OK, finally there is some good news in the fight against ransomware!
In case you did not know, I was the Editor-in-Chief for WServerNews for 15 years, and I have been following the Win OS closely since 1995. Glad to be back on my old stomping grounds for a bit here! (Here are 20 years of archives.)
Microsoft has been closely watching the onslaught of this new ransomware epidemic and added a slew of new features to the second major update of Win10 which is called "Creators Update" — Win 10 CU for short — which has been rolling out since a few weeks ago, consumers first.
Presenting new anti-ransomware protection features added in Win 10 CU, Robert Lefferts, Director of Program Management, Windows Enterprise and Security, said that no Windows 10 customer was affected by the recent WannaCry ransomware outbreak that took place in mid-May and no currently known ransomware strain can infect Windows 10. 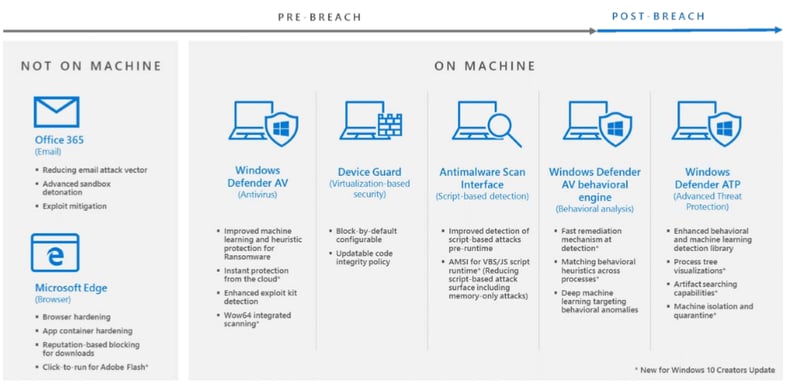
From a security perspective, CU is a massive improvement.
The new security features include the following list, apart from a host of non-security related additions like a 3D version of MS Paint. :-)
- Click-to-run for Adobe Flash in Edge — which prevents ransomware and other malware from landing on Windows 10 PCs via exploits kits and drive-by downloads.
- Instant cloud protection via Windows Defender — According to Microsoft, starting with CU, Windows Defender AV can suspend a suspicious file from running and sync with the cloud protection service to further inspect the file.
- Fast remediation mechanism at detection — Microsoft says it has made great strides to "remediate ransomware infection and limit ransomware activity from minutes to seconds, reducing its damage from hundreds of encrypted files to a few." Microsoft credits this to Windows Defender AV’s behavioral engine, who can aggregate malware behavior across processes and stages.
- Improved detection for script-based attacks — Microsoft says its Antimalware Scan Interface (AMSI) was modified to intervene during the strategic execution points of JS or VBS script runtimes, two infection vectors often used by ransomware.
- Wow64 compatibility scanning — In CU, Windows Defender AV added a process-scanning feature that uses the Wow64 compatibility layer, enabling it to better inspect system interactions of 32-bit applications running on 64-bit operating systems.
- Process tree visualizations — feature added to Windows Defender ATP, the commercial version of Windows Defender.
- Artifact searching capabilities — feature added to Windows Defender ATP.
- Machine isolation and quarantine — feature added to Windows Defender ATP
- Windows Edge browser — better protection against remote code execution attacks
Overall, your average user will probably not notice the difference
Overall, it's good update, but it stands out for its incremental tweaks and behind-the-scenes improvements to matters such as security, updates and privacy, rather than for spectacular new features.
Obviously, you will not be able to roll this out immediately in your organization, despite the CU security improvements. Implementing CU is likely not a priority if you have just started to deploy Win10, and you might jump straight to the next major update, codenamed Redstone 3 which is due later this year.
The update is available to MSDN/TechNet subscribers running the Enterprise, Education and IoT Core edition. Organizations that have Windows via the Volume License Service Center have been able to get the update since May 1.
These Goodies Only Come In The Latest Version
Microsoft has a very good 14-page PDF with all these features detailed and illustrated. You can download that PDF here. It is obvious that they are adding all these features only to the most recent version, giving you an incentive to accelerate your wall-to-wall upgrades to the latest rev of the OS, which in this case you should be looking at seriously.
The whitepaper contains excellent ammo for budget requests, but is too technical for average C-level execs since it talks about data science, machine learning, automation, behavioral analysis, and other exotic subjects like that. :-D

You Need A Full Security Stack, Including Your Human Firewall
Organizations defend their networks on each of the six levels in the green graph you see. End-user Security Awareness Training resides in the outer layer: ‘Policies, Procedures, and Awareness’.
As you see, this is the outer shell and in reality it is where security starts. You don’t open the door for the bad guy to come freely into your building, right?
Here is a short blog post that gives you a quick and admittedly highly simplified look at the rest of the layers of defense-in-depth .
UPDATE: windows 10 actually doesn't stop ransomware. More details here: https://blog.knowbe4.com/windows-10-stops-ransomware-cold-not-so-fast
 Here's how it works:
Here's how it works:




