Do you know how big your email attack surface really is? Open Source Intelligence (OSINT) is the collection of information from public sources on the Internet that both red teams and bad guys can use for phishing attacks.
A good IT security best practice to address the ongoing problem of social engineering using OSINT is to do quarterly email attack surface checks and find out what info about your users is out there.

Source: Gemalto
Find out which of your users' emails are exposed before the bad guys do.
Many of the email addresses and identities of your organization are exposed on the internet and easy to find for cybercriminals. With that email attack surface, they can launch social engineering, spear phishing and ransomware attacks on your organization.
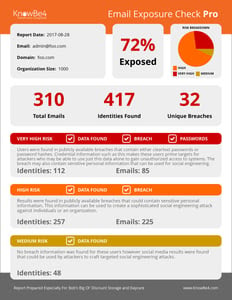
Our NEW Email Exposure Check Pro (EEC) identifies the at-risk users in your organization by crawling business social media information and hundreds of breach databases. This is done in two stages:
First Stage
Does deep web searches to find any publicly available organizational data. This will show you what your organizational structure looks like to an attacker, which they can use to craft targeted spear phishing attacks.
Second Stage
Finds any users that have had their account information exposed in any of several hundred breaches. These users are particularly at-risk because an attacker knows more about that user, up to and including their actual passwords!
Your EEC Pro Reports
We will email you back a summary report PDF of the number of exposed emails, identities and risk levels found. You will also get a link to the full detailed report of actual users found, including breach name and if a password was exposed.
Getting your EEC Pro will only take a few minutes and is often an eye-opening discovery. Get yours now:
https://info.knowbe4.com/email-exposure-check-pro




