
A Florida city is still struggling to recover from a ransomware attack two weeks after the city paid the ransom, according to the New York Times. The attack began after a city employee downloaded a malicious document that arrived in an email.
This document downloaded the Emotet Trojan, which in turn downloaded the Trickbot Trojan. These Trojans were then used to plant the RYUK ransomware within the city’s systems. On June 10th, the ransomware encrypted 16 terabytes (more than 16,000 gigabytes) of information, including more than a century’s worth of digitized municipal records.
A city clerk who has spent years manually scanning these documents for preservation, told the Times that it’s still not clear if everything will be recovered. “It puts us years and years and years behind,” Sikes said.
The victim decided to pay the $460,000 ransom on June 25th after failing to find a workaround. Most of the cost was covered by the city’s insurance provider, with the city paying a $10,000 deductible. Even though the attackers provided the decryption key, the recovery process is taking a very long time.
Mark A. Orlando, the chief technology officer for Raytheon Intelligence Information and Services, told the Times that attackers are improving their targeting to increase the chances that a victim will pay ransom.
“These groups are always trying to find that sweet spot: What is enough someone will consider paying but not so much that they’ll say, ‘Forget that. It’s easier to rebuild,’” Orlando said. “This is a situation where that amount is going up, and we have reached a new high-water mark as to what is getting paid out.”
Organizations need to maintain secure backups, but restoring from backups can be a lengthy and expensive process. Make sure you frequently test your restore procedure!
Ideally, the attackers won’t be able to gain a foothold in the first place. New-school security awareness training can teach your employees how to avoid falling for these attacks.
Brand-New Ransomware Simulator Tool Now with Two New Ransomware Scenarios
The bad guys are continuing to evolve their approach to evading detection. That’s why we’ve updated our Ransomware Simulation tool “RanSim” to include two new ransomware scenarios! 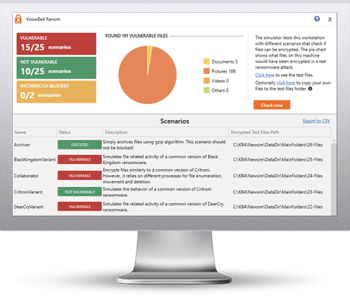
These new scenarios simulate ransomware strains like GandCrab and Rokku that encrypt users’ files and demands a crypto-ransom in exchange for the keys.
GandCrab was a very active ransomware strain all throughout 2018 as well as since the start of 2019, and it is known for requesting up to $3000 from its victims to decode encrypted files. While the creators of GandCrab announced in May they were shutting down their operation, make sure your organization is safe from this type of infection before another group takes it over, or worse, you won’t have an option to decrypt your system!
Try KnowBe4’s NEW Ransomware Simulator version and get a quick look at the effectiveness of your existing network protection against the latest threats. RanSim will simulate 15 ransomware infection scenarios and 1 cryptomining infection scenario to show you if a workstation is vulnerable to infection.
Here's how RanSim works:
- 100% harmless simulation of real ransomware and cryptomining infection scenarios
- Does not use any of your own files
- Tests 16 different types of infection scenarios
- Just download the install and run it
- Results in a few minutes!
This is a complimentary tool and will take you 5 minutes max. RanSim may give you some insights about your endpoint security you never expected!
Download the New RanSim Now:
https://www.knowbe4.com/ransomware-simulator




