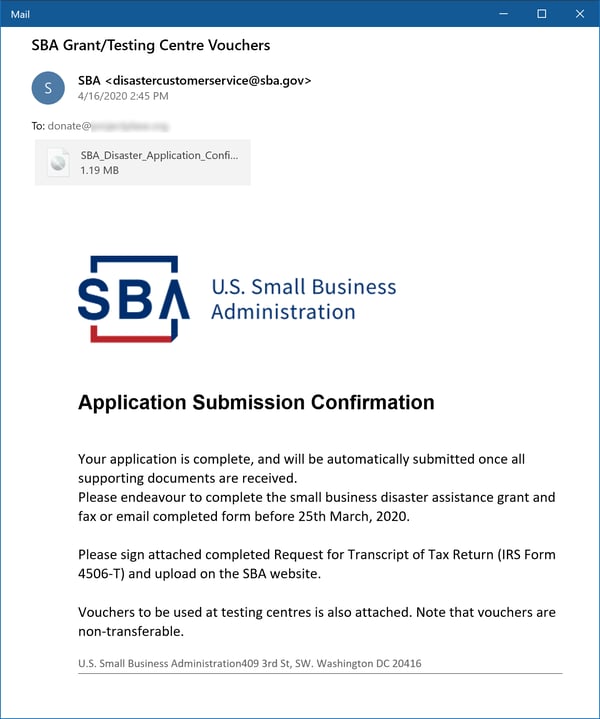
Note the attached .IMG file -- an image file format similar to .ISO files that is increasingly popular with malicious actors -- which in turn yields a malicious executable, itself a trojan dropper.
Although direct spoofs of the SBA are common enough, plenty of other malicious emails spoof the SBA via proxy -- offering up purported documentation or information from the SBA via a trusted intermediary. Take for example this phish, which spoofs Docusign (though not very well) as well as the SBA: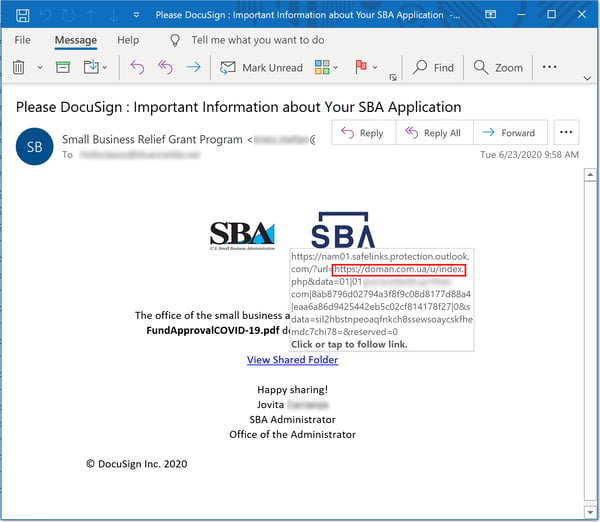
...and takes unwitting clickers to the usual credentials phish: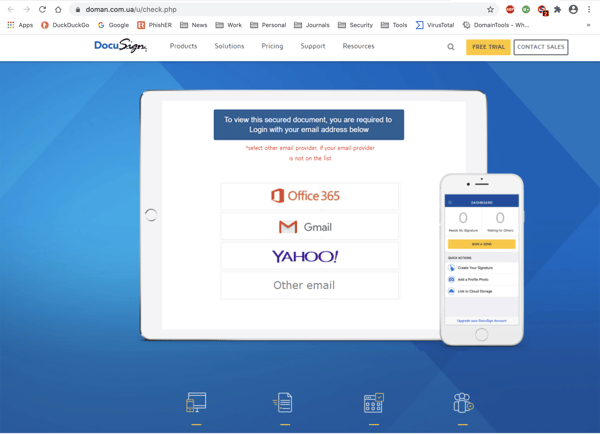
Malicious actors who prosecute this particular social engineering scheme are perfectly capable of using legitimate online services to deliver their malicious emails instead of just spoofing them (as in the fake Docusign email above). Although this next example spoofs Bank of America, it is delivered through Sendgrid, a well-known email service provider: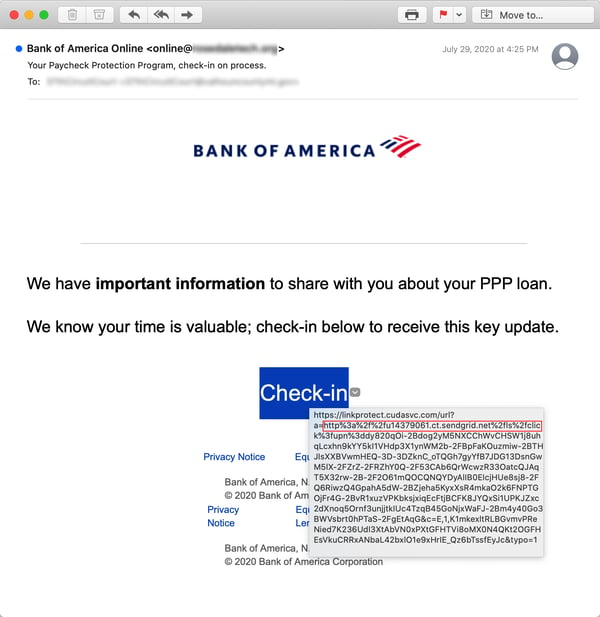
Another popular vehicle for delivering malicious SBA-themed phishing emails is Dropbox: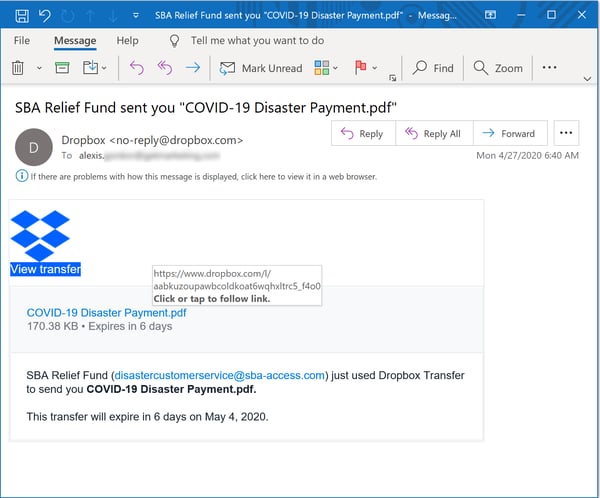
Note the bogus email address provided for the SBA towards the bottom of the email body.
Often the bad guys don't even bother spoofing an intermediary, however, electing instead to present users with some kind of PPP-related document: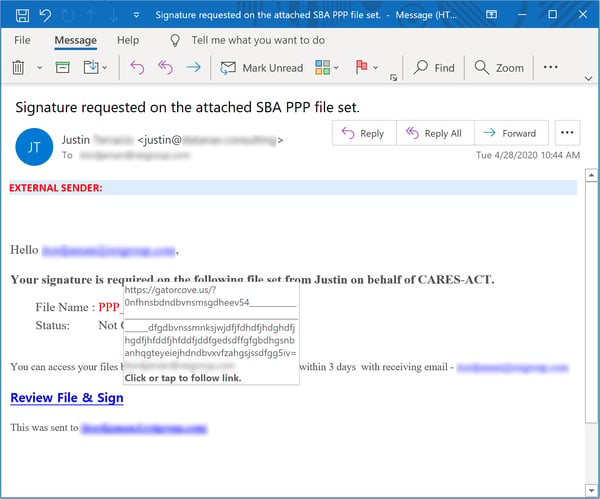
One might doubt the effectiveness of this kind of bare-bones phish, but when business owners are cash-strapped and looking into a financial abyss basic good judgement often goes out the window.
Meet the New Phish, Same as the Old Phish
As noted earlier, the vast majority of these "COVID-19 Relief" phishing emails -- whether targeted at individuals or organizations -- have pursued the usual end game for malicious actors: credentials phishes, malware installs, and "advance fee" fraud schemes.
Over the past few weeks, however, customers using the Phish Alert Button (PAB) have reported an interesting and alarming variation on the SBA-themed social engineering scheme targeted at businesses and organizations. Let's take a look.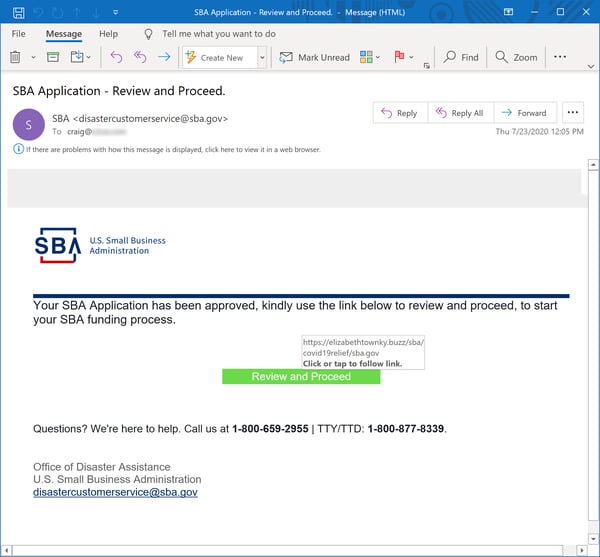
This is a convincing, high-quality spoof of the SBA -- a clear cut above any of the previous emails we've looked at here. For comparison, here's a legitimate email from the SBA:
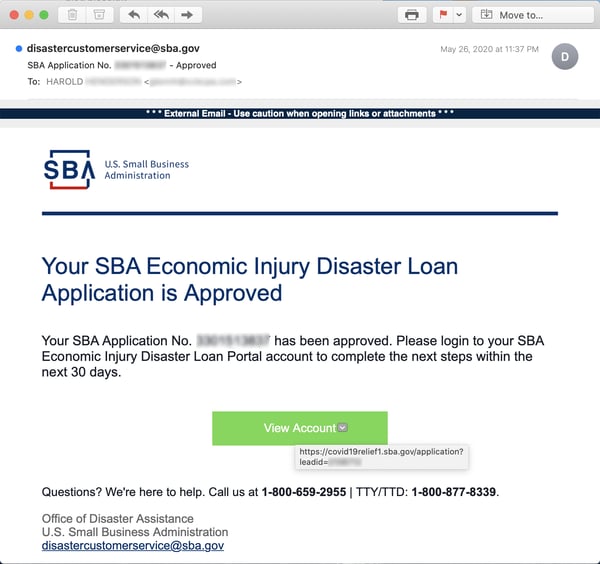
About the only thing that gives the con away here is the link -- provided the recipient bothers to check it.
This particular phish leads to an equally well-spoofed fake login page for the SBA: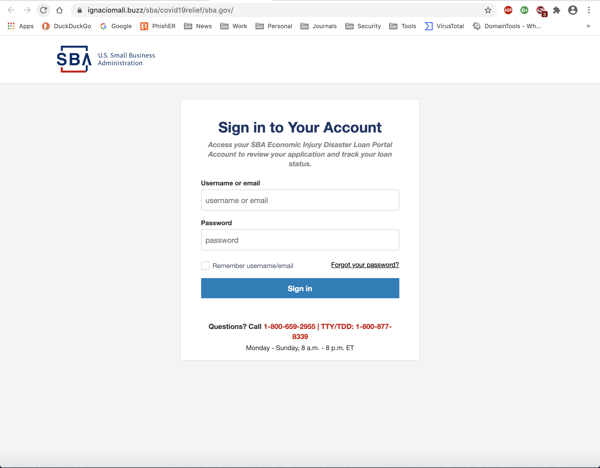
Again, for comparison purposes, here's the real SBA login page.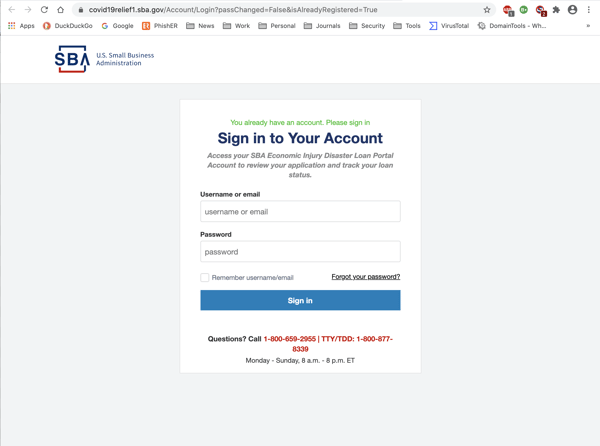
That's right. The bad guys are going after the SBA accounts of businesses and other organizations who have applied for one of the several types loans and grants available through the SBA.
Such accounts are particularly lucrative inasmuch as they offer the bad guys a wealth of exploitable information about businesses and organizations as well as a prime opportunity to re-route funds intended for those legitimate organizations:
Your typical SBA account contains valuable data about applicant organizations, including:
- legal name of business
- business address
- phone number
- business tax id
It also contains a gold mine of banking information, including:
- bank name
- account number
- routing number
- checking account
- business name, phone number, street address, & tax id on the account
Note that in its instructions to loan/grant applicants the SBA explicitly advises those organizations to ensure that the bank account provided is properly set up to receive ACH payments.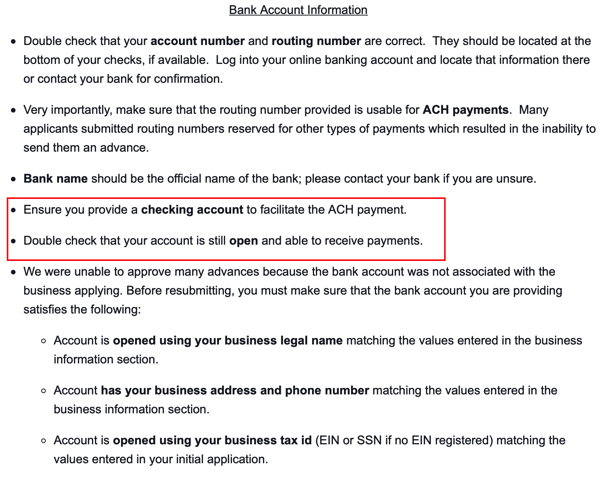
Even if the bad guys don't manage to snatch loans or grants intended for a legitimate organization, there are plenty of other opportunities available to exploit the information in that organization's SBA account.
In many ways, this particular phish is a "return to roots" for malicious actors. Remember: the current plague of phishing emails got its start back around 2004 - 2005 with simple, straightforward spoofs of popular banks designed to trick users into coughing up credentials for their online banking accounts.
This latest SBA-themed phishing campaign amounts to the same thing. And it could prove potentially devastating to businesses and organizations already on the ropes in this virus-ravaged economy.
Conclusion
The COVID-19 pandemic has damaged businesses, organizations, and individuals -- pushing many to the brink of insolvency. It has also provided malicious actors with a wealth of opportunities to develop social engineering schemes designed to facilitate fraud of one sort or another.
With your users working from home and your senior executives undoubtedly consumed with keeping your organization afloat, it is imperative -- now more than ever -- that you get those employees trained to spot and handle malicious phishing emails. That means stepping them through New-school Security Awareness Training and testing them regularly with simulated phishing emails like the real ones we've looked at here.
And keep in mind that this kind of training is critical not just for the lowly cubicle dwellers in your organization but for the senior-most members of your organization as well -- the very folks who might be targeted with the kinds of sophisticated SBA-themed phishing emails documented above. To do anything less simply courts catastrophe.
 Here's how it works:
Here's how it works:
