These three terms are often a source of confusion, especially in connection with cybercrime and where that comes from.
If you think that search engines like Google (there are more!) know about everything on the internet, you'd be wrong. Some stats from from Worldwidewebsize.com show at the start of November 2017, search engines have indexed at around 4.57 billion pages .
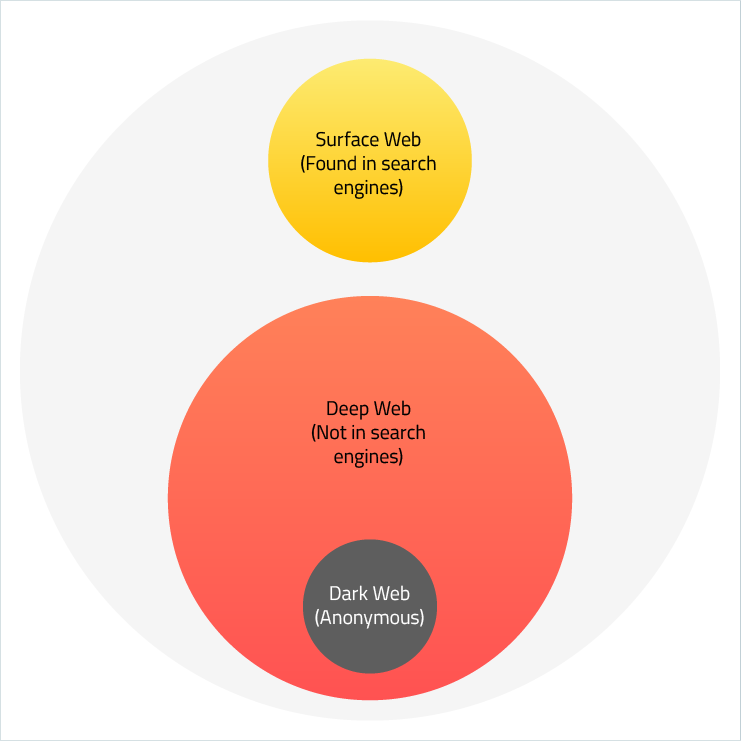
The section of the internet that is being indexed by search engines is known as the “Surface Web” or “Visible Web”. Now, 4.5 billion pages is a lot, but you'd be surprised to know that in reality it's only 10 percent of the whole web. It's the "surf" of the ocean of the whole internet. The reason search engines can see the surface web is through their web crawlers that read the website data, index it, and follow the links. So, what is the 90% that lies under the surface?
Deep Web vs Surface Web
The main difference is that the Surface Web can be indexed, but the Deep Web cannot. You can still access it though. You yourself spend a lot of time in the Deep Web, but you probably do not know it. Deep web site examples are:
- Websites you can only get in with a username and password, like email and cloud service accounts, banking sites, and even subscription-based online media restricted by paywalls
- Companies’ internal networks and various databases
- Education and certain government-related pages
- Dynamic content, coming from a database where the page you see was displayed as a result of a query you put into that page's search box or a form (Crawlers can’t do these things.)
Note that bits and pieces of the data out of the Deep Web may be picked up by search engines in the case of a data breach or targeted attack.
Dark Web vs. Deep Web
At the moment, the Dark Web is defined as a layer of information and pages that you can only get access to through so-called "overlay networks", which run on top of the normal internet and obscure access. You need special software to access the Dark Web because a lot of it is encrypted, and most of the dark web pages are hosted anonymously.
There are several tools used for reaching these parts of the internet. The TOR (The Onion Router) maintains the most popular tool for Dark Web access. Their primary product is the Tor browser. If you think you are completely anonymous though, think again. Law enforcement routinely shuts down and prosecutes sites and people doing illegal things on the Dark Web.
On the Tor network, internet traffic is directed through the network of random relays. The browser builds a route of encrypted connections, one-by-one. Each relay knows only the previous and the next relays, but full connection route stays almost untraceable. The Multiple layers of encryption resemble the structure of an onion.
The Connection Between Dark Web and Cybercrime
Greater anonymity allows cyber criminals to do their thing, and the rise of the Bitcoin cryptocurrency which allows incognito payments, has also contributed to illegal trade.
According to article “Cryptolitik and Dark Net”, published by Thomas Rid and Daniel Moore (King’s College London), out of 2723 active sites found on Tor Dark web during several weeks, 1547 or 56.8 percent contained illicit material of some kind.
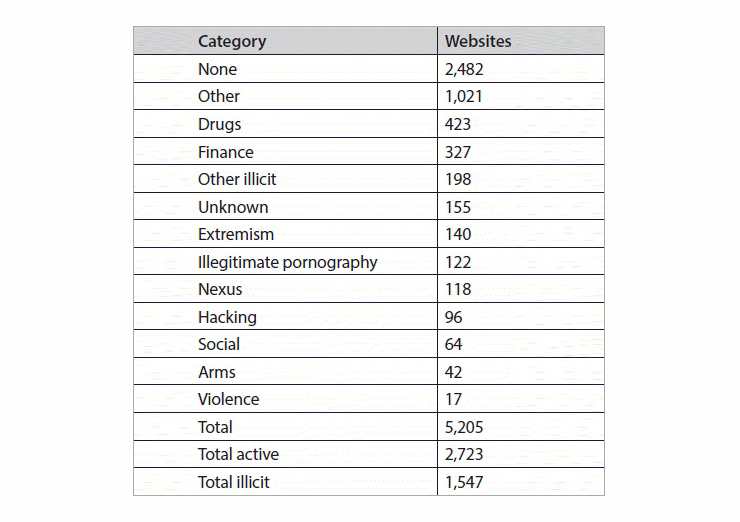
It turns out that a majority of cybercriminals, selling everything from compromised personal and financial data to drugs and hacking tools, constitute over half of Dark Web contents.
The Dark Web is a very convenient venue for cybercrime's underground economy, but you see their social engineering attacks as spear phishing emails in your inbox, and on compromised websites in the Surface Web.
So now you know the difference between the Surface, Deep, and Dark Web!
Grateful acknowledgement to George Paliy.
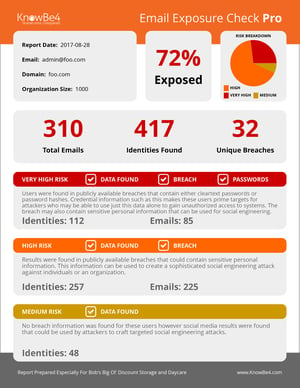 Here's how it works:
Here's how it works:




