 So, here is something new...
So, here is something new...
The Register just wrote about the difference between your run-of-the-mill spray-and-pray ransomware infections, and highly targeted manual deployment attacks like the SamSam or Samas attacks that have hit hospitals recently, locking all machines and demand exorbitant ransoms. The attacks are targeted against banking and infrastructure firms worldwide.
Criminal hackers penetrating the network usually start with a spear phishing attack, and then laterally move through the network to get the lay of the land and then lock all machines at the same time with a shock-and-awe effect.
The bad guys time their attack to add pressure
Matt Hillman, a principal security researcher at MWR InfoSecurity, said: "This ransomware is targeted at big organisations because the amount they are prepared to pay is greater. Hackers are timing their attack to add pressure, for example by launching assaults just before sales quarters close or a major announcement or industry event.
Evil Corp hires hackers for targeted attacks
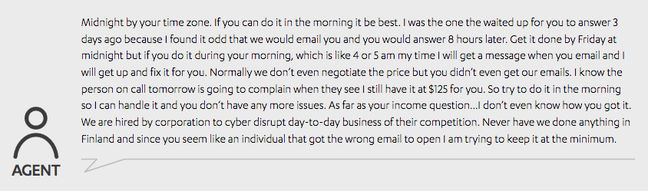
Sean Sullivan, a security advisor at F-Secure, said that its labs uncovered chat sessions in which a ransomware support agent claimed they were hired by a corporation for targeted operations (see page 15 of this PDF). "There was some analysis/metadata that we later used to find another variant which seemed to support that claim," Sullivan toldEl Reg, adding that the follow-up attack targeted IP lawyers and was seemingly aimed at disrupting their business operations.
Here Are 10 Things To Do About It (apart from having weapons-grade backup)
- From here on out with any ransomware infection, wipe the machine and re-image from bare metal
- If you have no Secure Email Gateway (SEG), get one that does URL filtering and make sure it's tuned correctly
- Make sure your endpoints are patched religiously, OS and 3rd Party Apps
- Make sure your endpoints and web-gateway have next-gen, frequently updated (a few hours or shorter) security layers
- Identify users that handle sensitive information and enforce some form of higher-trust authentication (like 2FA)
- Review your internal security Policies and Procedures, specifically related to financial transactions to prevent CEO Fraud
- Check your firewall configuration and make sure no criminal network traffic is allowed out
- Run PCs at least-privilege, use software that blocks ransomware infections
- Work on and improve your network segmentation architecture
- Deploy new-school security awareness training, which includes social engineering via multiple channels, not just email
Since phishing has risen to the #1 malware infection vector, and attacks are getting through your filters too often, getting your users effective security awareness training which includes frequent simulated phishing attacks is a must.
KnowBe4's integrated training and phishing platform allows you to send attachments with Word Docs with macros in them, so you can see which users open the attachments and then enable macros!
See it for yourself and get a live, one-on-one demo.
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:





